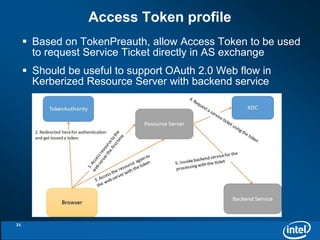
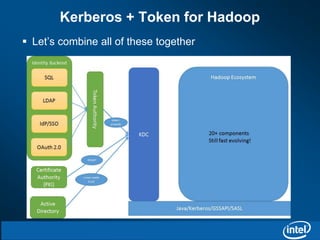
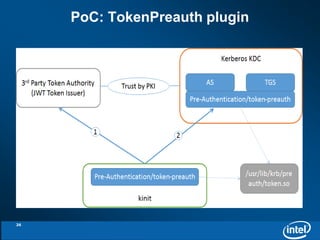
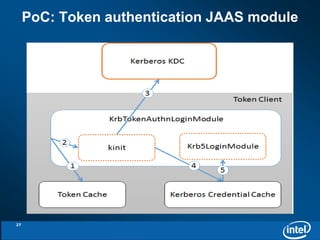
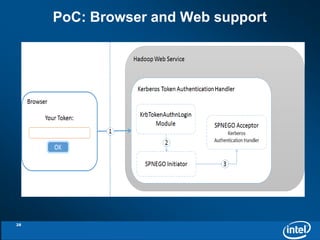
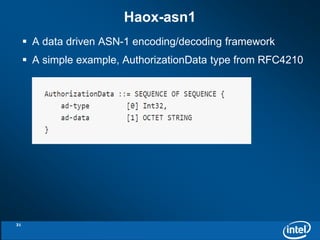
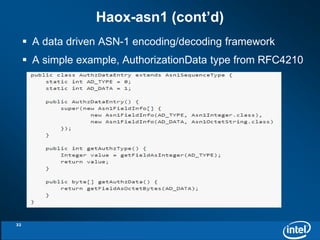
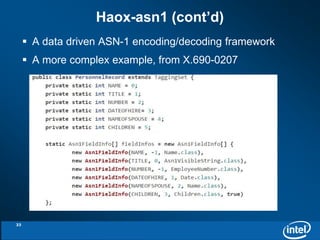
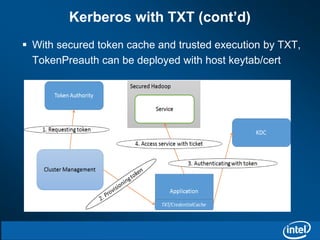
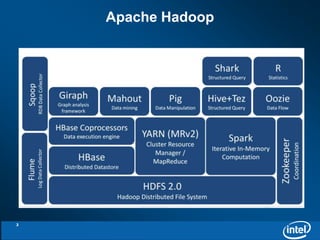
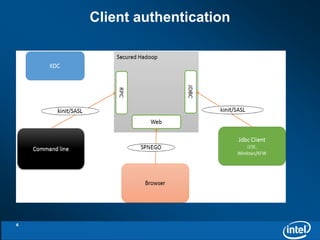
The document discusses the integration of Kerberos authentication with Hadoop and the challenges faced in deploying it within a large and evolving ecosystem. It outlines the need for token-based authentication methods to enhance security and facilitate the adoption of third-party solutions while ensuring performance efficiency. Future work includes collaboration with MIT to standardize these authentication solutions and to improve the overall security framework for Hadoop applications.













![TokenPreauth mechanism (cont’d)
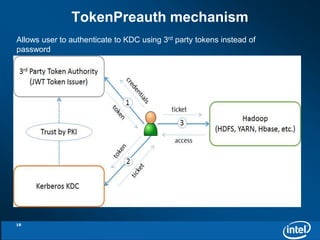
Client principal may exist or not during token validating
and ticket issuing
kinit –X token=[Your-Token], by default ref. ~/.kerbtoken
How token being generated may be out of scope, left for
token authority
Identity Token -> Ticket Granting Ticket, Access Token ->
Service Ticket
Ticket lifetime derived from token SHOULD be in the time
frame of the token
Ticket derived from token may be not renewable
20](https://image.slidesharecdn.com/kerberosonhadoop-141016043552-conversion-gate01/85/Kerberos-Token-and-Hadoop-20-320.jpg)