Embed presentation
Downloaded 44 times






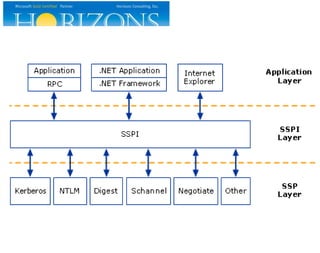

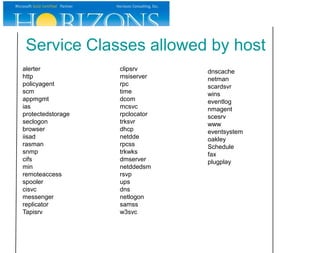


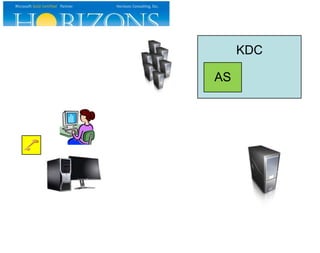

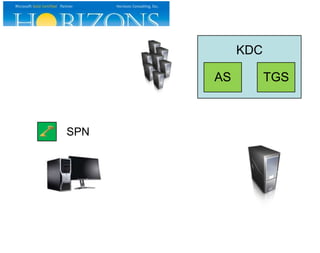












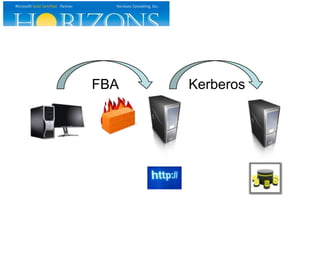





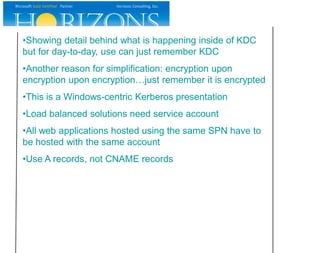



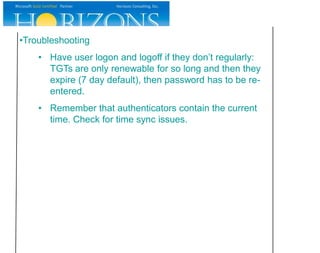






This document provides an overview and agenda for a presentation on Kerberos survival guide. The presentation covers Kerberos logon process, accessing a web site using Kerberos, troubleshooting Kerberos issues, and demonstrations of Kerberos and delegation. It includes definitions of key Kerberos terms like KDC, TGT, and service tickets. Details of the Kerberos protocol that are out of scope are also listed.









































