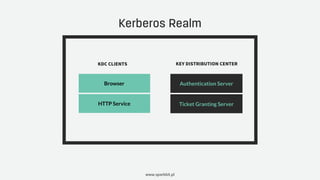
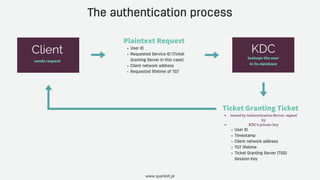
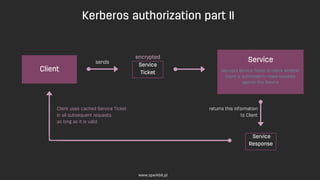
Kerberos is a network authentication protocol that uses 'tickets' to enable secure communication between nodes in a non-secure environment, developed at MIT and utilized in Windows and Unix systems. It provides Single Sign-On (SSO) services through a complex authentication process involving a Key Distribution Center (KDC) and ticket granting mechanisms, with limitations in web environments addressed by the SPNEGO protocol. Despite its effectiveness in intranets, Kerberos poses challenges such as being a single point of failure and restrictions in scenarios involving external clients.

![Kerberos is a computer network authentication protocol which works on
the basis of 'tickets' to allow nodes communicating over a non-secure
network to prove their identity to one another in a secure manner.
[Wikipedia]
What is Kerberos?
www.sparkbit.pl](https://image.slidesharecdn.com/kerberos-160916091806/85/Kerberos-2-320.jpg)