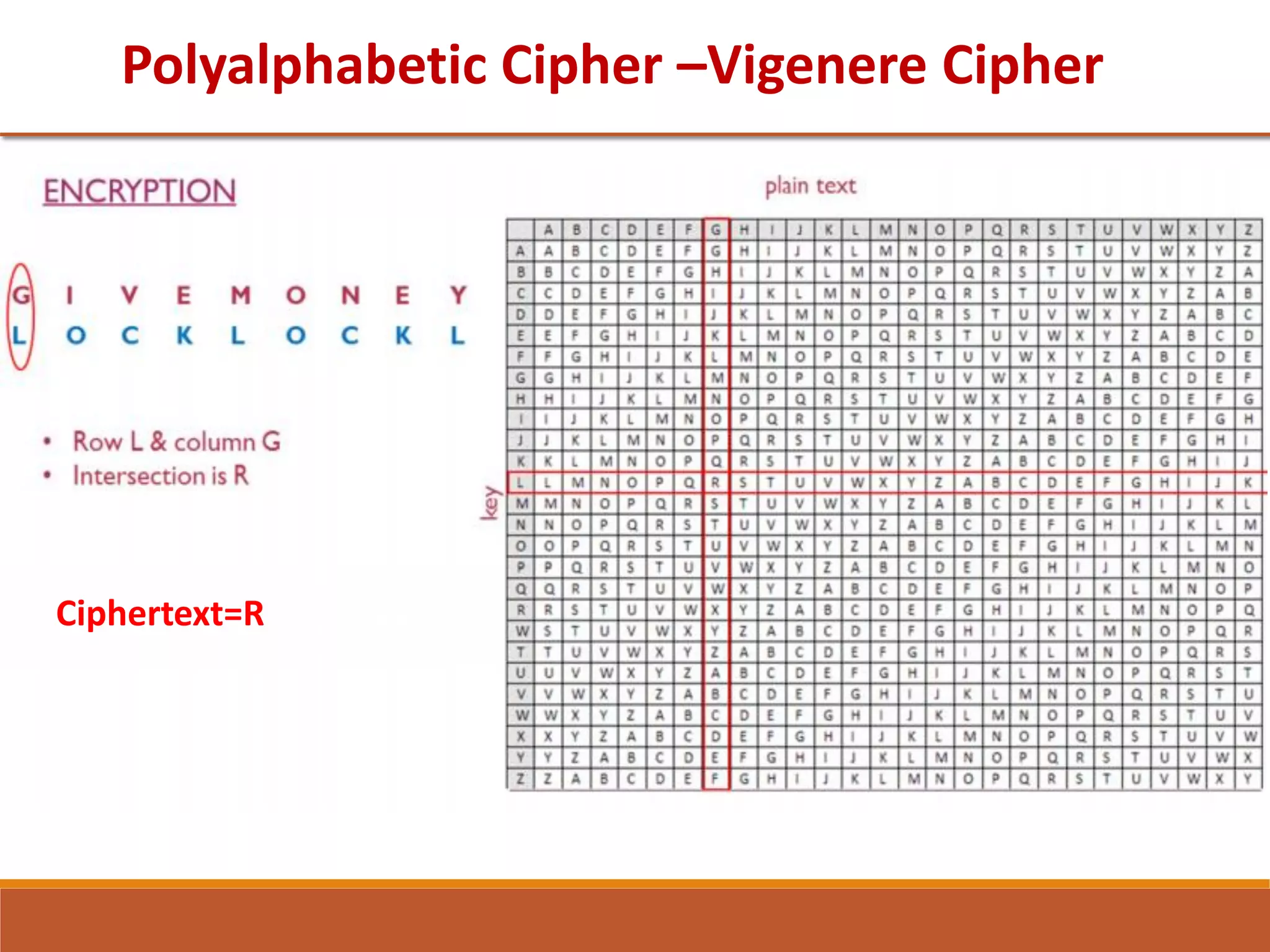
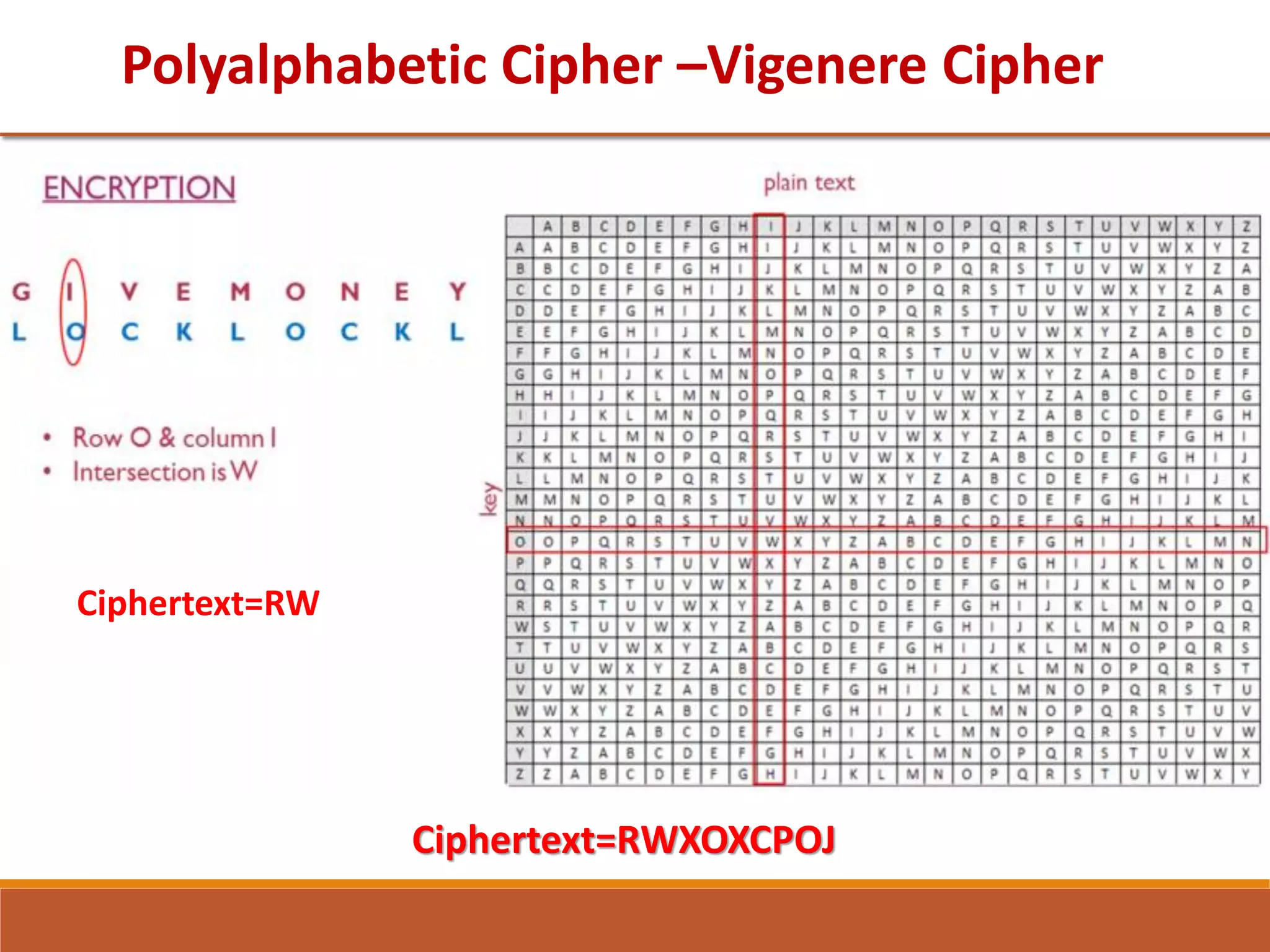
