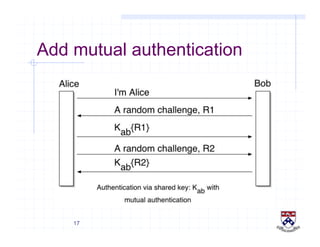
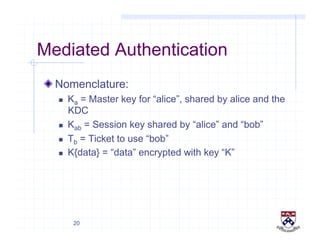
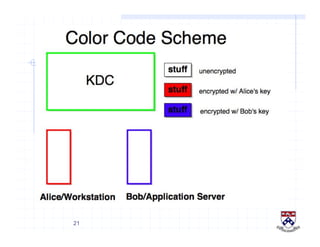
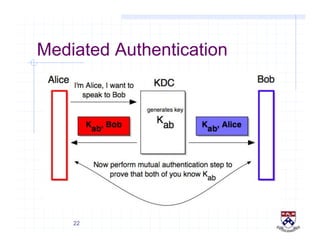
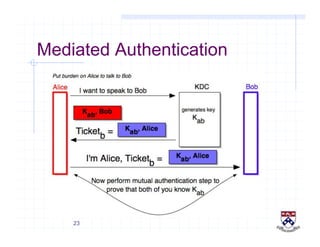
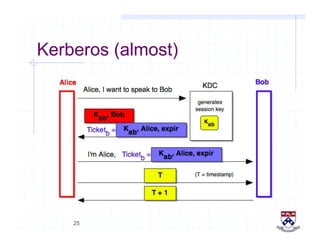
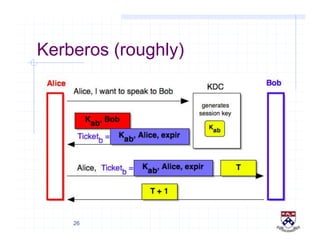
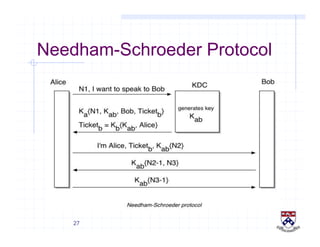
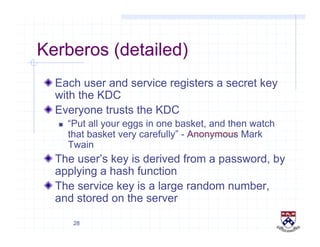
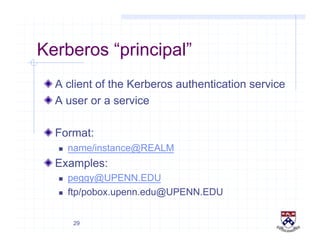
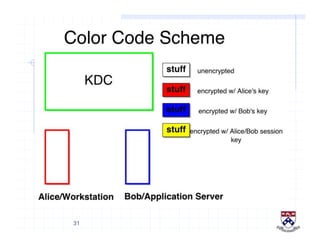
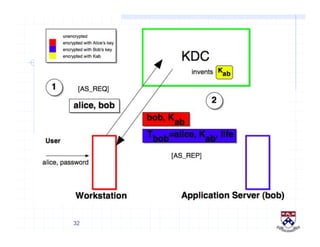
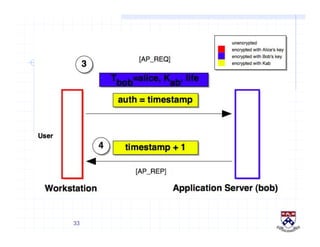
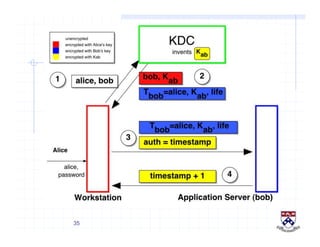
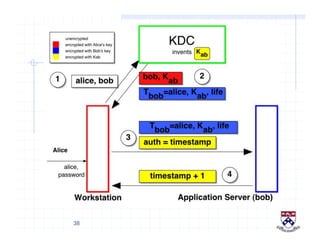
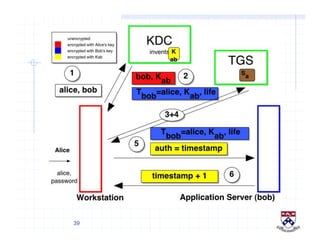
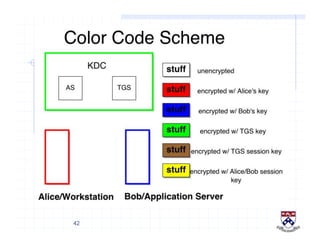
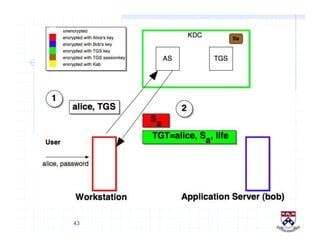
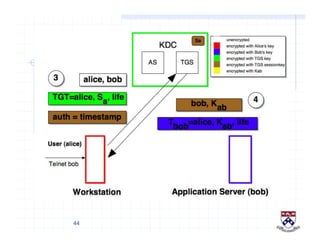
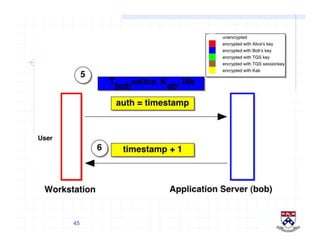
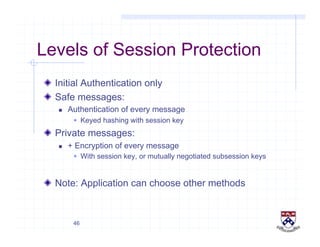
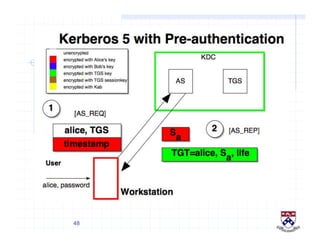
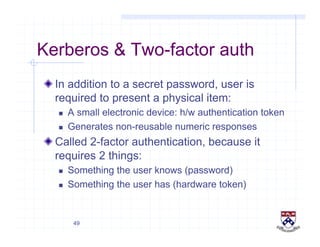
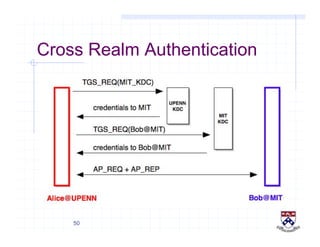
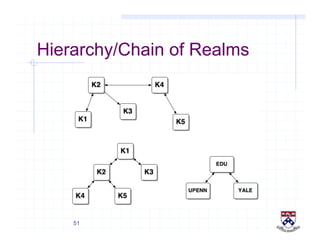
This document provides a high-level overview of how Kerberos authentication works. It explains that Kerberos uses a trusted third party called the Key Distribution Center (KDC) to mediate authentication between users and services. The KDC distributes session keys to allow communication and verifies users' identities through cryptographic operations. It also describes how Kerberos implements single sign-on through the use of ticket-granting tickets obtained from the KDC. Some advantages of Kerberos include strong authentication without sending passwords over the network and more convenient single sign-on for users.