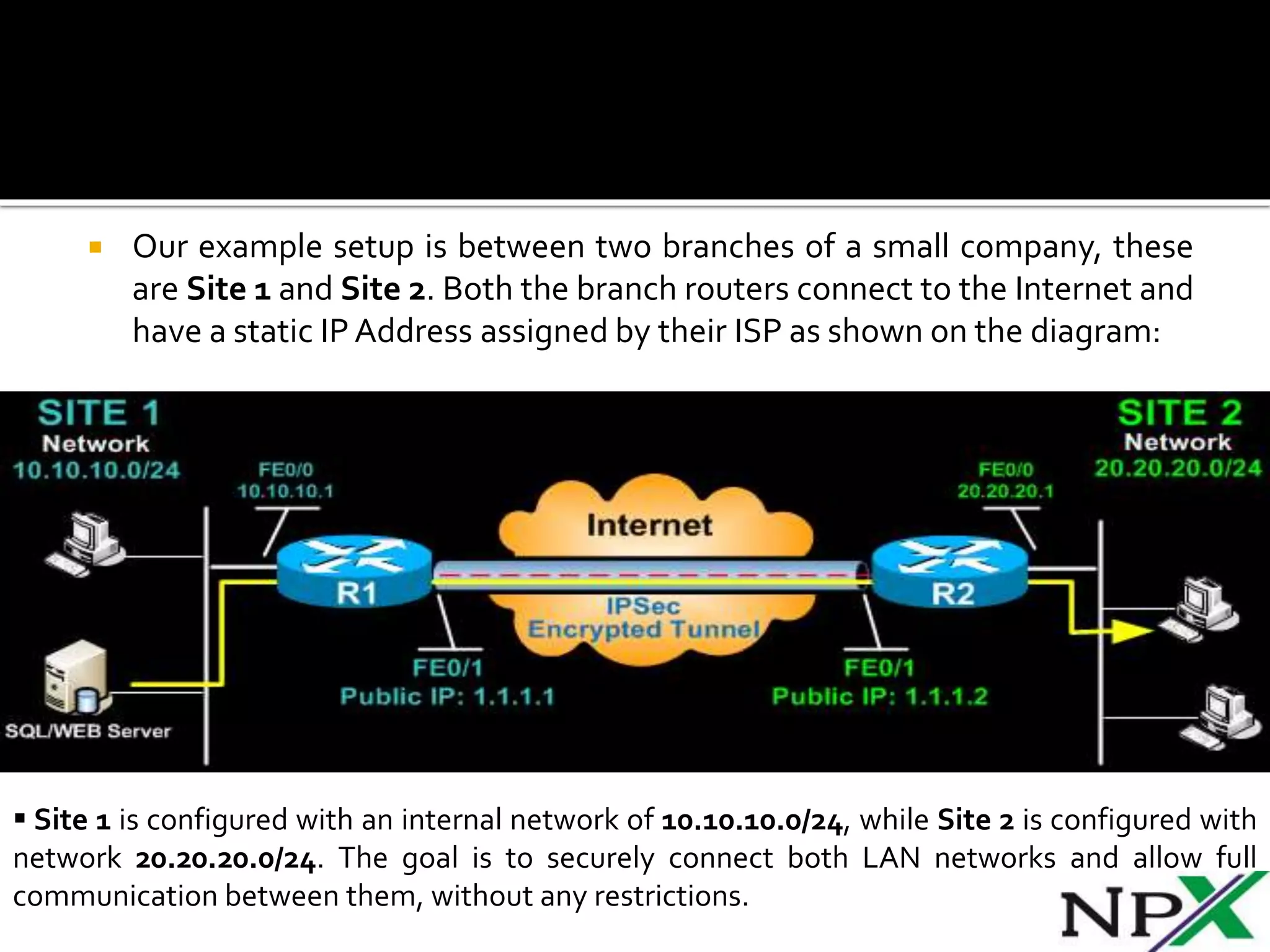
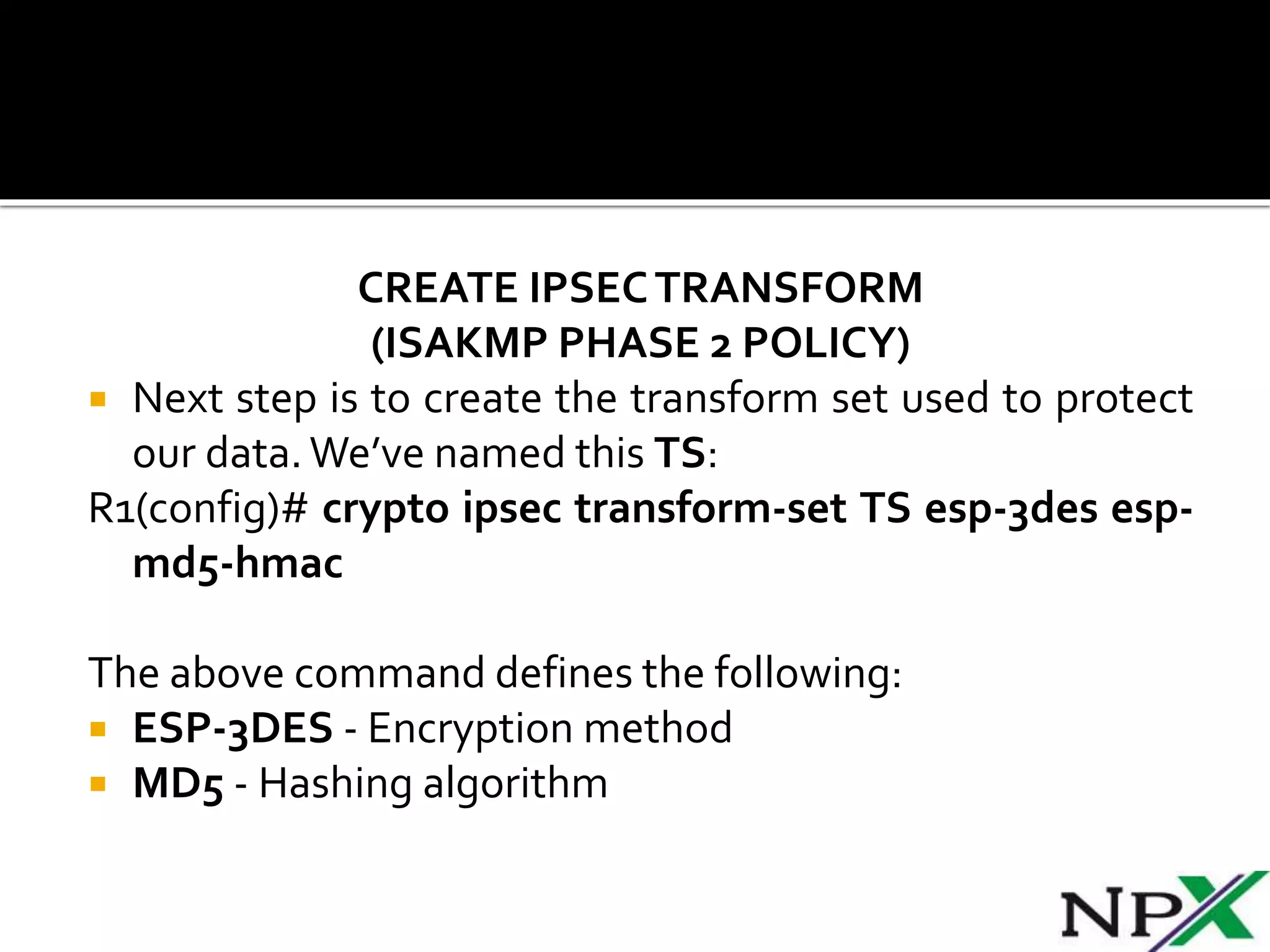
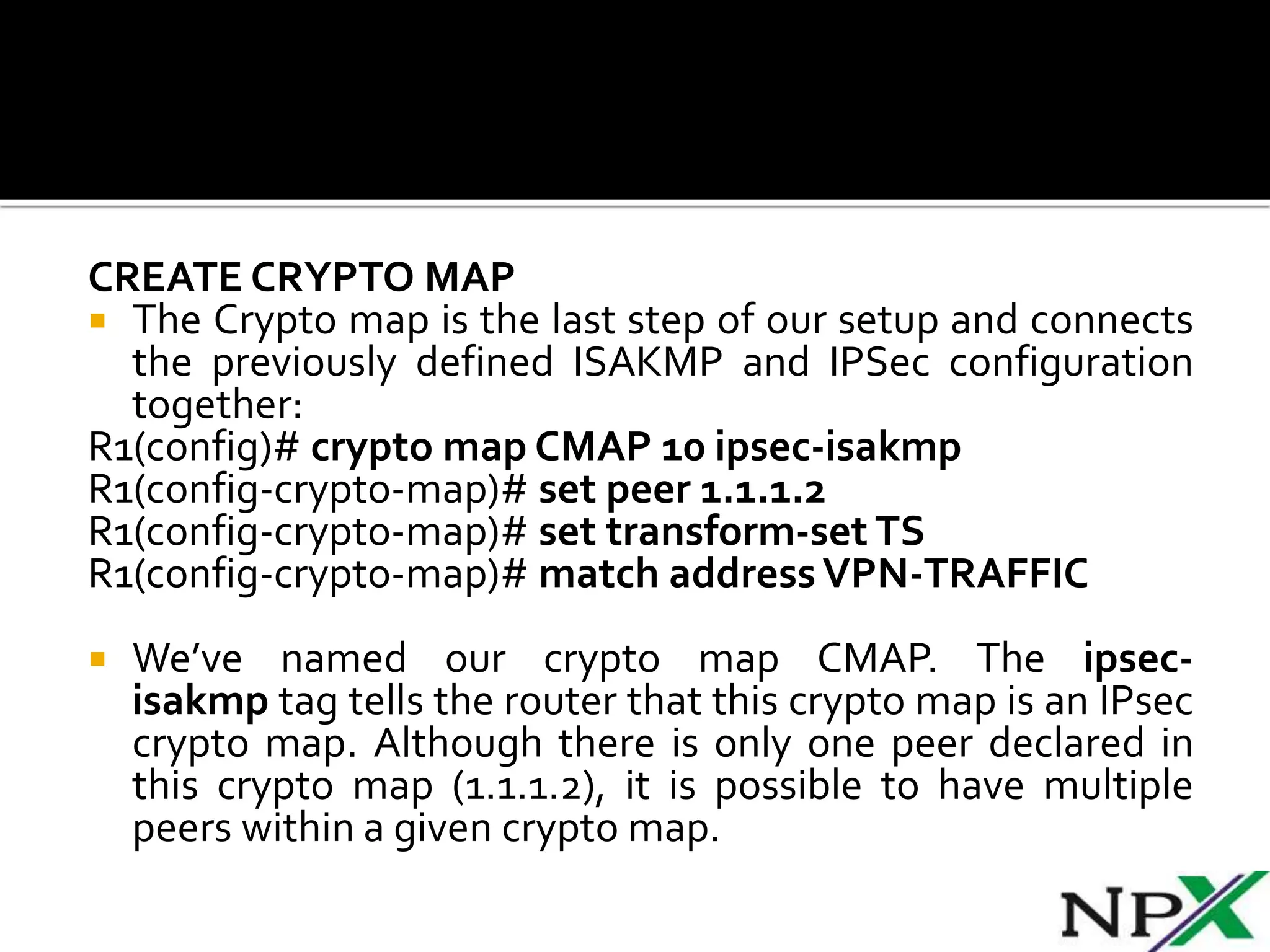