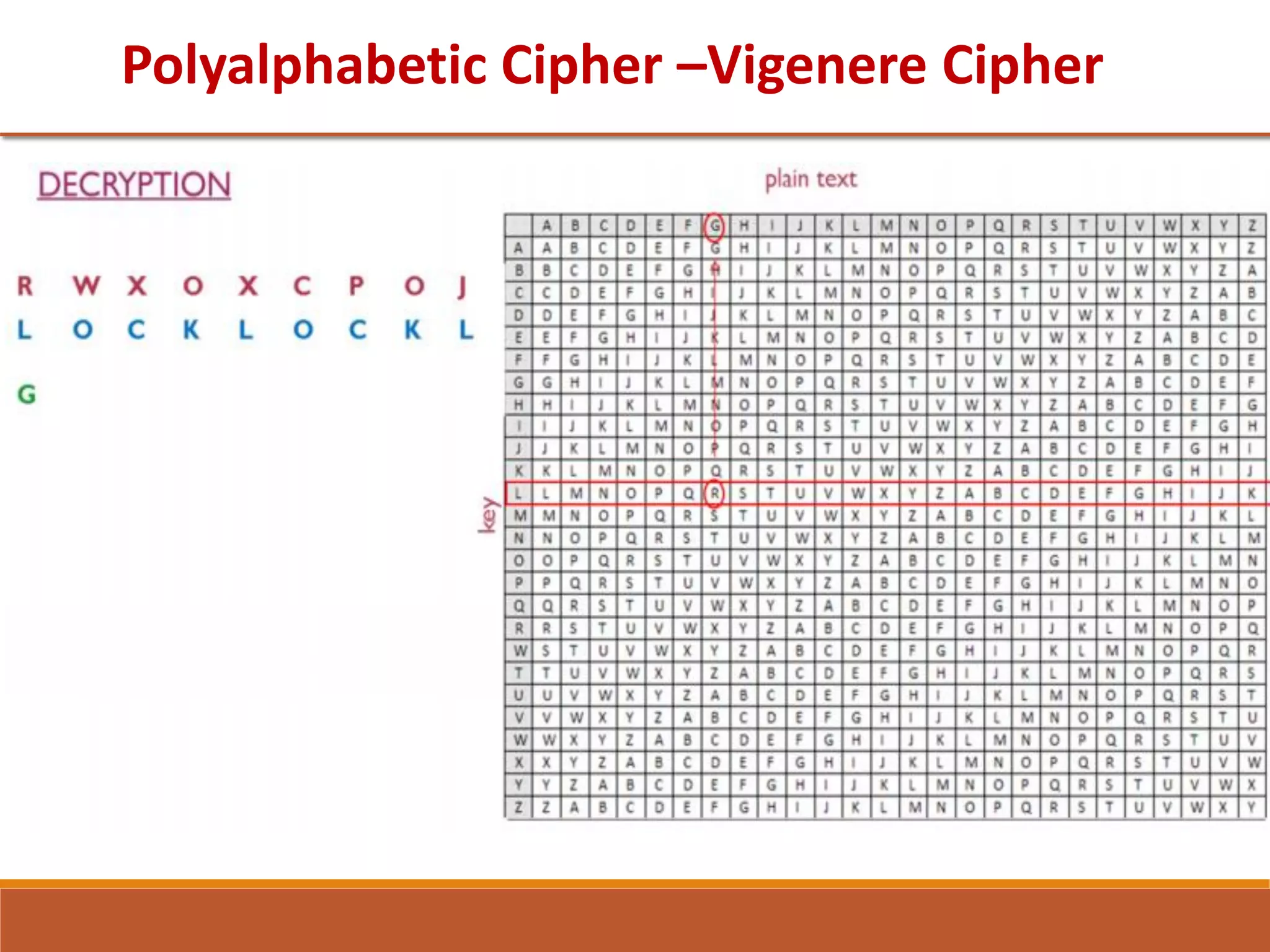
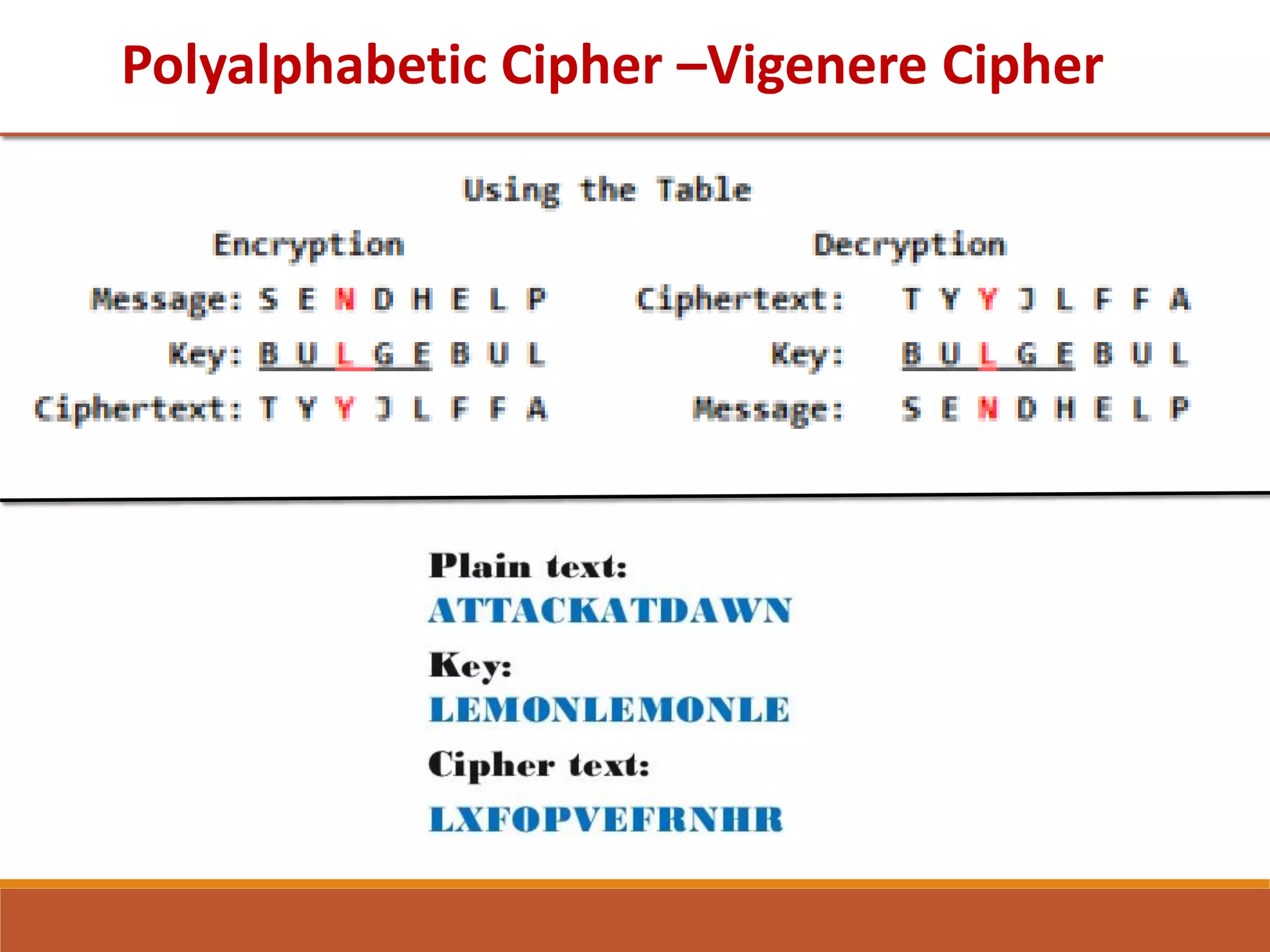
