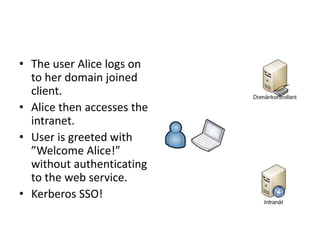
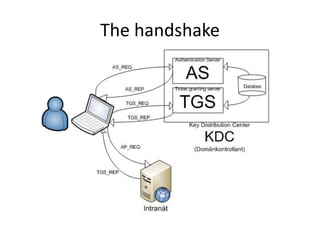
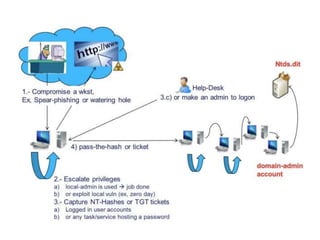
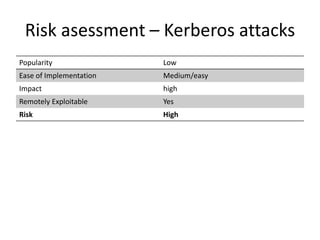
This document discusses Kerberos attacks and defenses against them. It describes how Kerberos single sign-on authentication works and some common attacks such as man-in-the-middle attacks, downgrade attacks, pass-the-ticket attacks, and creating a "golden ticket". It recommends ways to harden Kerberos security, such as using newer domain controllers, AES encryption, strict KDC validation, separate client networks, and changing the KRBTGT password regularly. Detecting pass-the-ticket attacks is difficult but a SIEM solution may help determine if tickets are being used inappropriately.