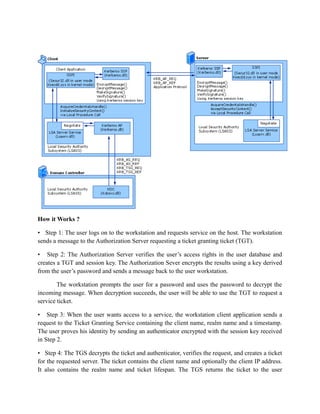
Kerberos is a network authentication protocol that provides secure authentication for client/server applications. It uses secret-key cryptography and relies on a trusted third party called the Key Distribution Center (KDC) which is aware of all systems on the network. Kerberos introduces tickets that allow a client access to a server after initial authentication with the KDC. The authentication process involves the client receiving a ticket-granting ticket from the KDC and then exchanging messages with the ticket-granting service and target server to gain access.