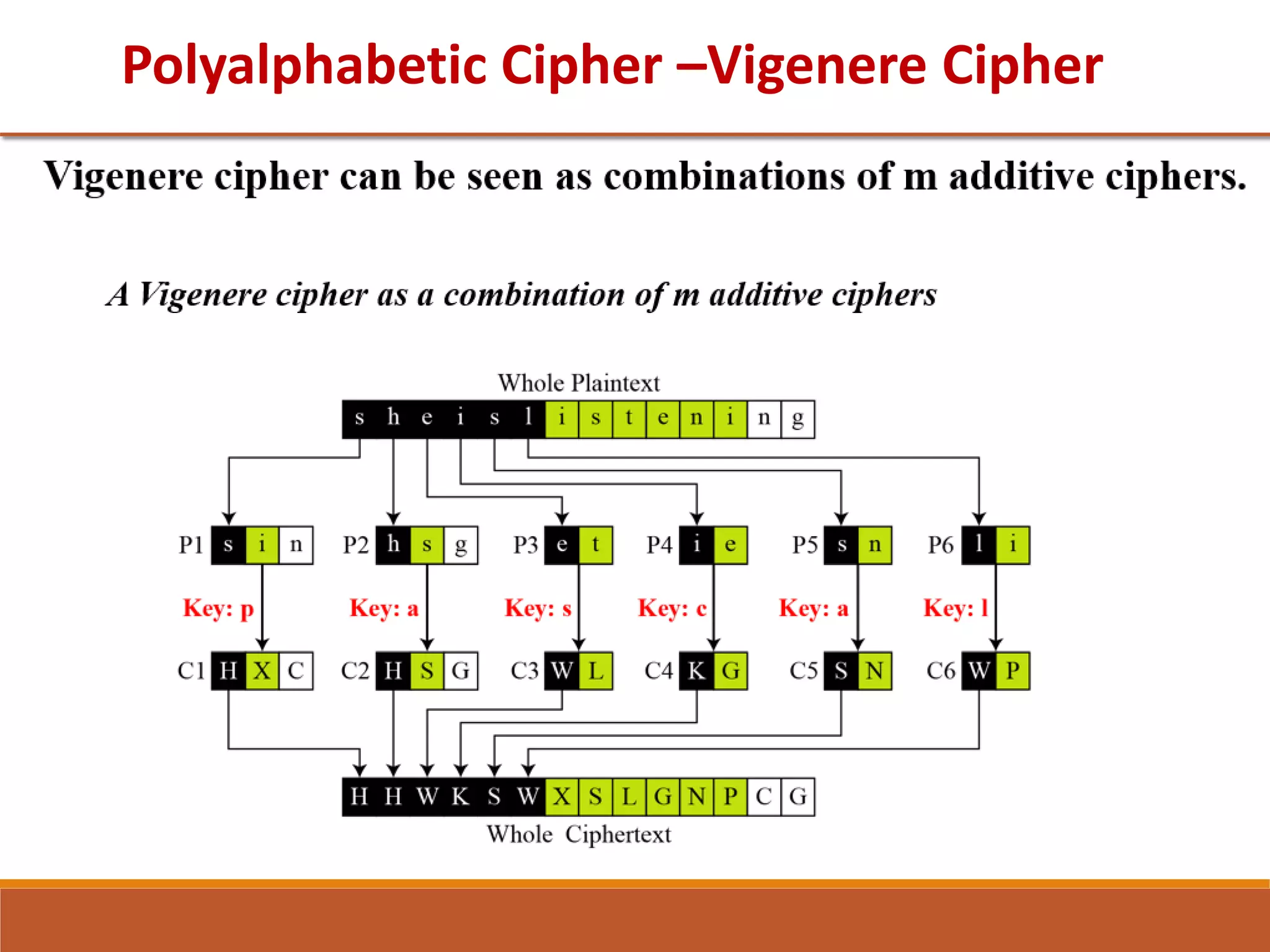
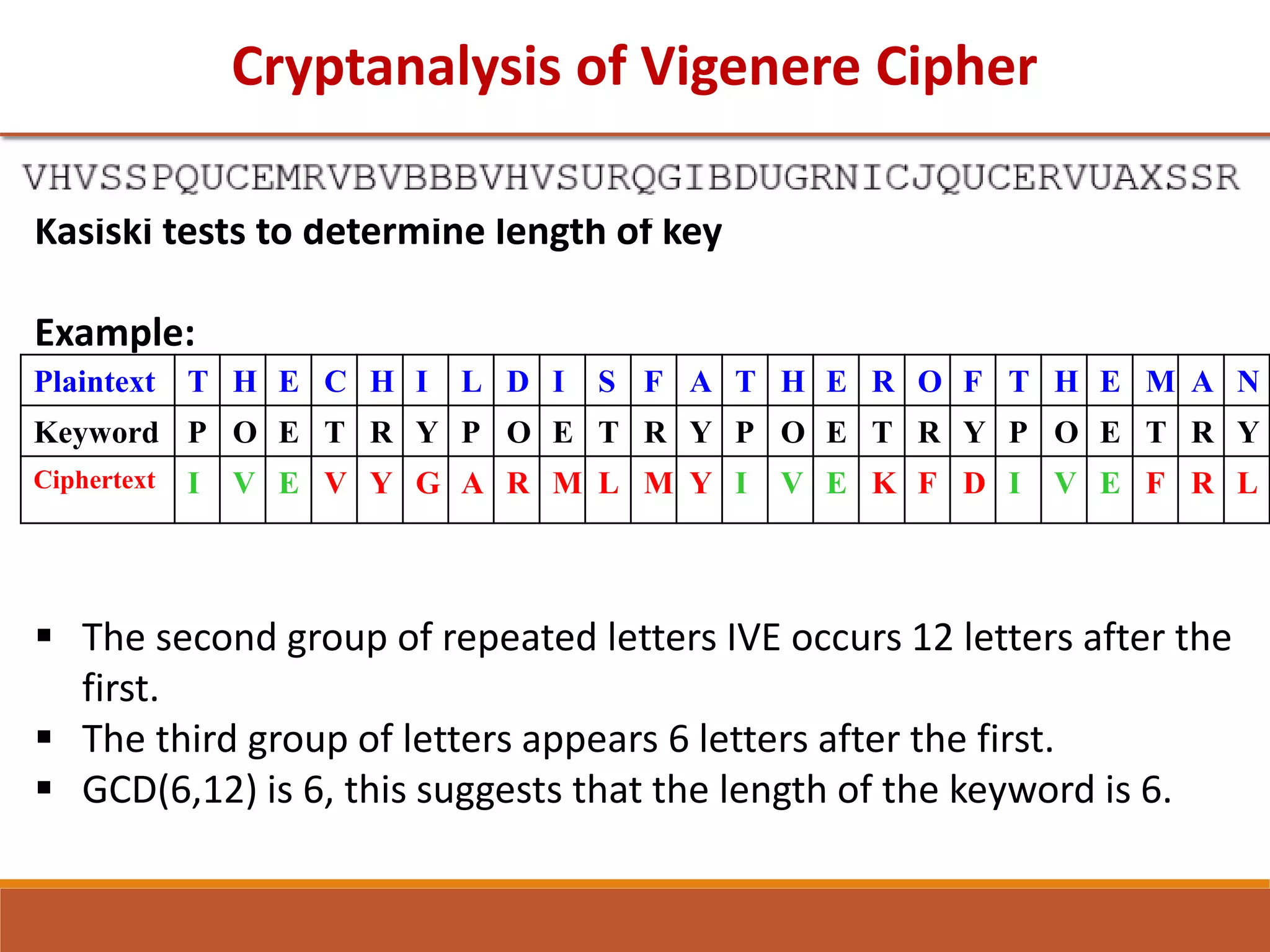
