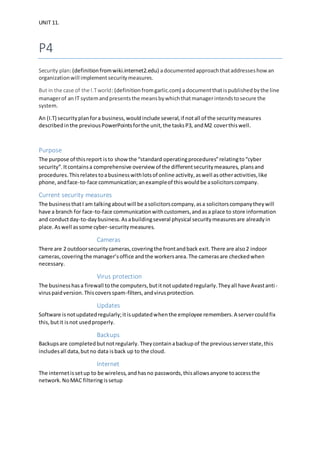
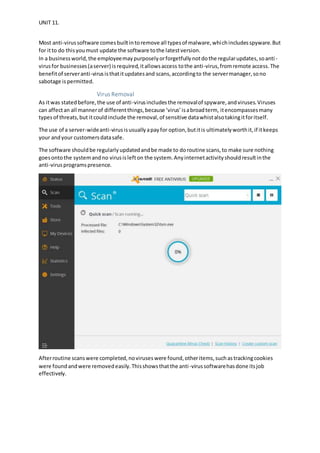
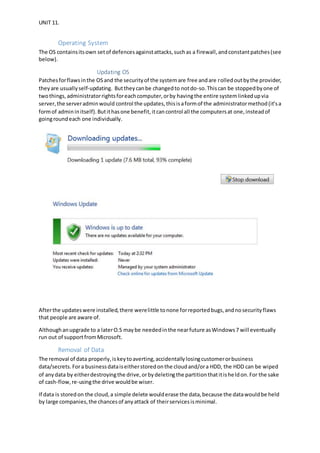
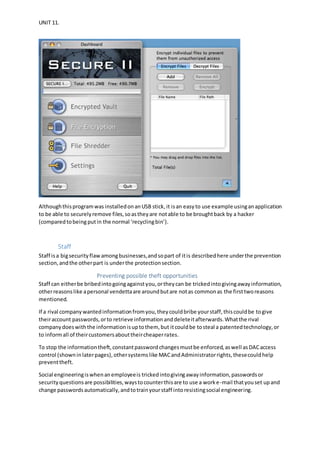
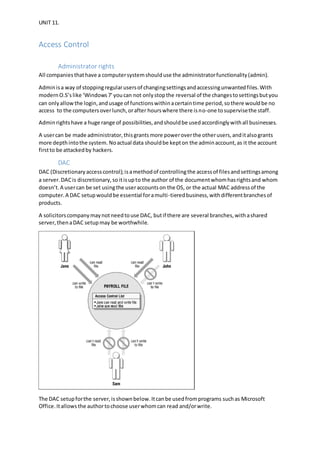
The document discusses security measures for a solicitor's company including physical security cameras and locks, cybersecurity such as firewalls, antivirus software, and regular updates, access controls like administrator rights and discretionary access control, and backups stored on the cloud. While current security is adequate, improvements could include an alarm system, more secure encryption for sensitive data, and prioritizing RAM to isolate privileged processes. The security plan implemented has improved safety significantly but physical security could be strengthened further.