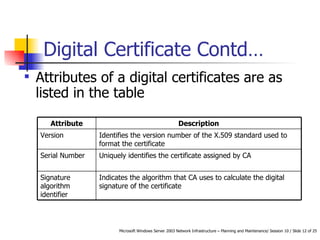
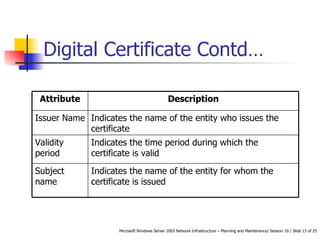
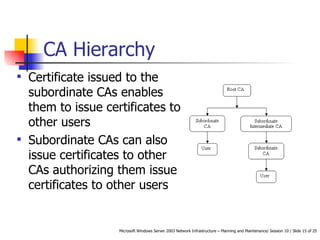
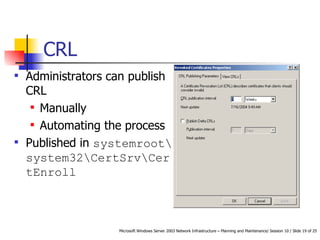
Public Key Infrastructure (PKI) uses public and private key cryptography to authenticate users and devices. Digital certificates, issued by a Certificate Authority (CA), bind a public key to a user's identity. Enterprise CAs issue certificates only to internal users while stand-alone CAs can issue to external users. Active Directory, a Windows directory service, enables single sign-on access to network resources and authenticates external users without an Active Directory account.