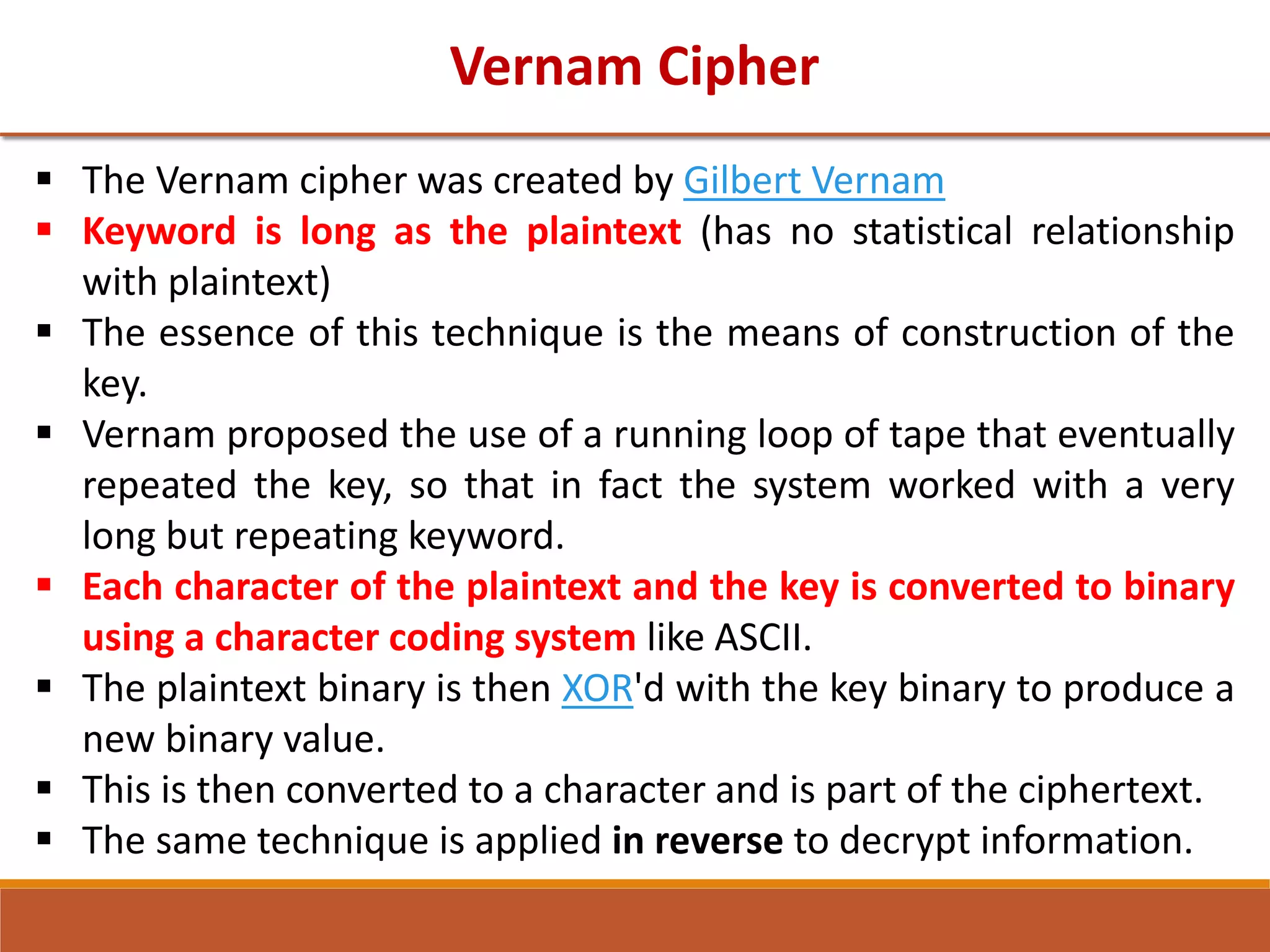
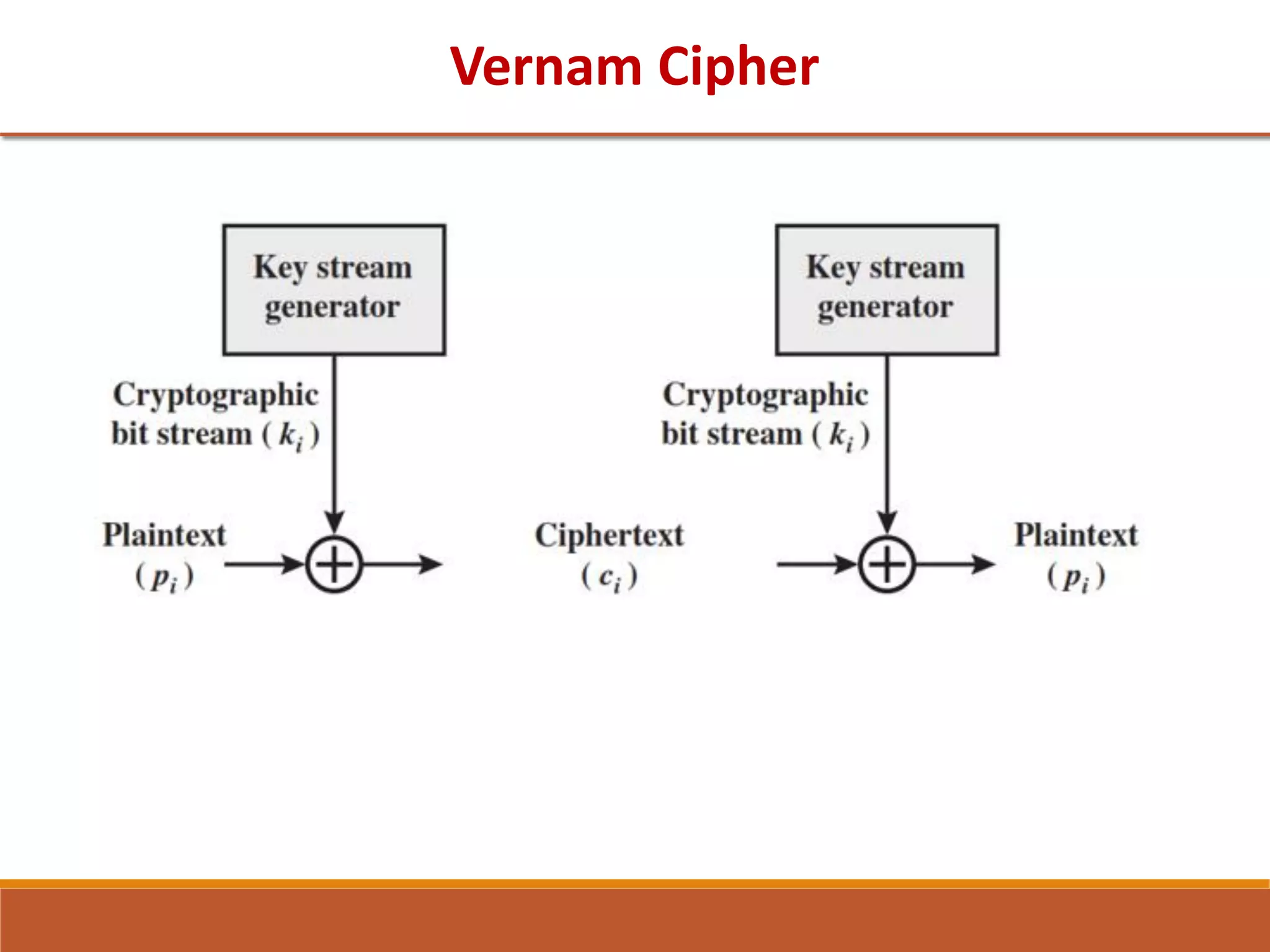
