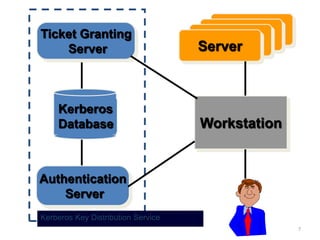
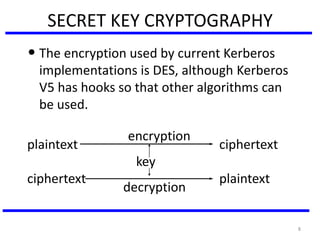
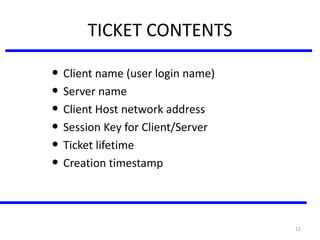
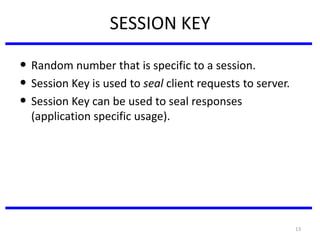
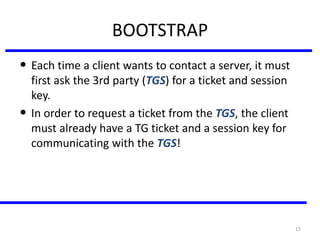
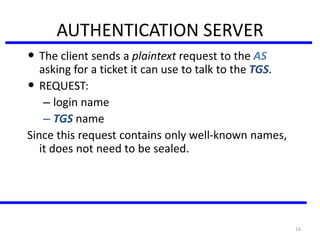
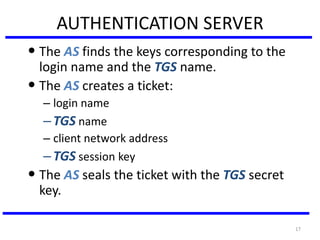
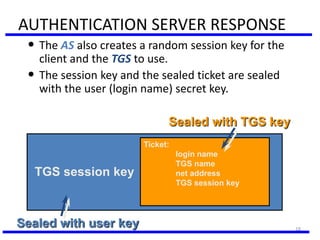
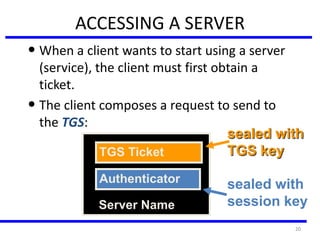
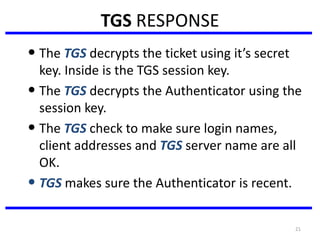
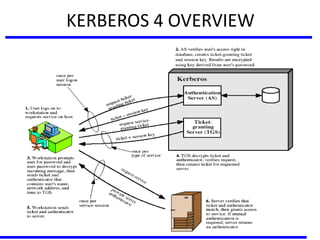
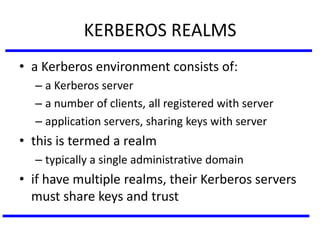
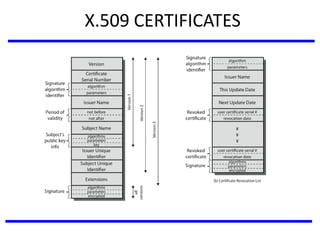
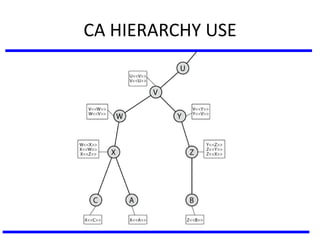
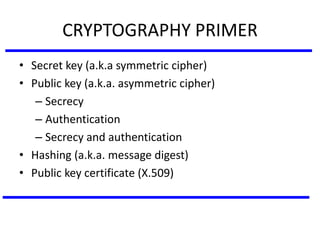
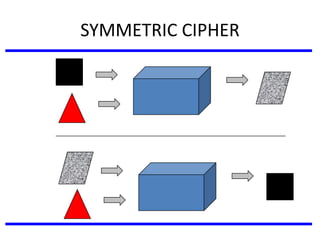
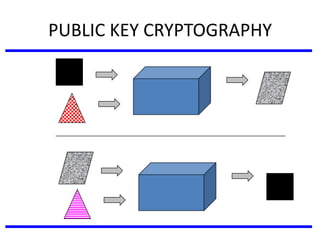
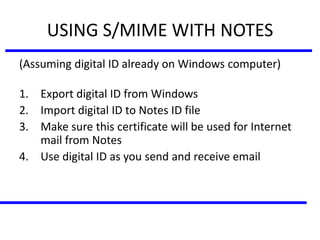
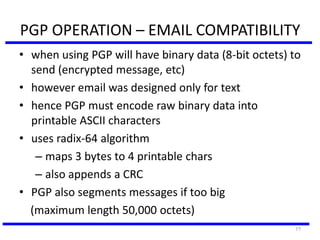
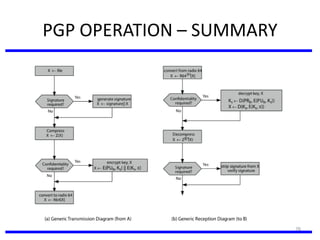
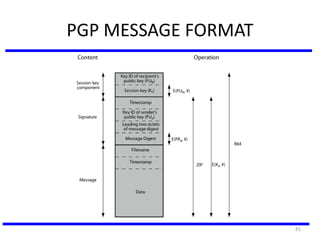
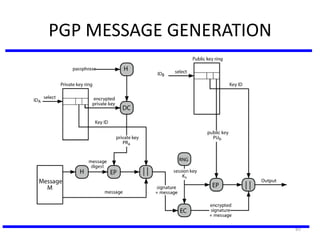
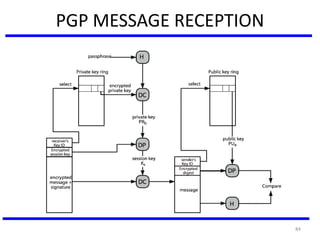
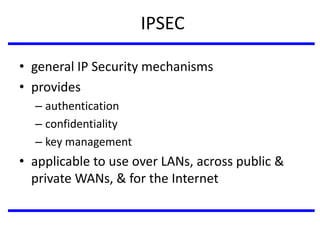
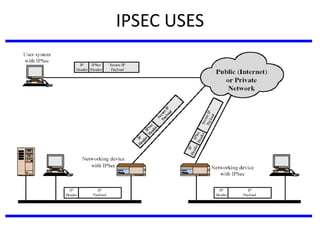
