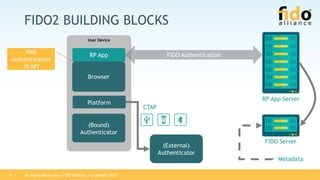
The document describes the FIDO2 specification which includes two new standards: WebAuthn for authentication in browsers and CTAP for platform authentication. It provides overviews and code snippets for how credentials can be registered and used for authentication on websites using public key cryptography with FIDO2 compliant security keys or platform authenticators on devices. The specification also covers credential management APIs and the processes of decommissioning credentials.




![All Rights Reserved | FIDO Alliance | Copyright 20175
RELYING PARTY APPLICATION
Browser “Application”:
A normal website - HTML, CSS,
JavaScript
Website, Inc. [US] https://www.acme.com
acme.com X](https://image.slidesharecdn.com/fido2specificationsoverview-171214213511/85/FIDO2-Specifications-Overview-5-320.jpg)



![All Rights Reserved | FIDO Alliance | Copyright 201710
NAVIGATOR.CREDENTIAL.CREATE()
if (!PublicKeyCredential) { /* Platform not capable. Handle error. */ }
var publicKey = {
challenge: Uint8Array.from(window.atob("PGifxAoBwCkWkm4b1CiIl5otCphiIh6MijdjbWFjomA="), c=>c.charCodeAt(0)),
// Relying Party:
rp: {
name: "Acme"
},
// User:
user: {
id: "1098237235409872"
name: "john.p.smith@example.com",
displayName: "John P. Smith",
icon: "https://pics.acme.com/00/p/aBjjjpqPb.png"
},
// This Relying Party will accept either an ES256 or RS256 credential, but
// prefers an ES256 credential.
pubKeyCredParams: [
{
type: "public-key",
alg: -7 // "ES256" as registered in the IANA COSE Algorithms registry
},
{
type: "public-key",
alg: -257 // Value registered by this specification for "RS256"
}
],](https://image.slidesharecdn.com/fido2specificationsoverview-171214213511/85/FIDO2-Specifications-Overview-10-320.jpg)
![All Rights Reserved | FIDO Alliance | Copyright 201711
NAVIGATOR.CREDENTIAL.CREATE()
timeout: 60000, // 1 minute
excludeCredentials: [], // No exclude list of PKCredDescriptors
extensions: {"webauthn.location": true} // Include location information
// in attestation
};
// Note: The following call will cause the authenticator to display UI.
navigator.credentials.create({ publicKey })
.then(function (newCredentialInfo) {
// Send new credential info to server for verification and registration.
}).catch(function (err) {
// No acceptable authenticator or user refused consent. Handle appropriately.
});](https://image.slidesharecdn.com/fido2specificationsoverview-171214213511/85/FIDO2-Specifications-Overview-11-320.jpg)




![All Rights Reserved | FIDO Alliance | Copyright 201716
NAVIGATOR.CREDENTIALS.GET()
if (!PublicKeyCredential) { /* Platform not capable. Handle error. */ }
var options = {
challenge: new TextEncoder().encode("climb a mountain"),
timeout: 60000, // 1 minute
allowCredentials: [{ type: "public-key" }]
};
navigator.credentials.get({ "publicKey": options })
.then(function (assertion) {
// Send assertion to server for verification
}).catch(function (err) {
// No acceptable credential or user refused consent. Handle appropriately.
});](https://image.slidesharecdn.com/fido2specificationsoverview-171214213511/85/FIDO2-Specifications-Overview-16-320.jpg)

![All Rights Reserved | FIDO Alliance | Copyright 201718
AUTHENTICATION - CREDENTIAL HINT
var options = {
challenge: encoder.encode("climb a mountain"),
timeout: 60000, // 1 minute
allowCredentials: [acceptableCredential1, acceptableCredential2];
extensions: { 'webauthn.txauth.simple':
"Wave your hands in the air like you just don’t care" };
};
navigator.credentials.get({ "publicKey": options })
.then(function (assertion) {
// Send assertion to server for verification
}).catch(function (err) {
// No acceptable credential or user refused consent. Handle appropriately.
});](https://image.slidesharecdn.com/fido2specificationsoverview-171214213511/85/FIDO2-Specifications-Overview-18-320.jpg)