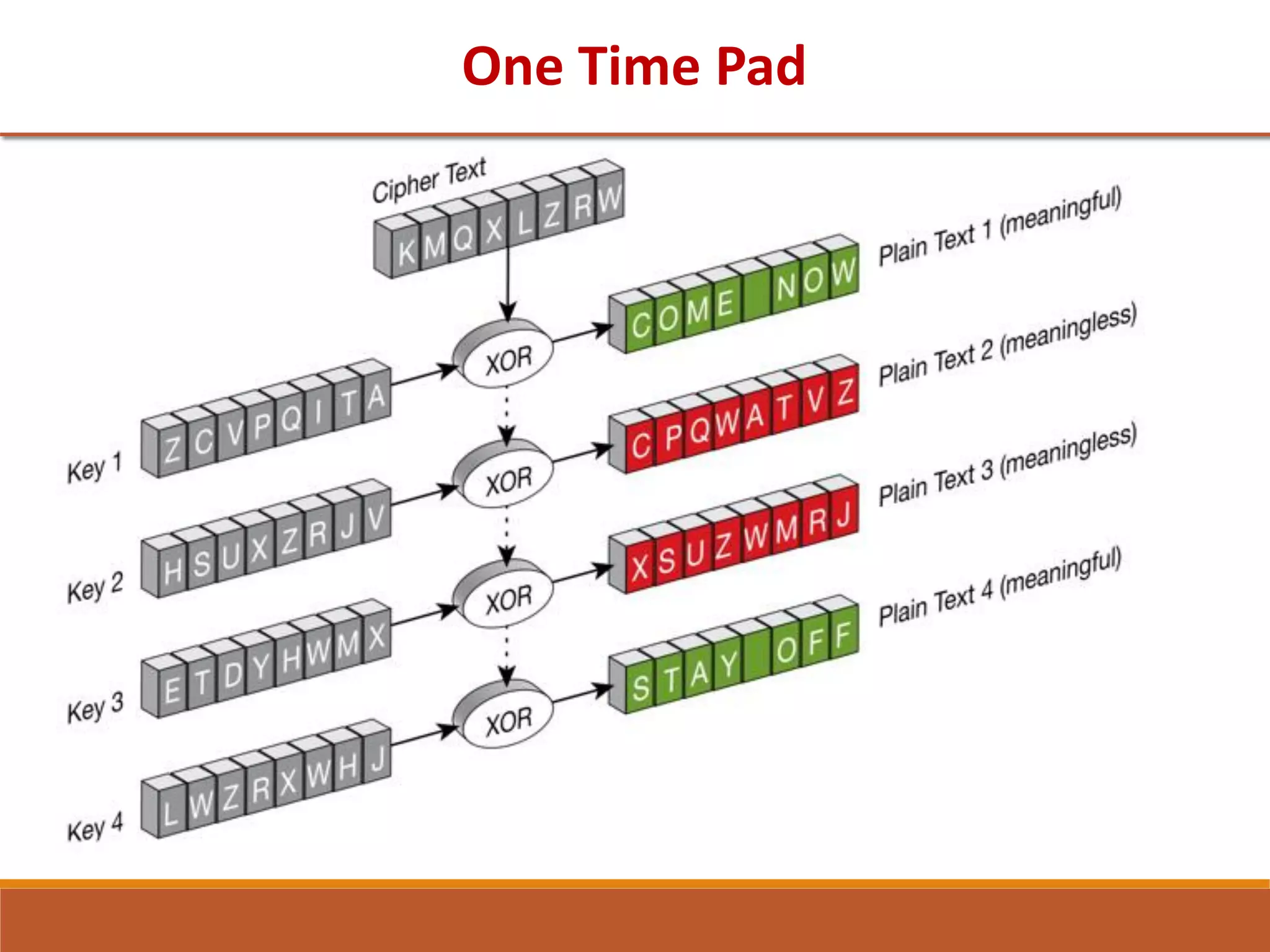
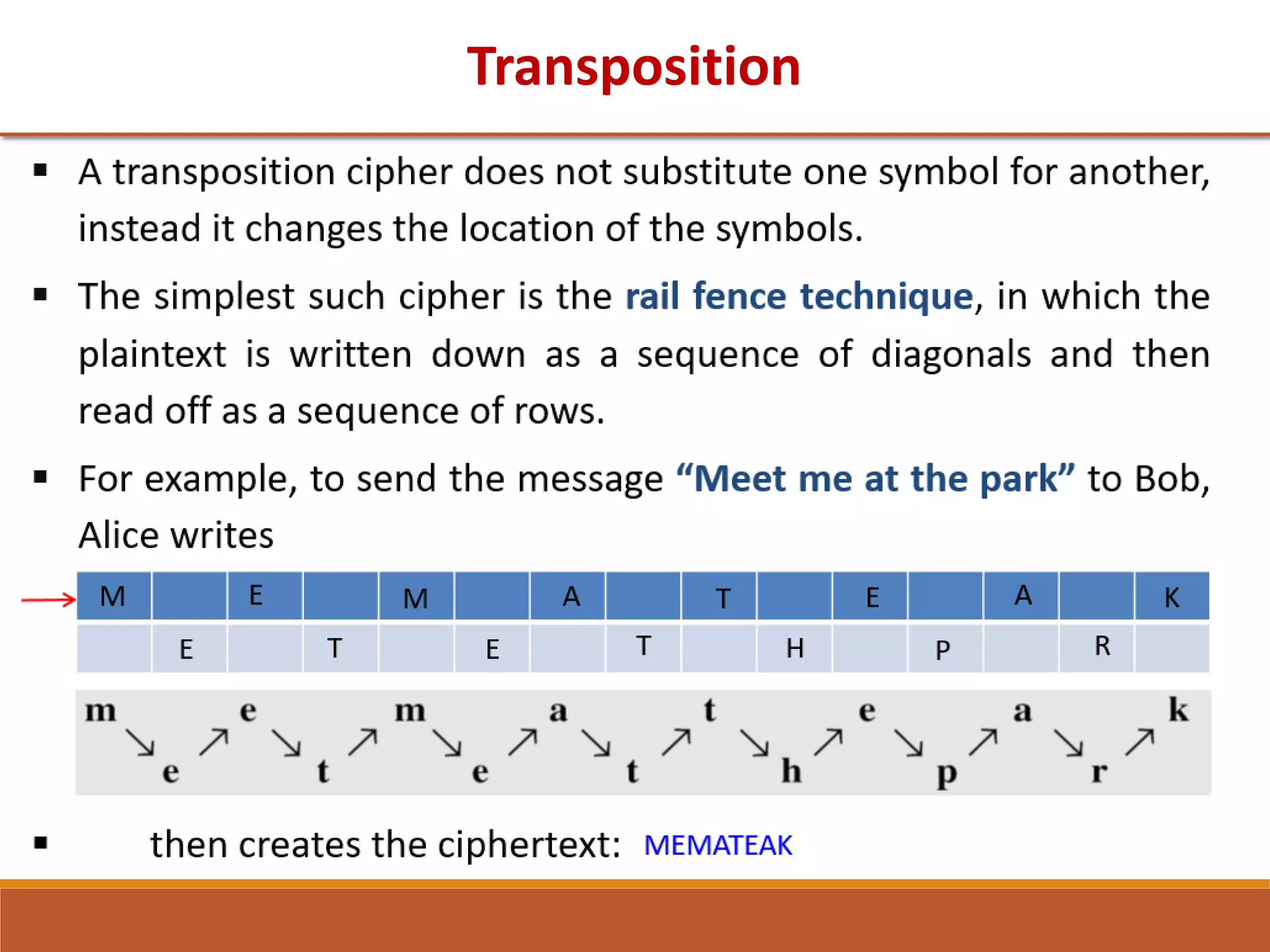