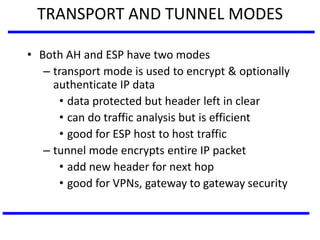
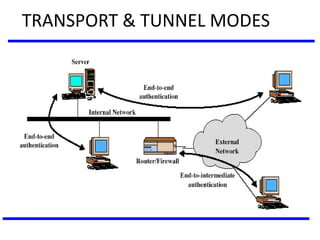
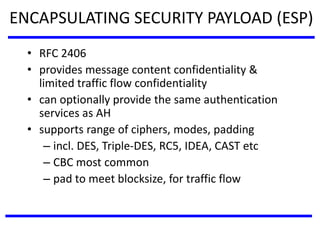
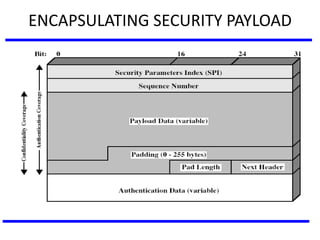
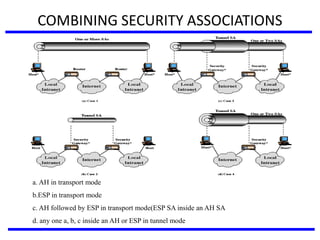
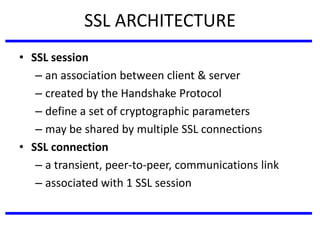
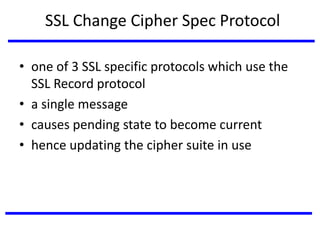
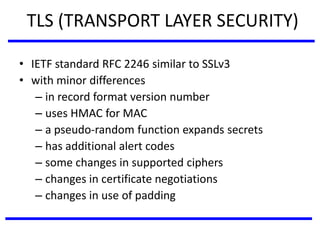
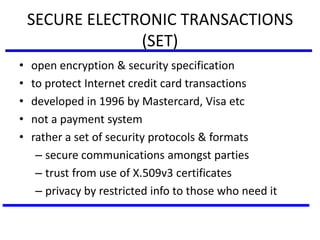
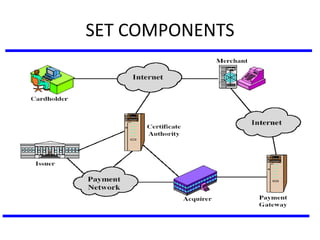
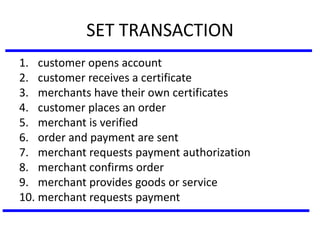
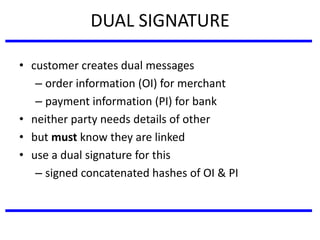
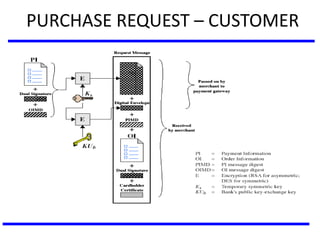
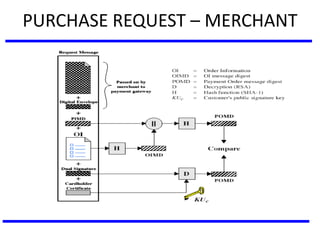
The document discusses various authentication applications in network security, focusing on Kerberos and X.509. It elaborates on how Kerberos functions as a trusted third-party authentication scheme that requires users to authenticate only once per session, and the processes involved in obtaining tickets for server access. It also covers the X.509 authentication service, including the structure and role of public key certificates in ensuring secure email communication through S/MIME.