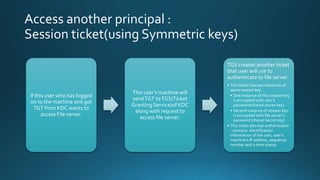
The document outlines the components and functioning of the Key Distribution Center (KDC) in the Kerberos authentication protocol, including principles like ticket granting services and session ticket usage. It details the process of user authentication, ticket creation, and the importance of shared secret keys for secure communication. Additionally, it addresses security concerns such as single points of failure, key theft, and the need for time synchronization across machines.