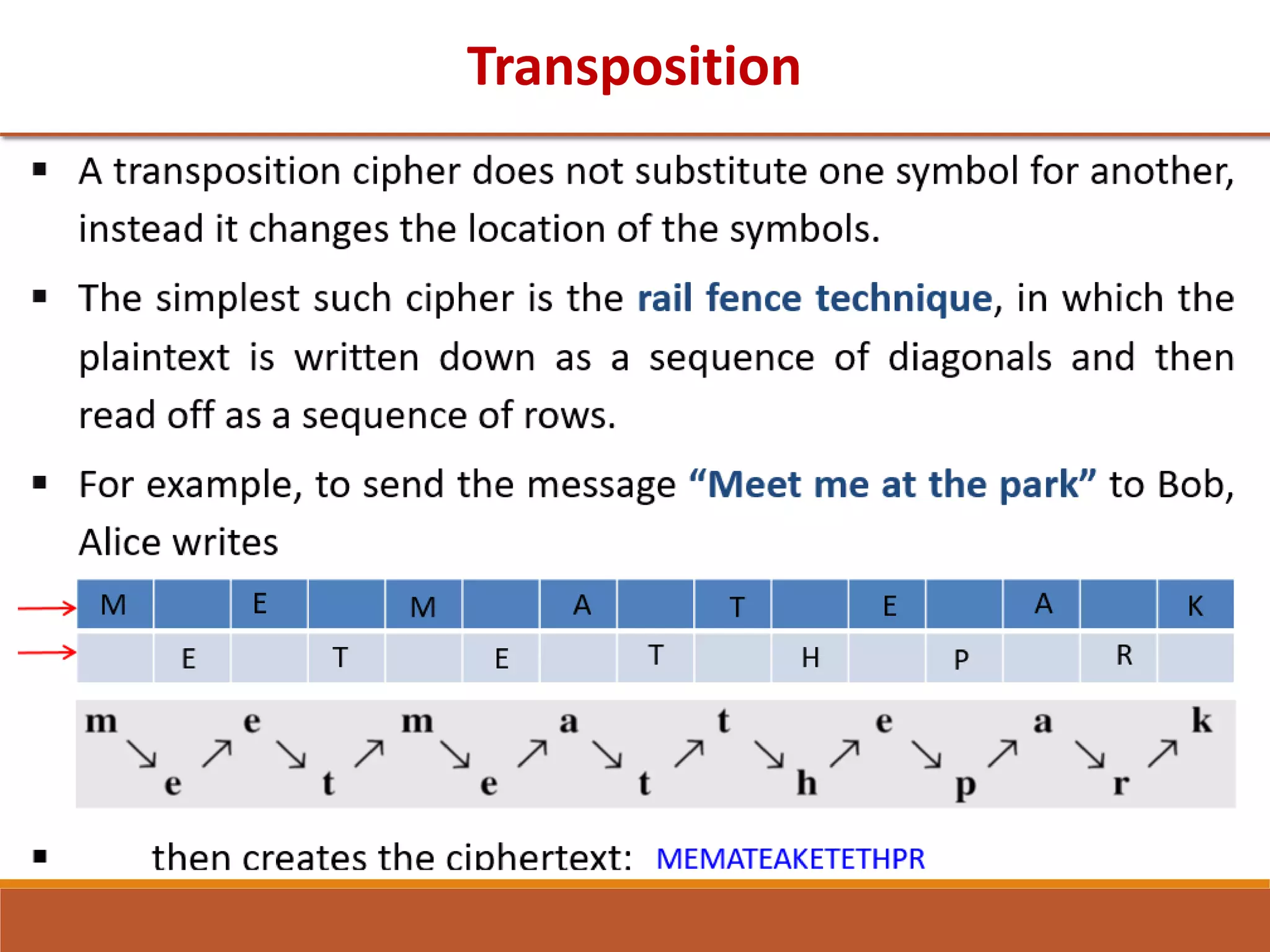
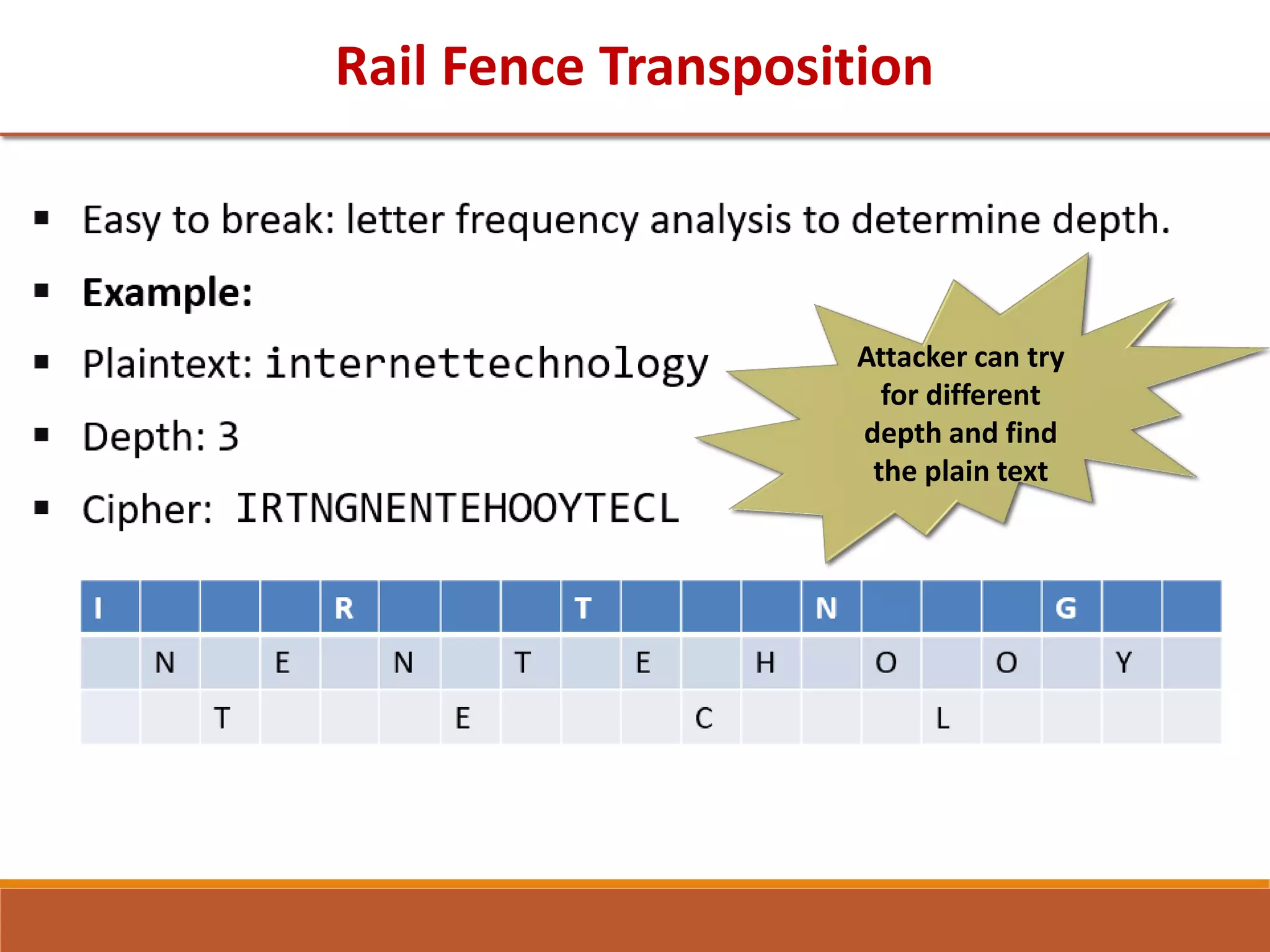
