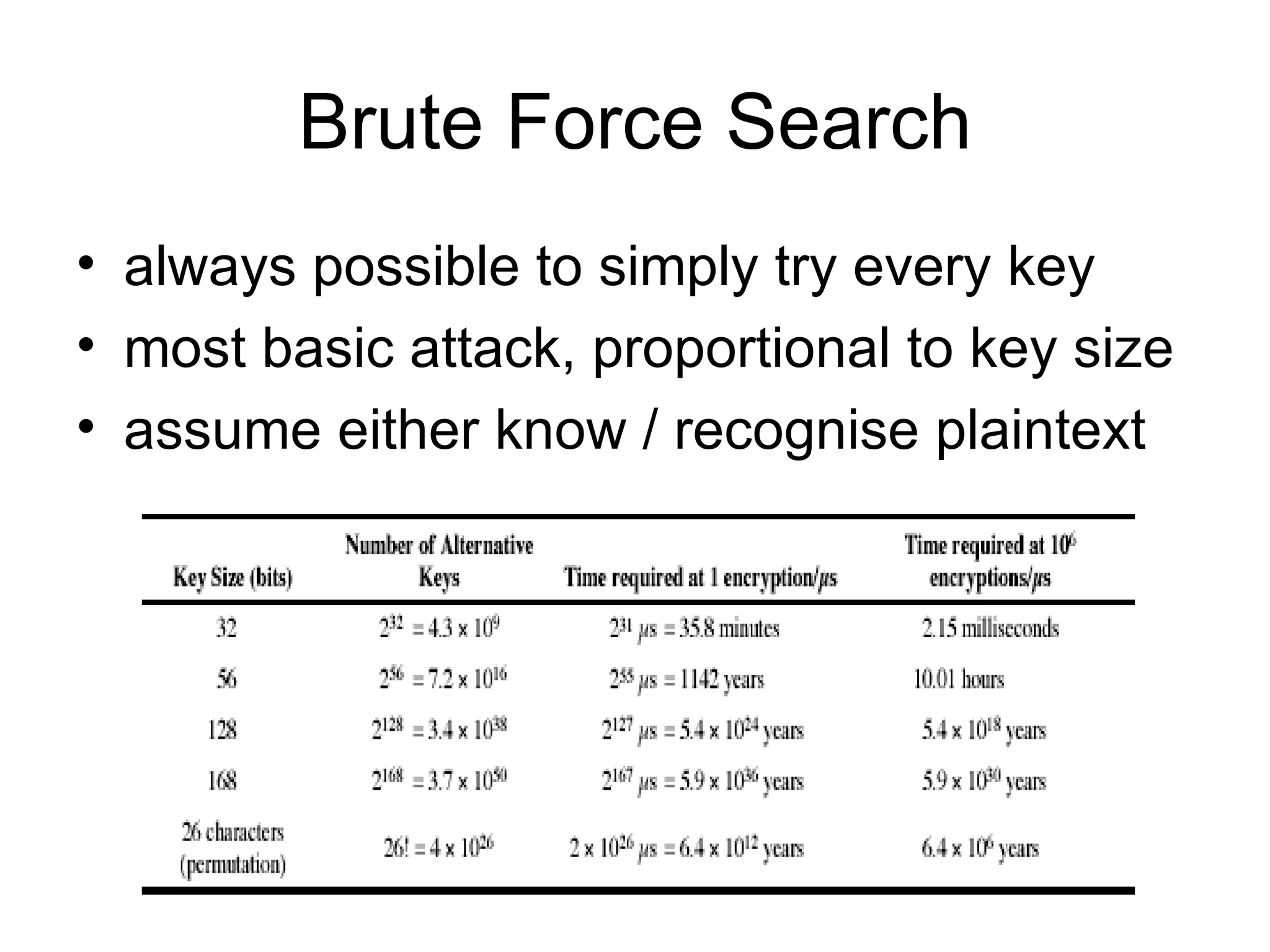
The document summarizes classical encryption techniques, including:
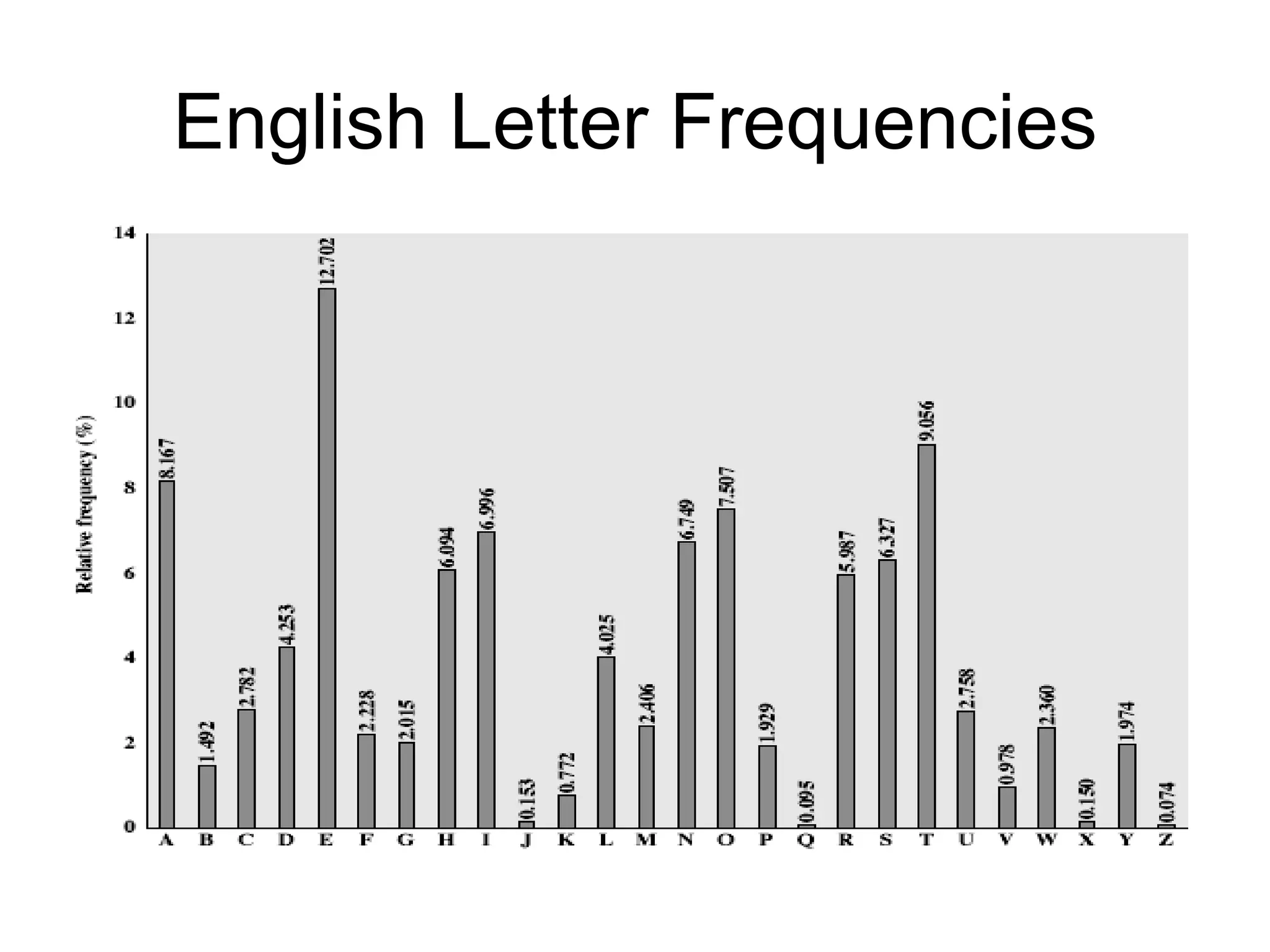
1) Monoalphabetic ciphers which encrypt one letter to another but can be broken through frequency analysis of letters.
2) The Playfair cipher which encrypts digrams and provides more security than monoalphabetic ciphers.
3) Polyalphabetic ciphers like the Vigenère cipher which use multiple cipher alphabets to provide even stronger security.