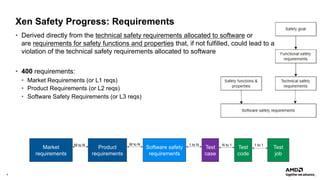
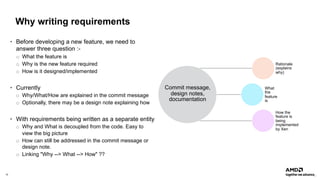
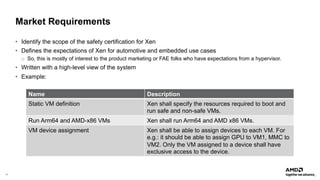
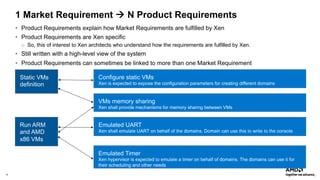
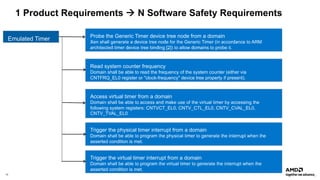
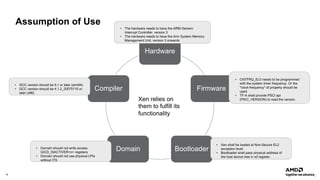
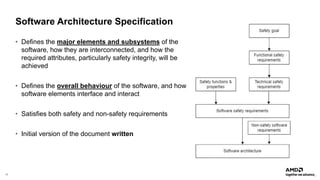
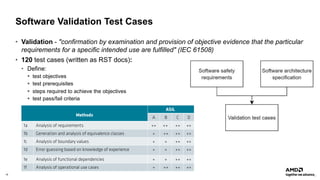
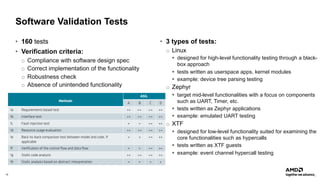
The document outlines AMD's efforts to achieve functional safety certification for the Xen hypervisor on ARM and AMD x86 platforms, adhering to standards like IEC 61508 and ISO 26262. It details progress in achieving MISRA C compliance, improving safety requirements, and developing test cases for validation. Emphasizing community collaboration, the document highlights the importance of clear requirement structures to enhance code quality and ensure reliable system operations.