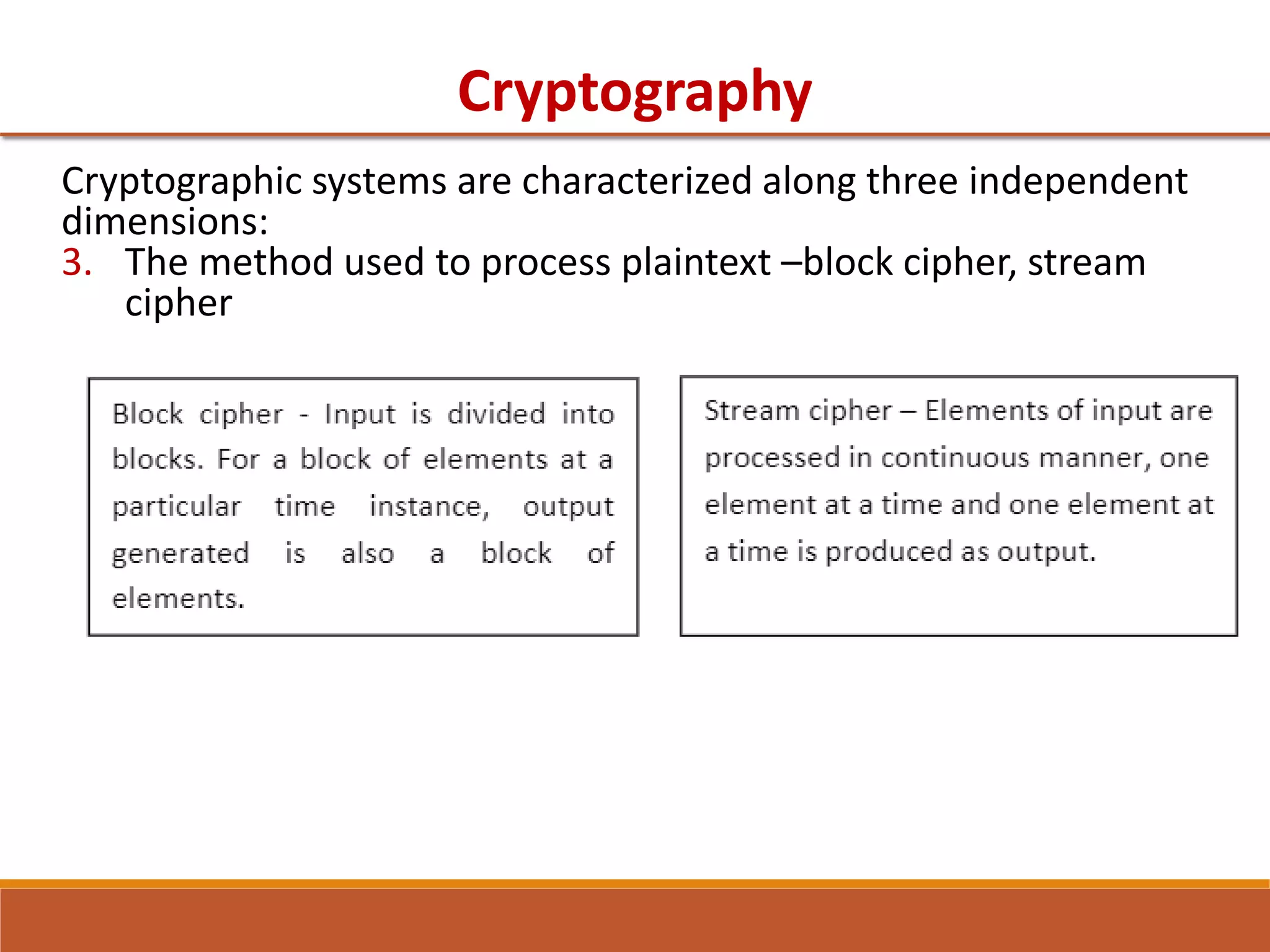
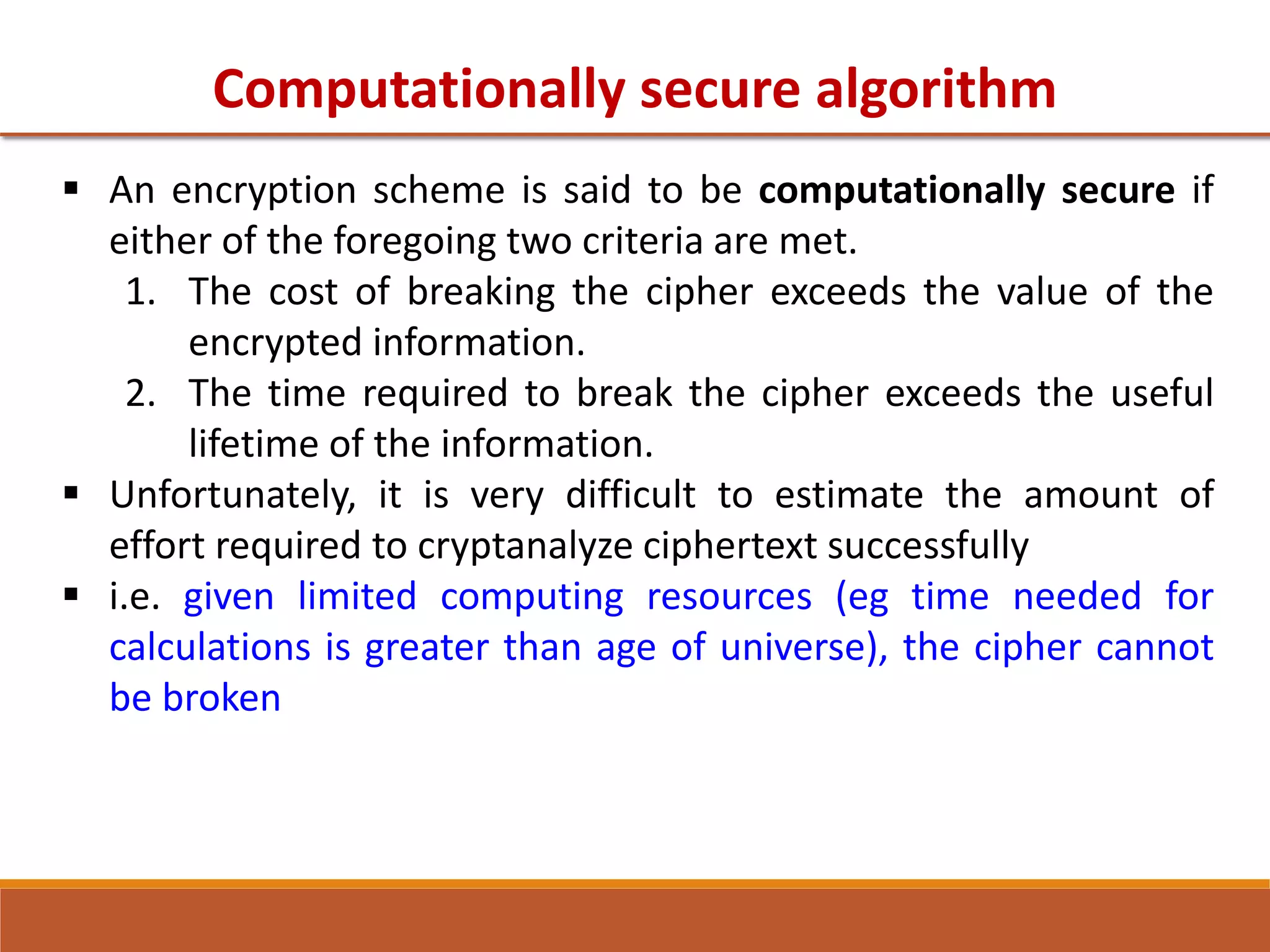
