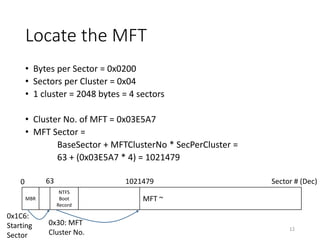
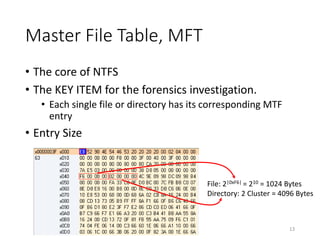
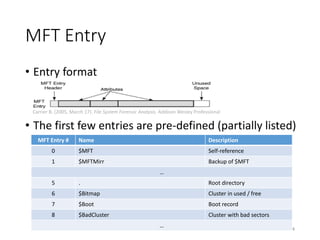
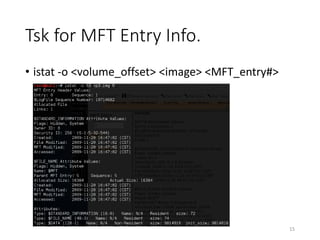
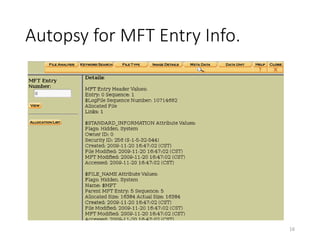
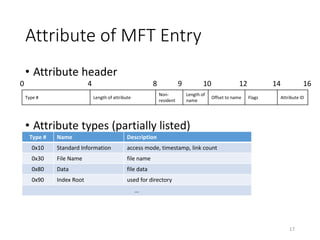
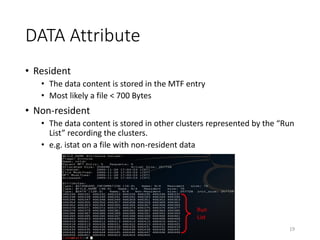
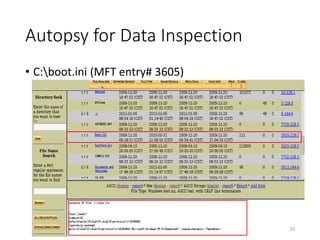
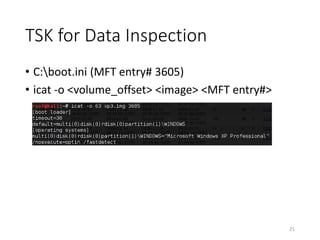
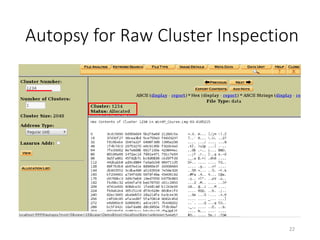
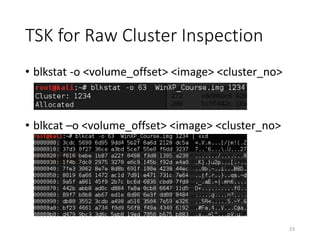
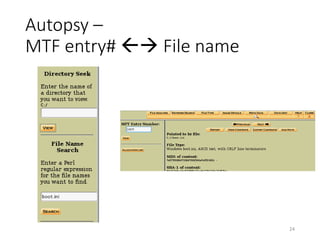
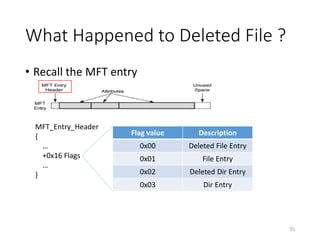
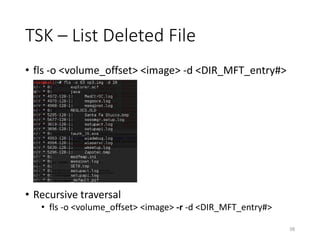
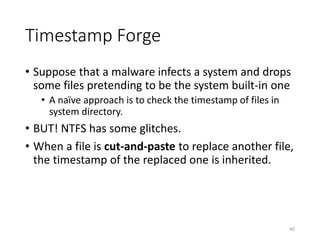
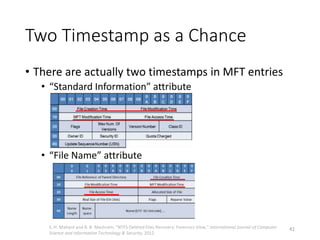
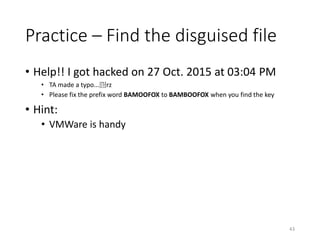
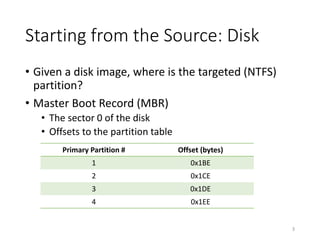
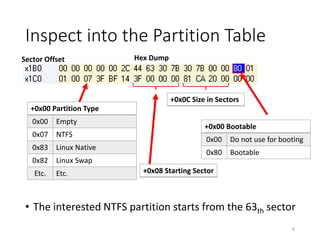
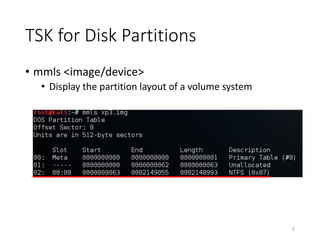
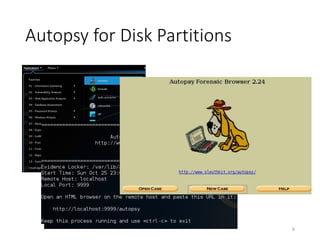
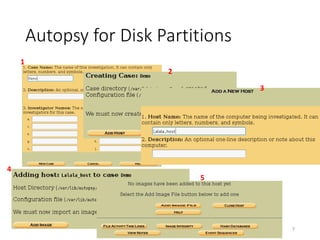
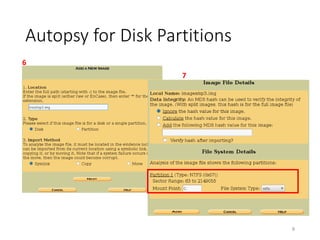
