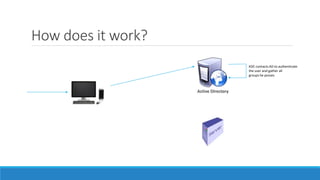
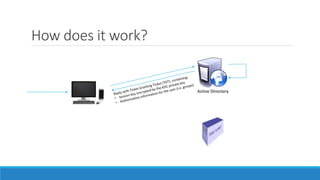
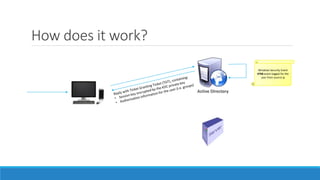
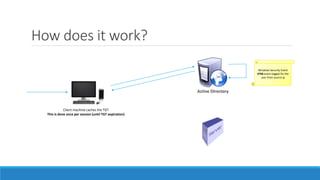
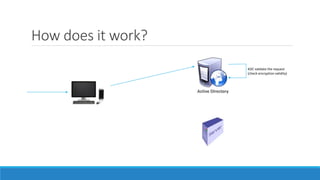
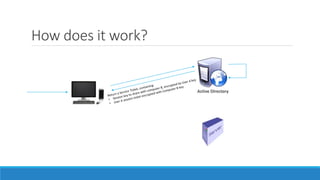
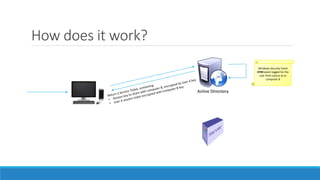
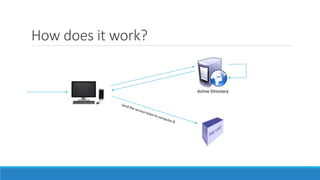
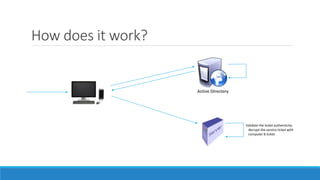
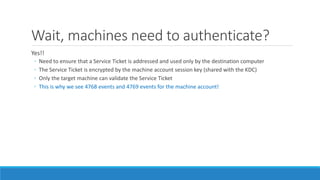
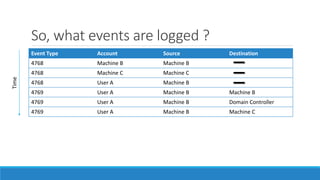
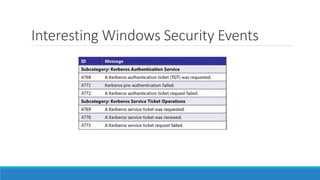
The document discusses the Kerberos authentication protocol. It describes Kerberos as a protocol that uses tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. It also summarizes how Kerberos works, the events it generates, and some of its advanced features like single sign-on, delegation, and cross-domain authentication.