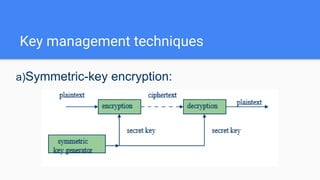
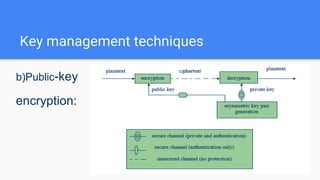
Key management involves the generation, exchange, storage, use, and replacement of cryptographic keys within a cryptosystem, addressing the entire key lifecycle to combat threats such as key compromise. Techniques include symmetric and public-key encryption, with notable algorithms like the Diffie-Hellman key exchange introduced in 1976 for secure key exchange. Digital certificates serve as identity documents that bind public keys to individuals or organizations, validated by certification authorities to facilitate secure communications.