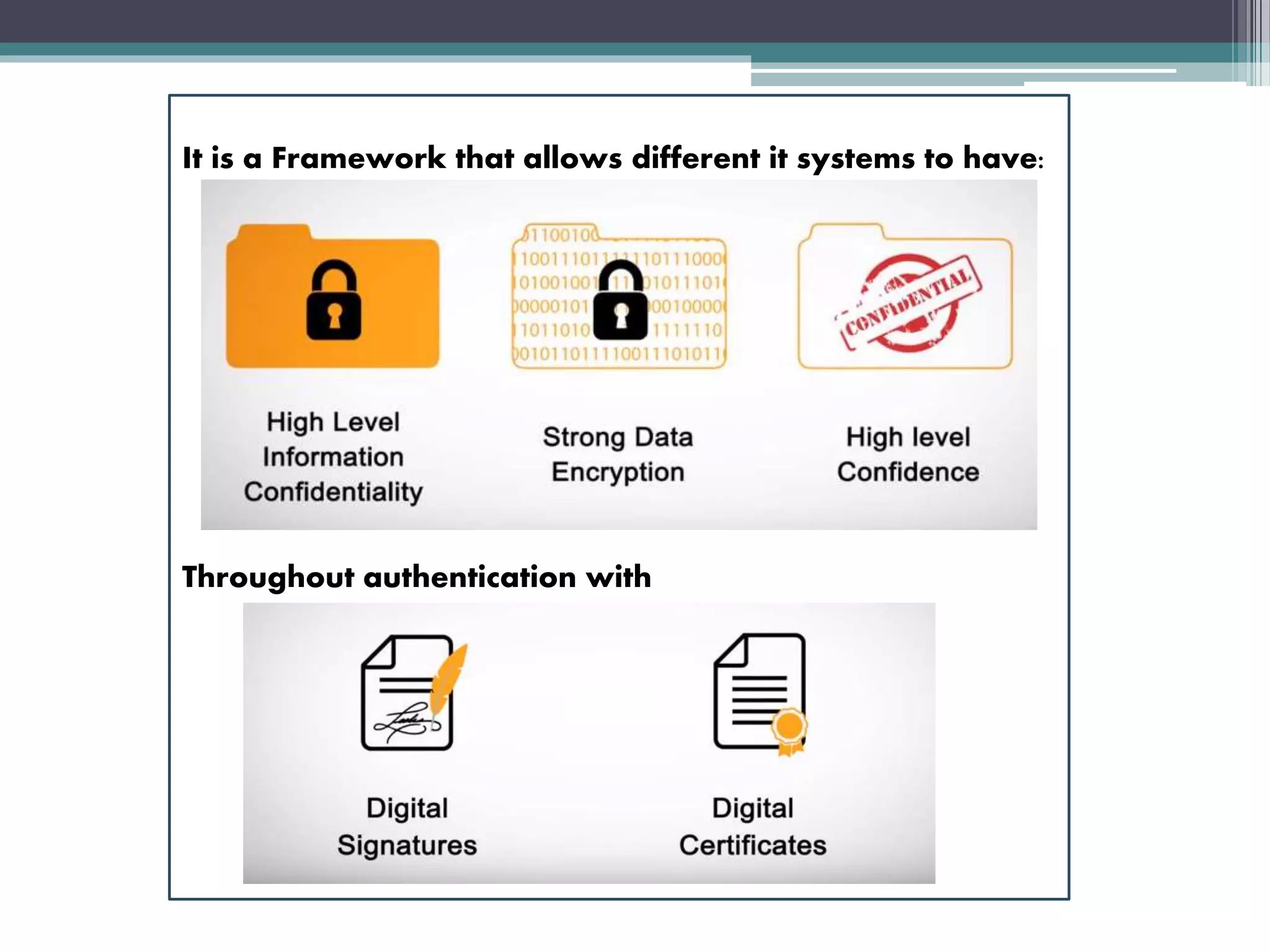
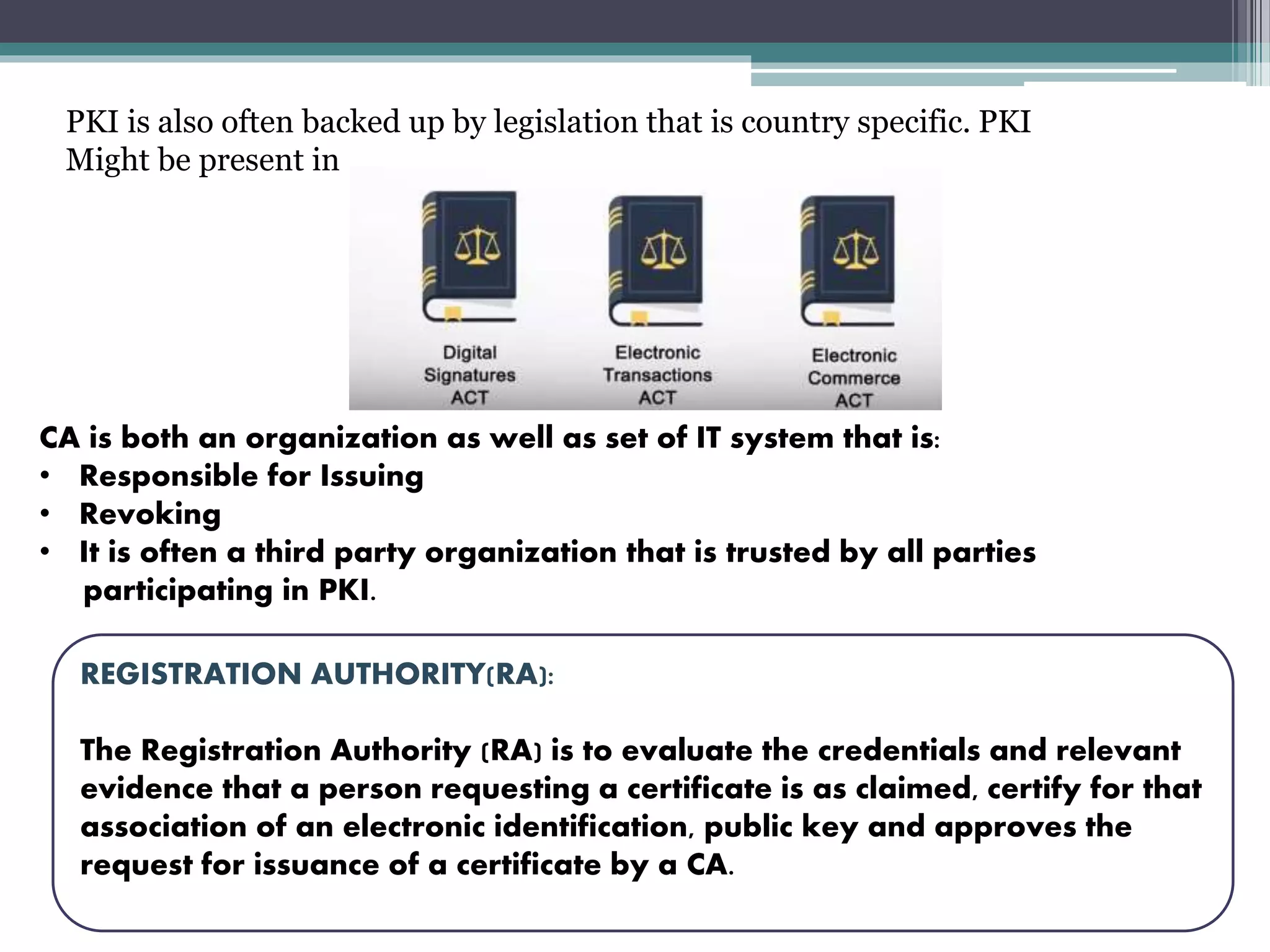
A public key infrastructure (PKI) allows for secure communication and data exchange over public networks through the use of public and private cryptographic key pairs provided by a certificate authority. A PKI uses asymmetric encryption where a public key is used to encrypt data and a private key is used to decrypt it. Digital certificates issued by a certificate authority are used to verify the identity of individuals by containing their public key and identification details signed by the certificate authority. This allows for trust in electronic transactions by ensuring people receive keys from the actual identity they claim to be rather than an impersonator.