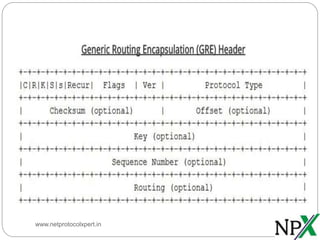
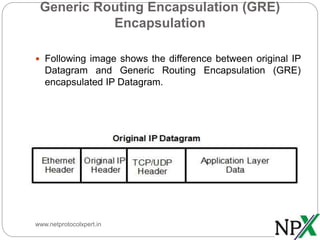
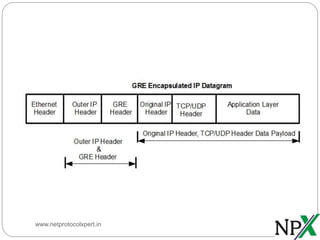
Generic routing encapsulation (GRE) is a tunneling protocol that can encapsulate many network layer protocols inside IP tunnels to transport IP packets across networks. GRE was first developed by Cisco and later became an industry standard. It allows routing of IP packets between private networks separated by public networks, and supports encapsulating broadcast and multicast traffic. While GRE does not encrypt data, it is often used with secure protocols like IPSec for network security. The GRE header contains fields for checksums, routing, keys, and sequence numbers to authenticate and track encapsulated packets.