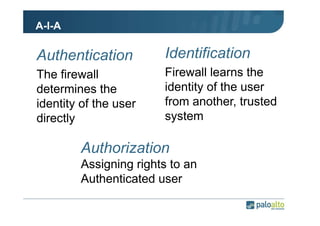
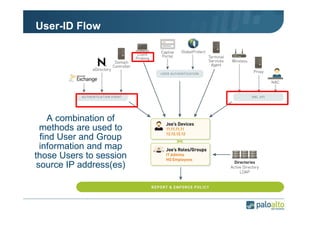
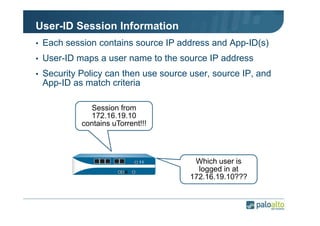
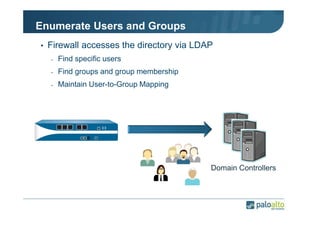
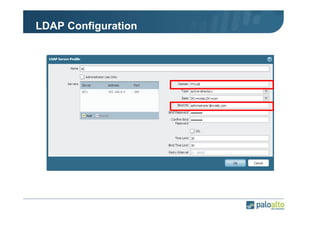
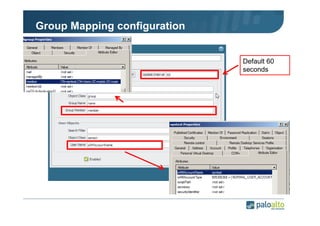
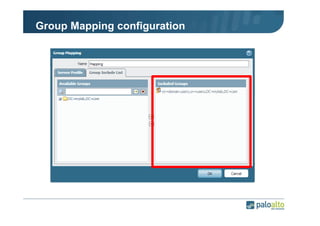
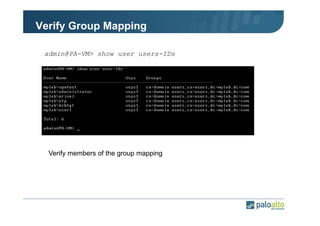
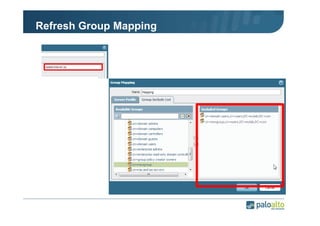
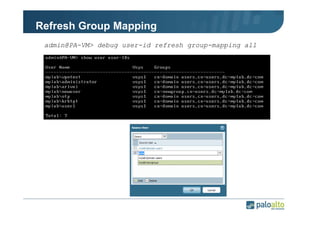
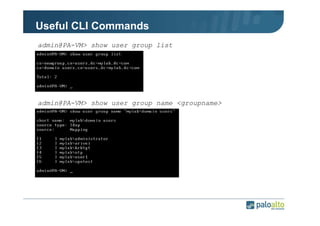
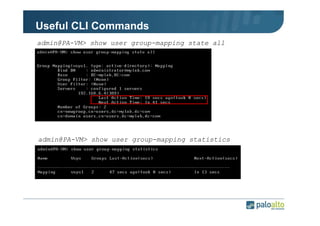
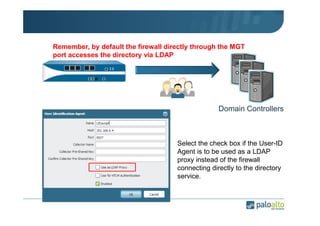
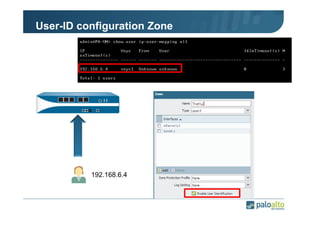
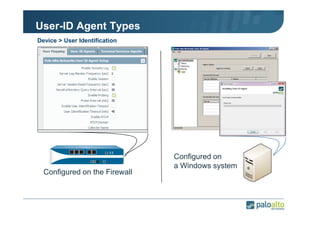
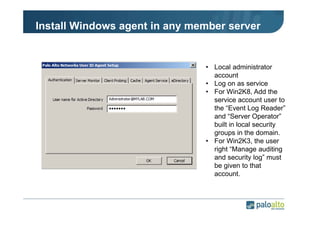
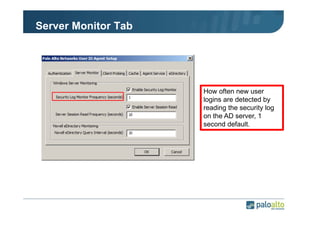
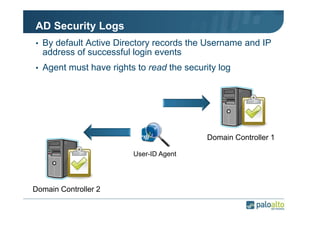
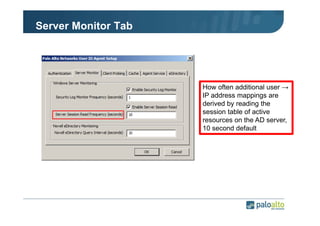
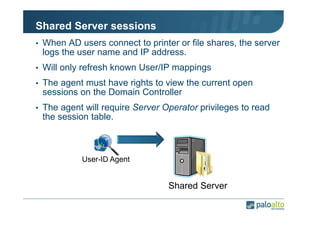
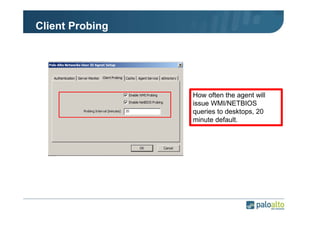
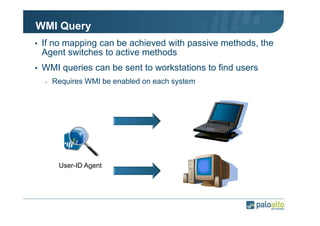
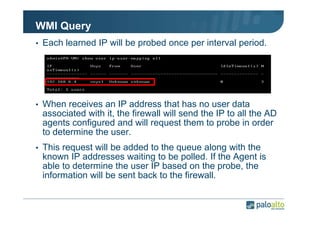