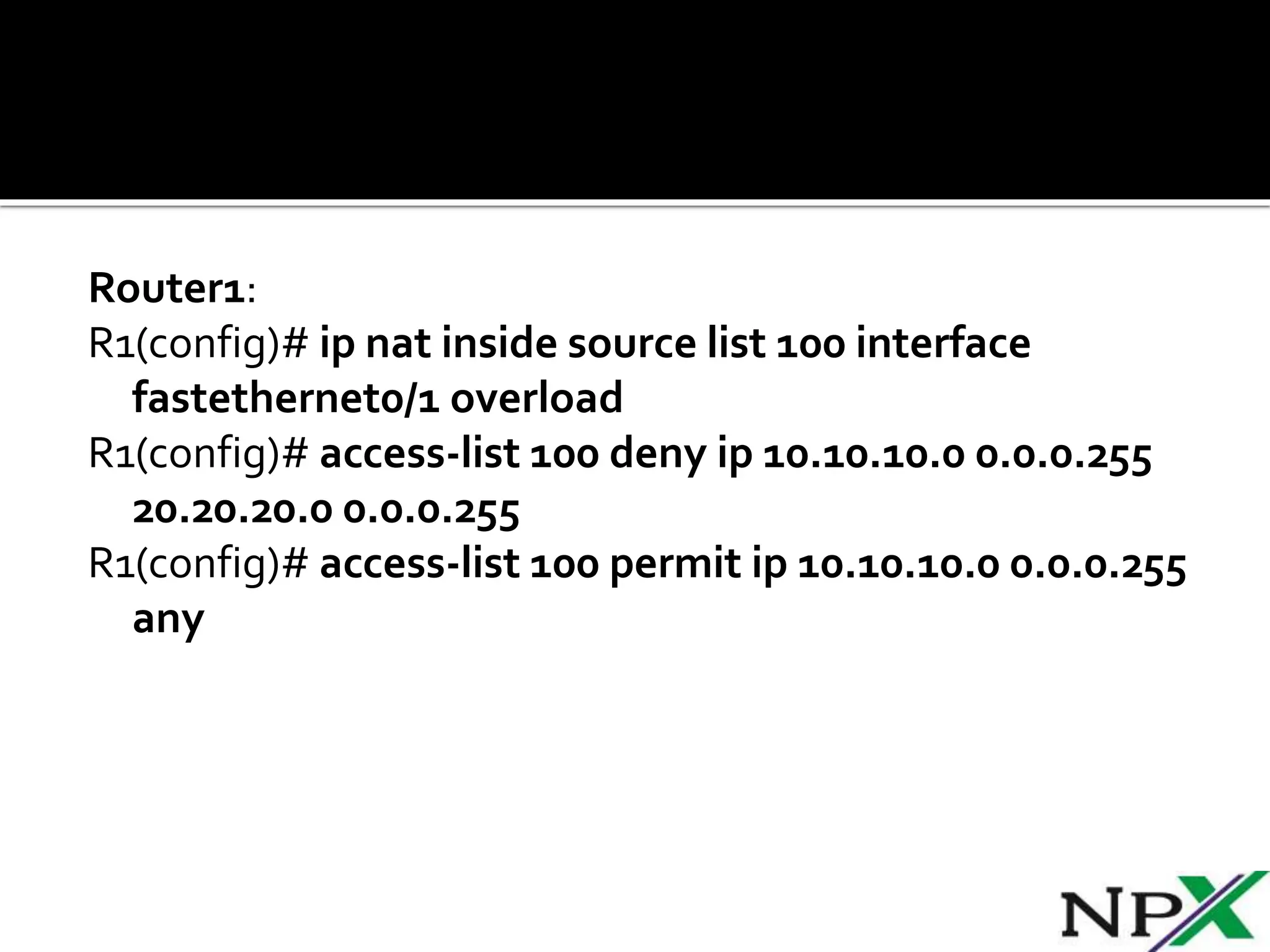
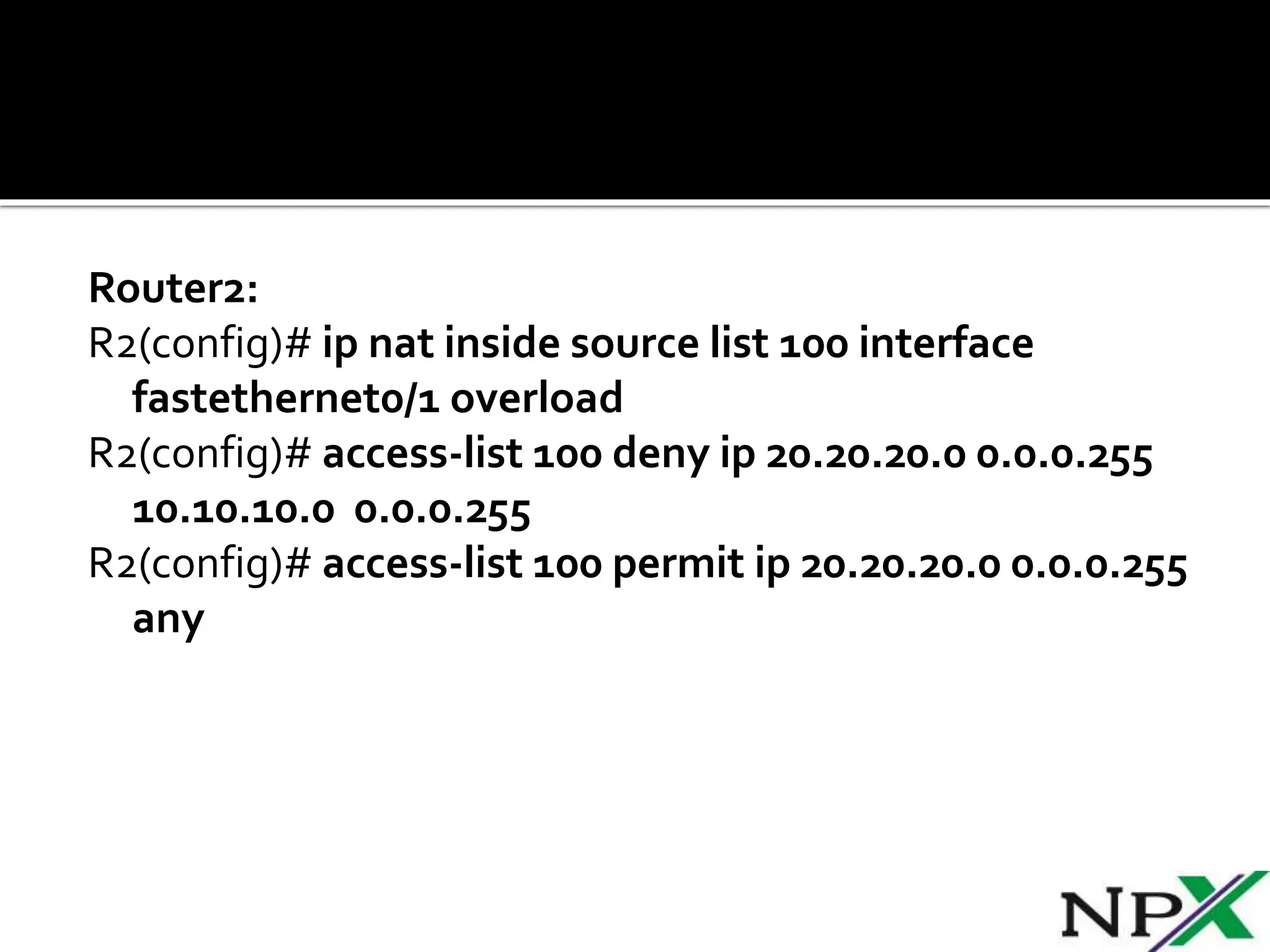
Site-to-site IPSec VPN tunnels securely transmit data between two network sites using encryption. ISAKMP and IPSec are used to establish and encrypt the VPN tunnel. ISAKMP phase 1 creates an initial secure tunnel, then phase 2 creates the data transmission tunnel using encryption algorithms. Configuring IPSec requires defining ISAKMP and transform sets, access lists, crypto maps, and applying crypto maps to interfaces.