Embed presentation
Downloaded 1,112 times










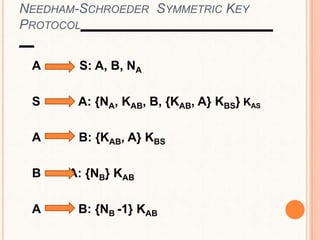

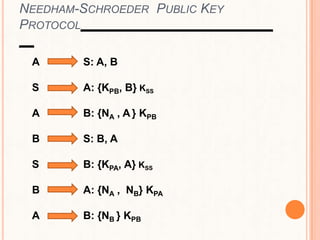
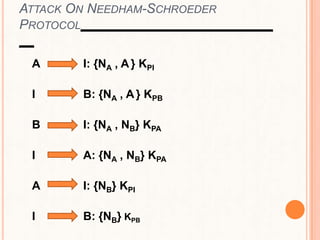
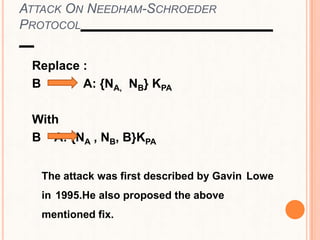
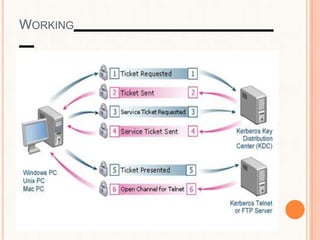
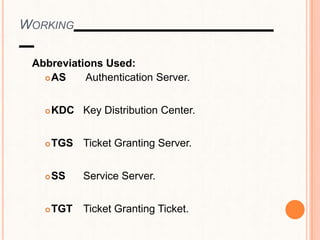
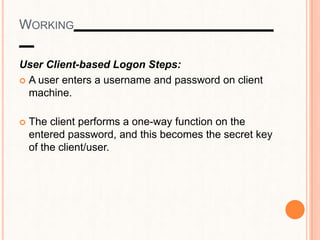

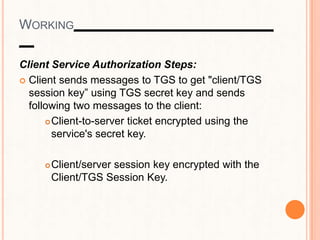
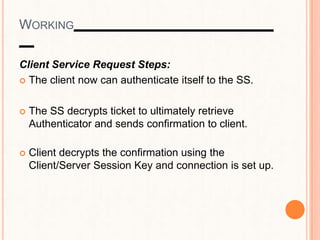



This document provides an overview of the Kerberos network authentication protocol. It discusses that Kerberos was developed at MIT to allow secure authentication over insecure networks. It provides a high-level overview of how Kerberos uses tickets and session keys to authenticate users and allow access to services without reentering passwords. The document also summarizes the Needham-Schroeder protocol that inspired part of Kerberos' design and discusses some applications and weaknesses of the Kerberos protocol.