The document provides an overview of disk forensics concepts and tools used for analyzing disk images. It discusses locating the NTFS partition, inspecting the master boot record and partition table. It also covers the NTFS file system structures like the master file table, file attributes, alternate data streams, and methods for recovering deleted files. Timestamp analysis and registry forensics are also briefly introduced. Various forensic tools like The Sleuth Kit, Autopsy, and samdump2 are demonstrated.


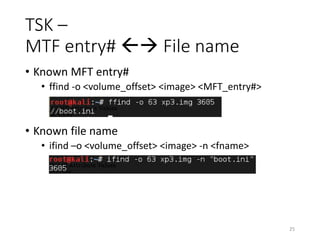
![NTFS Boot Sector @ 63th Sector
10
+0x03OEMID=“NTFS”
+0x54BootstrapCode[426]
+0x0BBytesperSec
+0x0CSecperCluster](https://image.slidesharecdn.com/diskforensics-151105065635-lva1-app6891/85/Disk-forensics-10-320.jpg)
![NTFS Boot Sector @ 63th Sector
11
+0x03OEMID=“NTFS”
+0x54BootstrapCode[426]
+0x0BBytesperSec
+0x0CSecperCluster
+0x30ClusterNo.ofMFT](https://image.slidesharecdn.com/diskforensics-151105065635-lva1-app6891/85/Disk-forensics-11-320.jpg)