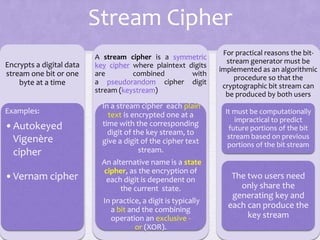
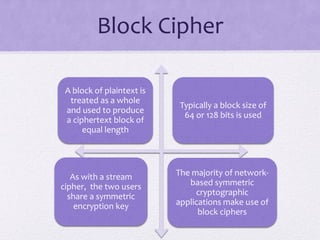
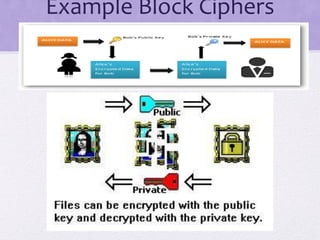
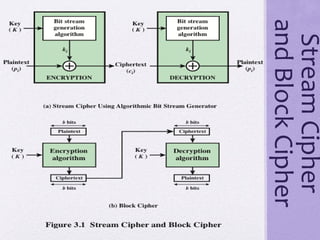
1. The document discusses network security and provides details about stream ciphers and block ciphers. It explains how each type of cipher works and provides examples of each.
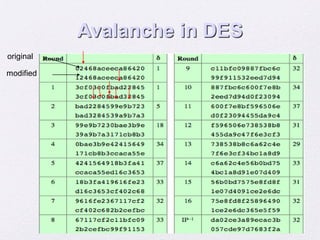
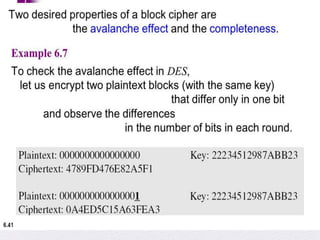
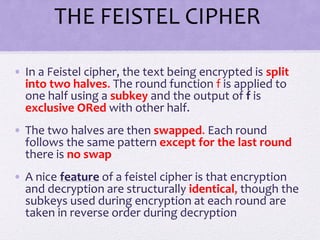
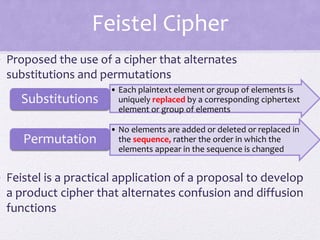
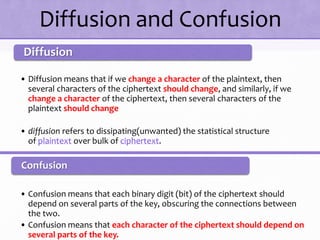
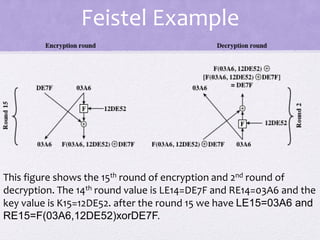
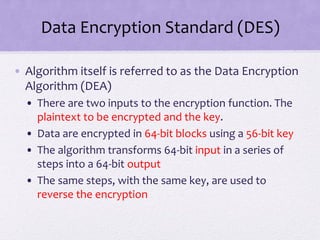
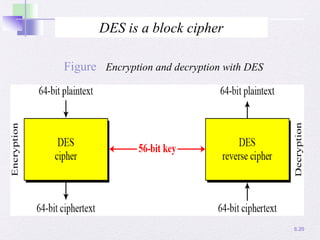
2. Details are given about the Feistel cipher structure and how it provides diffusion and confusion through repeated rounds. The Data Encryption Standard (DES) algorithm is described as a prominent example of a Feistel cipher.
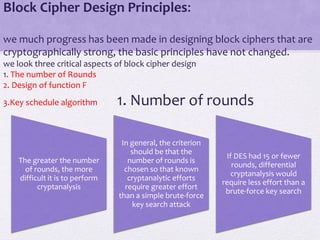
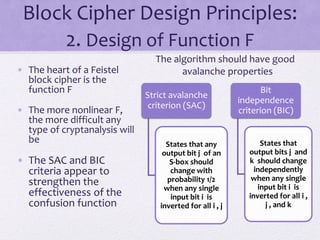
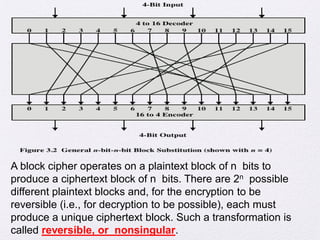
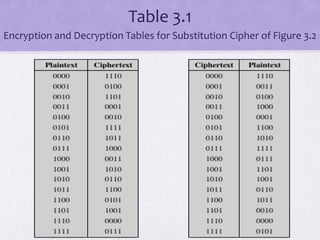
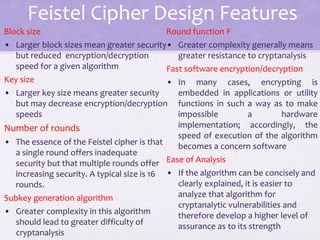
3. Principles of block cipher design are outlined, emphasizing the importance of number of rounds, design of the round function F, and the key schedule algorithm in providing security.

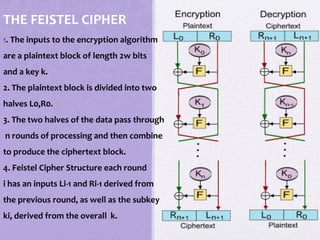



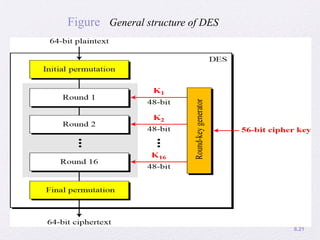
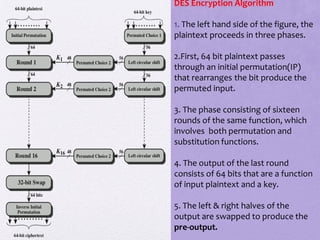
![6. Finally, the pre-output is passed through permutation
[IP-1] that is inverse of the initial permutation function, to
produce the 64 bit ciphertext.
7. The right hand side portion, in which the 56 bit key is
used. Initially the key is passed through a permutation
function.
8. Then for each 16 rounds, a subkey(Ki) is produced a
combination of a left circular shift and a permutation.
9.This is same for each round. But different subkey is
produced because the repeated shift of the key bits](https://image.slidesharecdn.com/1-190215090354/85/Block-Ciphers-and-the-Data-Encryption-Standard-23-320.jpg)