Embed presentation
Downloaded 71 times

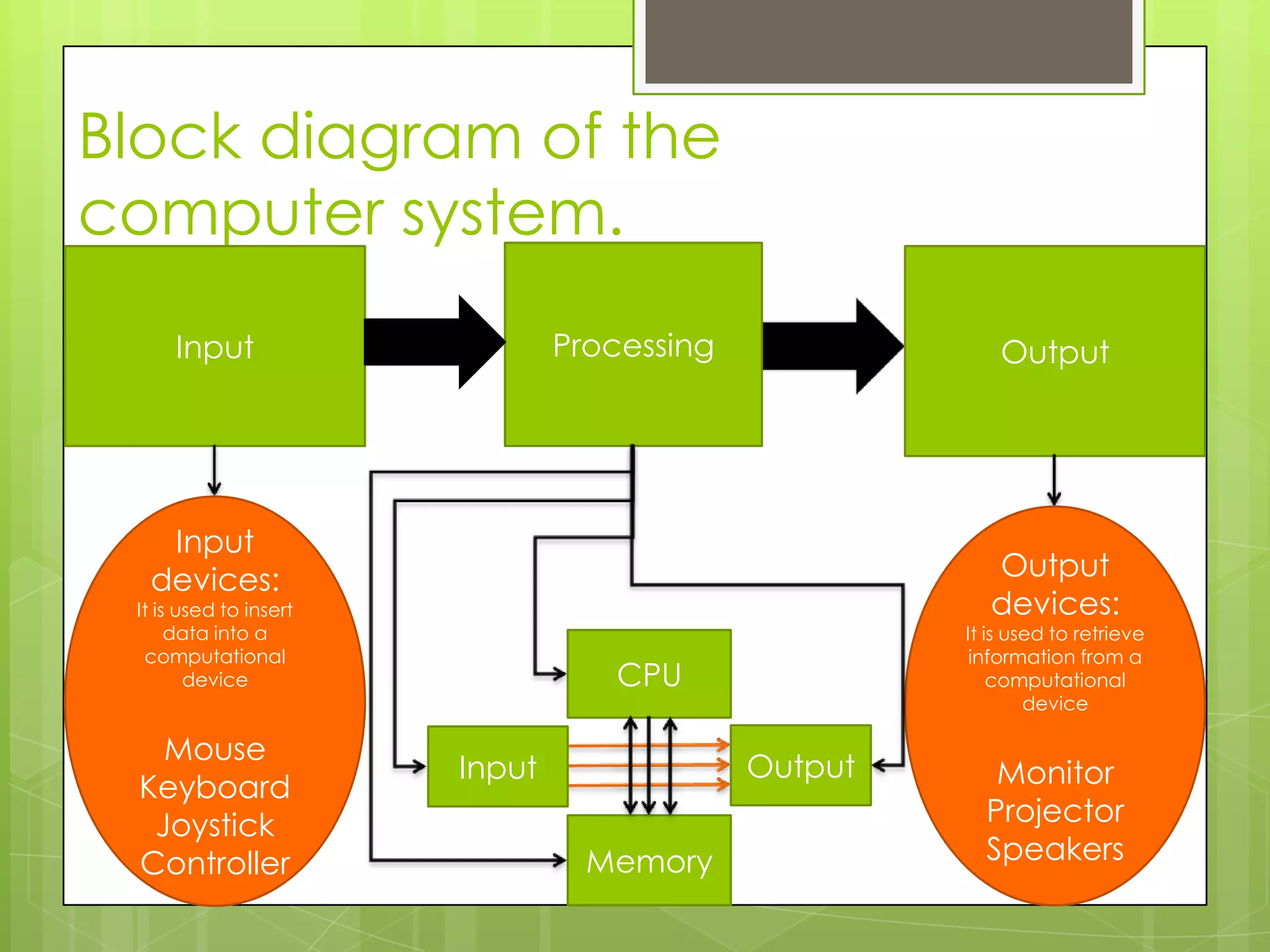
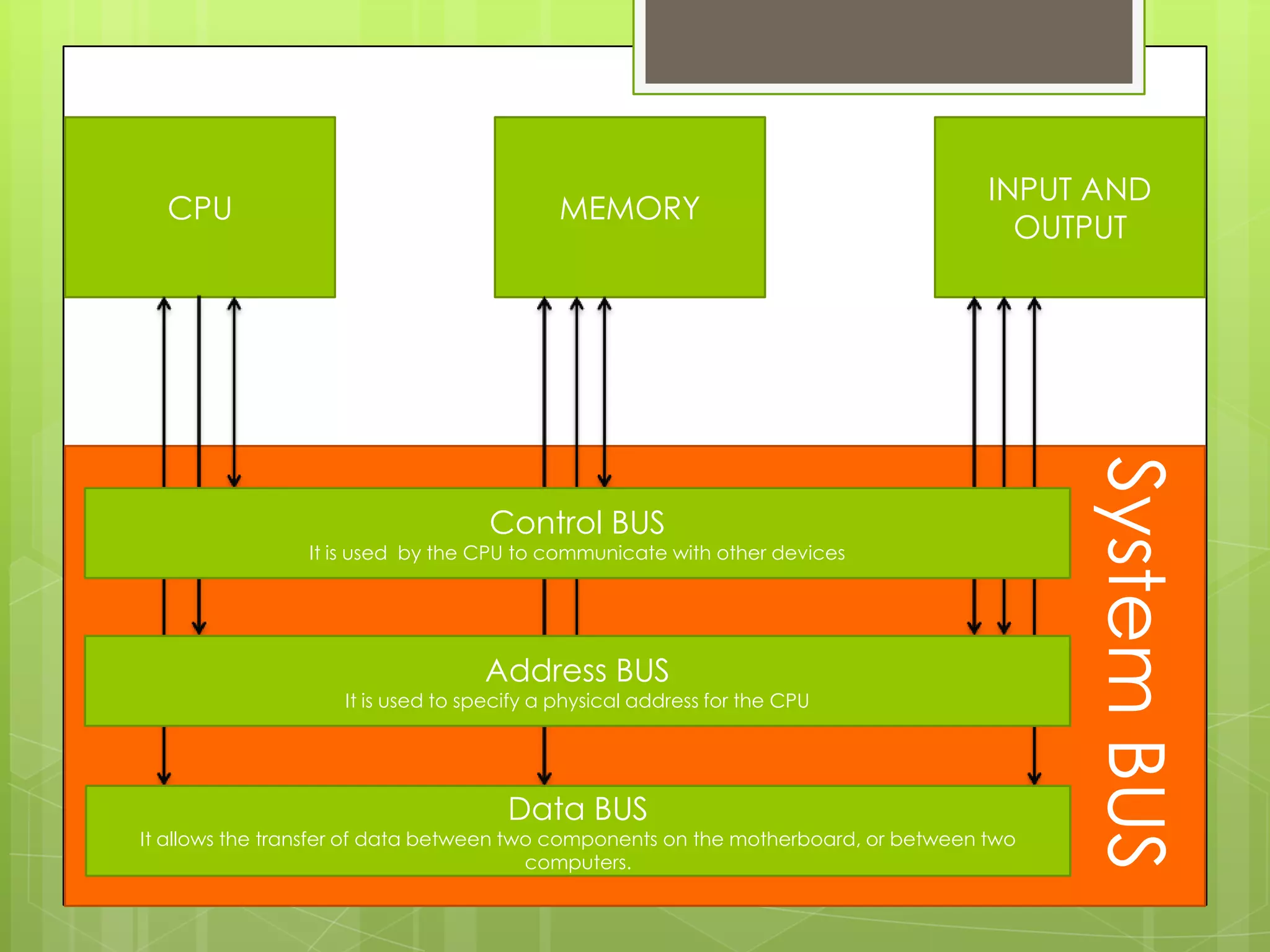
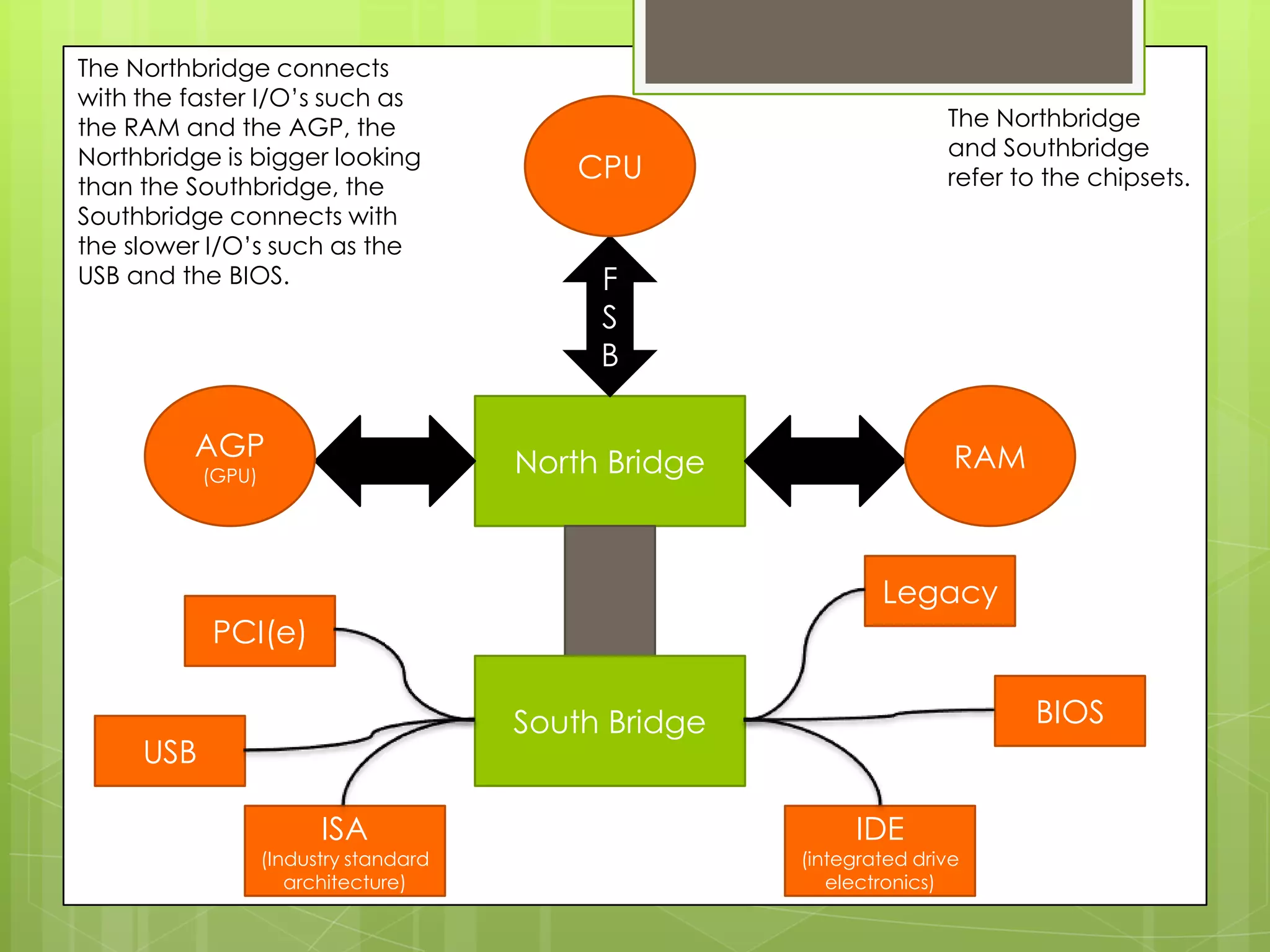
The document outlines the data flow within a computer system using a block diagram that illustrates input devices (mouse, keyboard), output devices (monitor, projector), and the interaction between the CPU, memory, and other components. It describes the roles of the northbridge and southbridge chipsets in connecting high-speed and low-speed I/O devices. Additionally, it explains the function of address and data buses in coordinating communication between components.