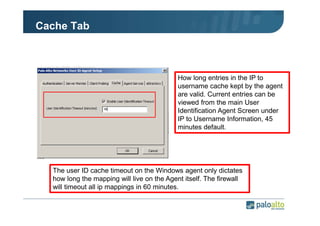
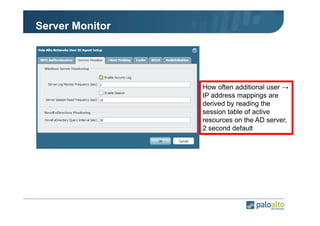
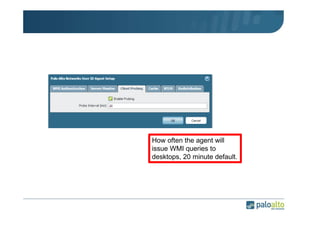
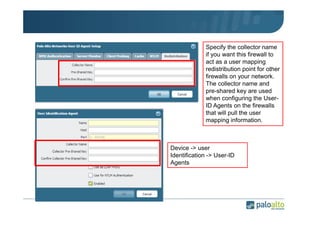
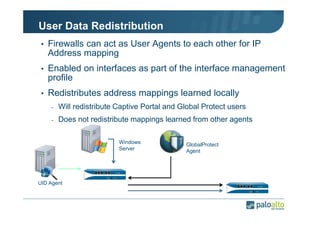
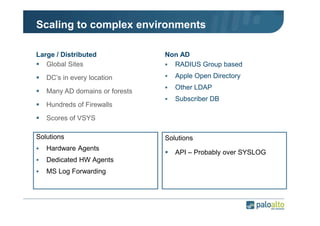
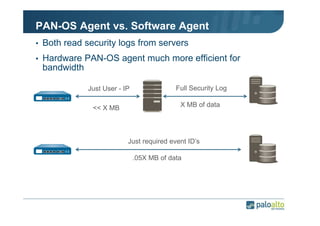
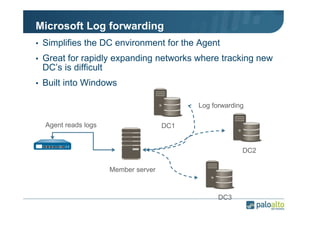
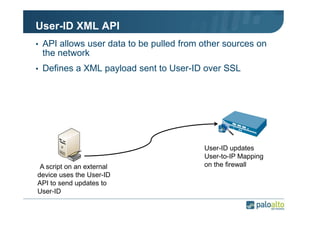
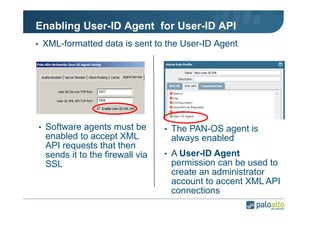
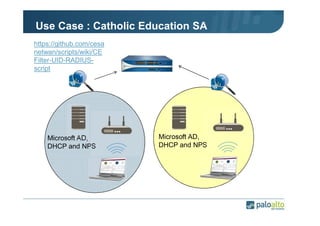
The document details the user identification (user-id) processes of a Palo Alto Networks firewall, focusing on how it maps users to IP addresses through various methods such as LDAP and WMI queries. It outlines the configuration requirements for user-id agents, monitoring of Active Directory security logs, and best practices for managing user data redistribution in complex environments. Additionally, it mentions the use of APIs for external user data integration.