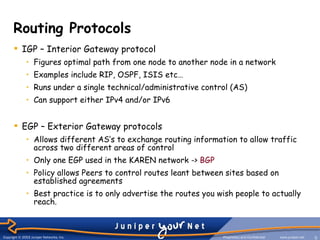
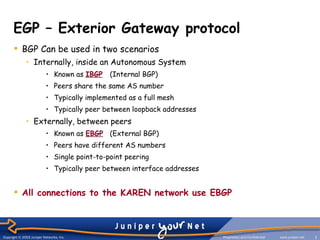
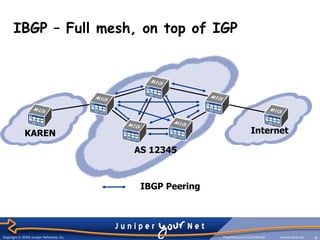
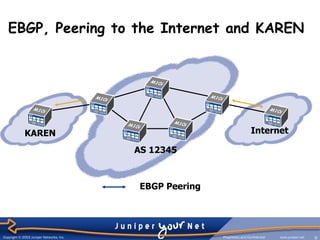
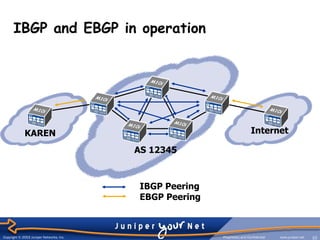
The document provides an overview of Border Gateway Protocol (BGP) which is the routing protocol used to exchange routes between institutions and the KAREN network. BGP allows different autonomous systems (AS) to exchange routing information and is more than just a routing protocol as it contains additional route attributes that are used for policy rules. BGP can operate internally within an AS or externally between ASes to control route propagation based on commercial agreements.