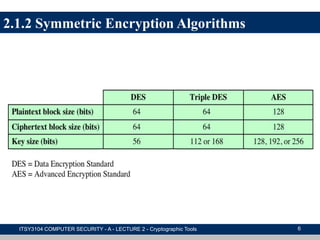
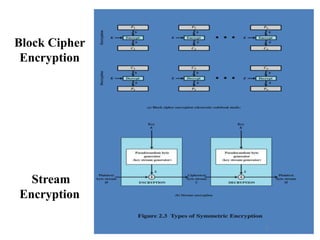
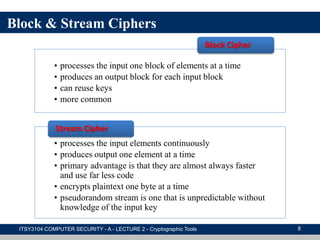
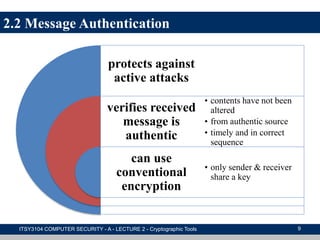
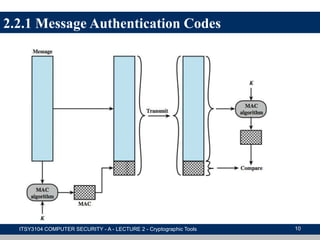
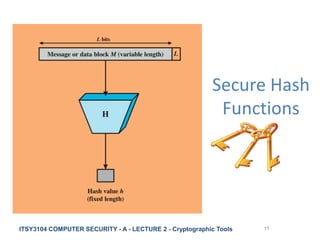
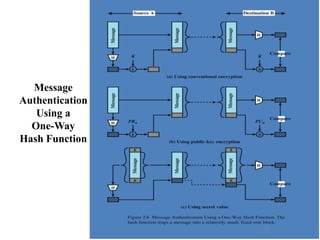
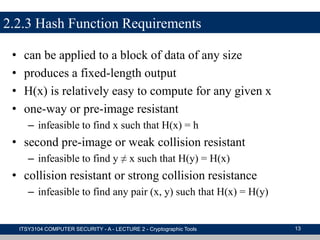
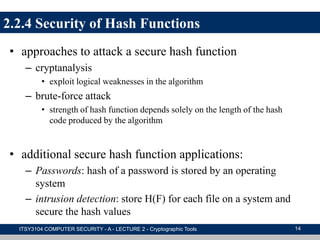
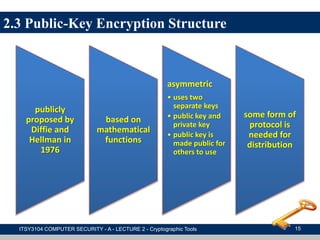
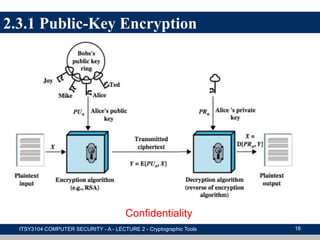
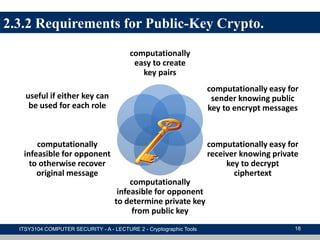
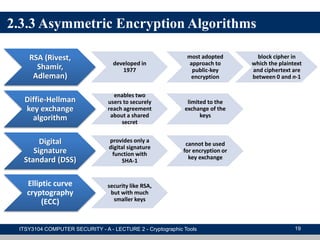
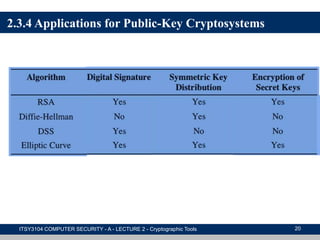
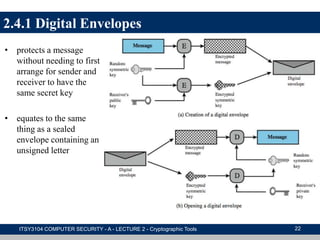
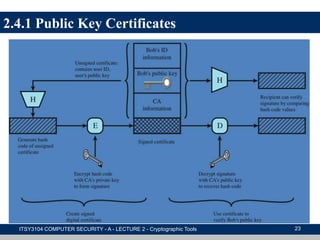
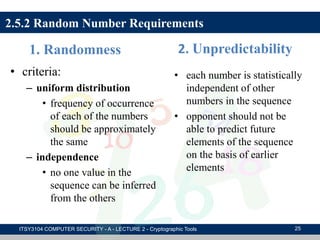
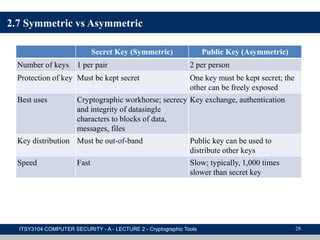
The document provides an overview of cryptographic tools in computer security, focusing on symmetric and asymmetric encryption methods, message authentication, hash functions, and digital signatures. It discusses the algorithms, principles, and applications of these techniques, highlighting their roles in ensuring confidentiality, integrity, and authenticity of data. Additionally, it addresses the importance of random number generation and the encryption of stored data.