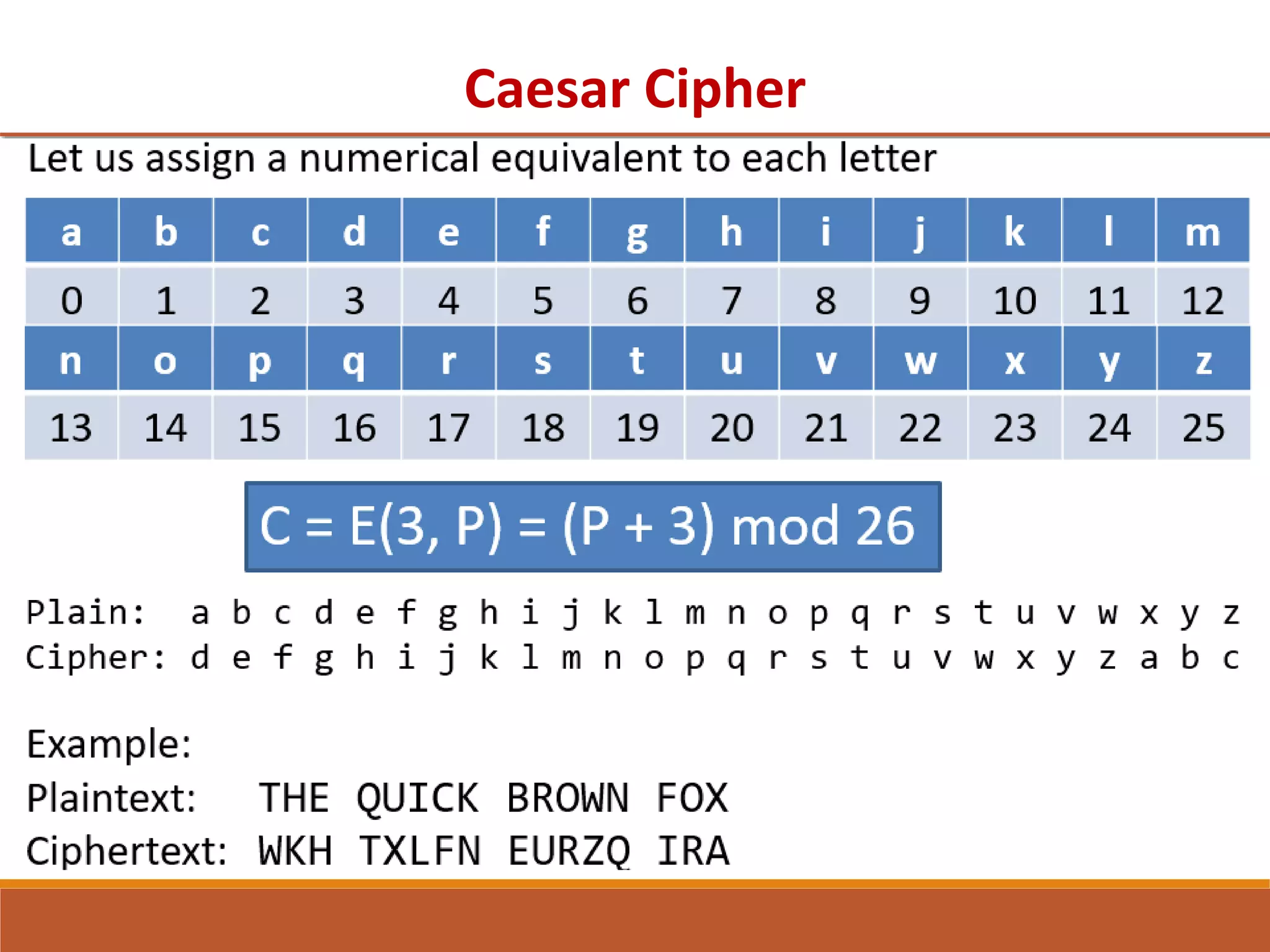
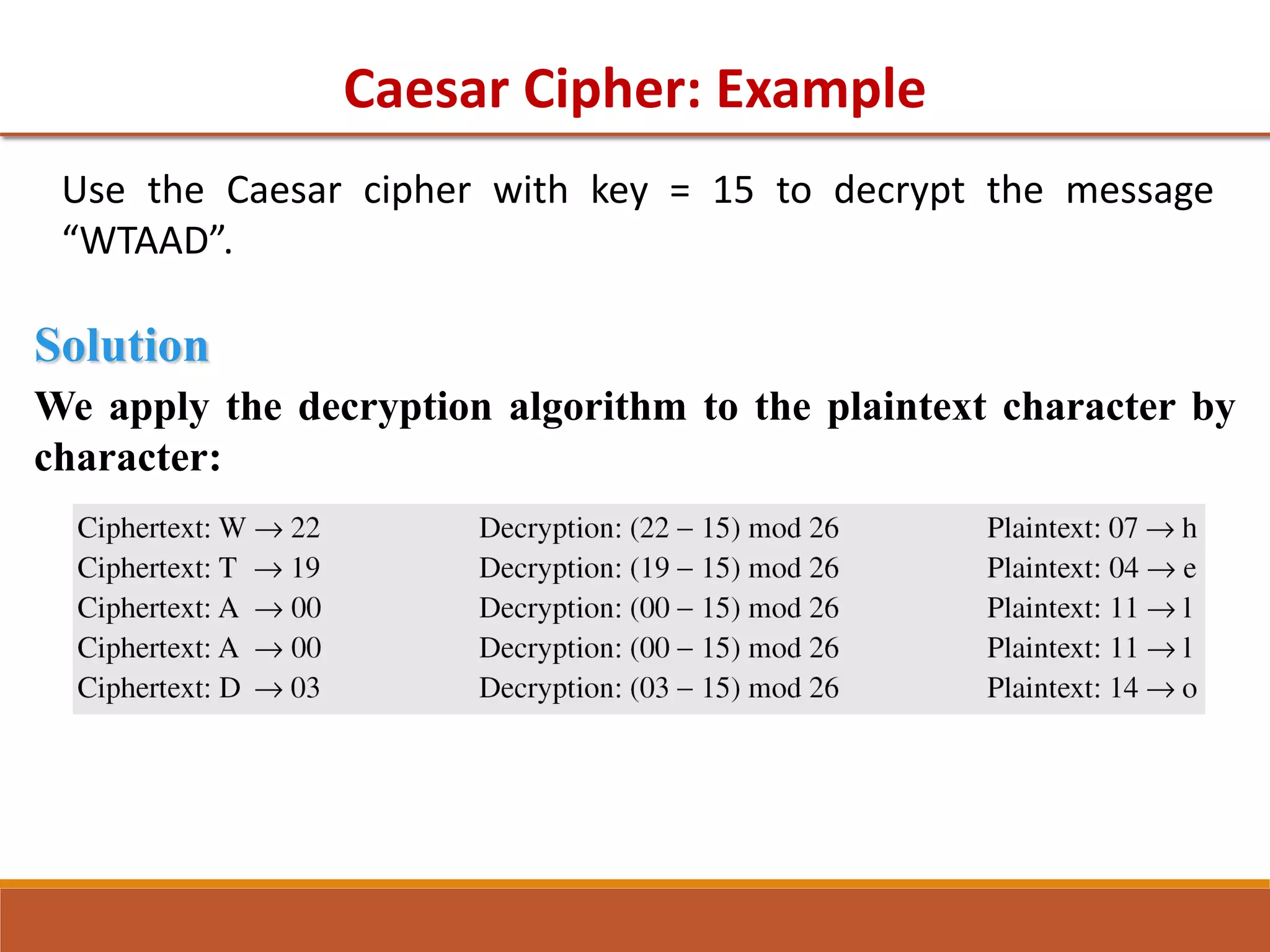
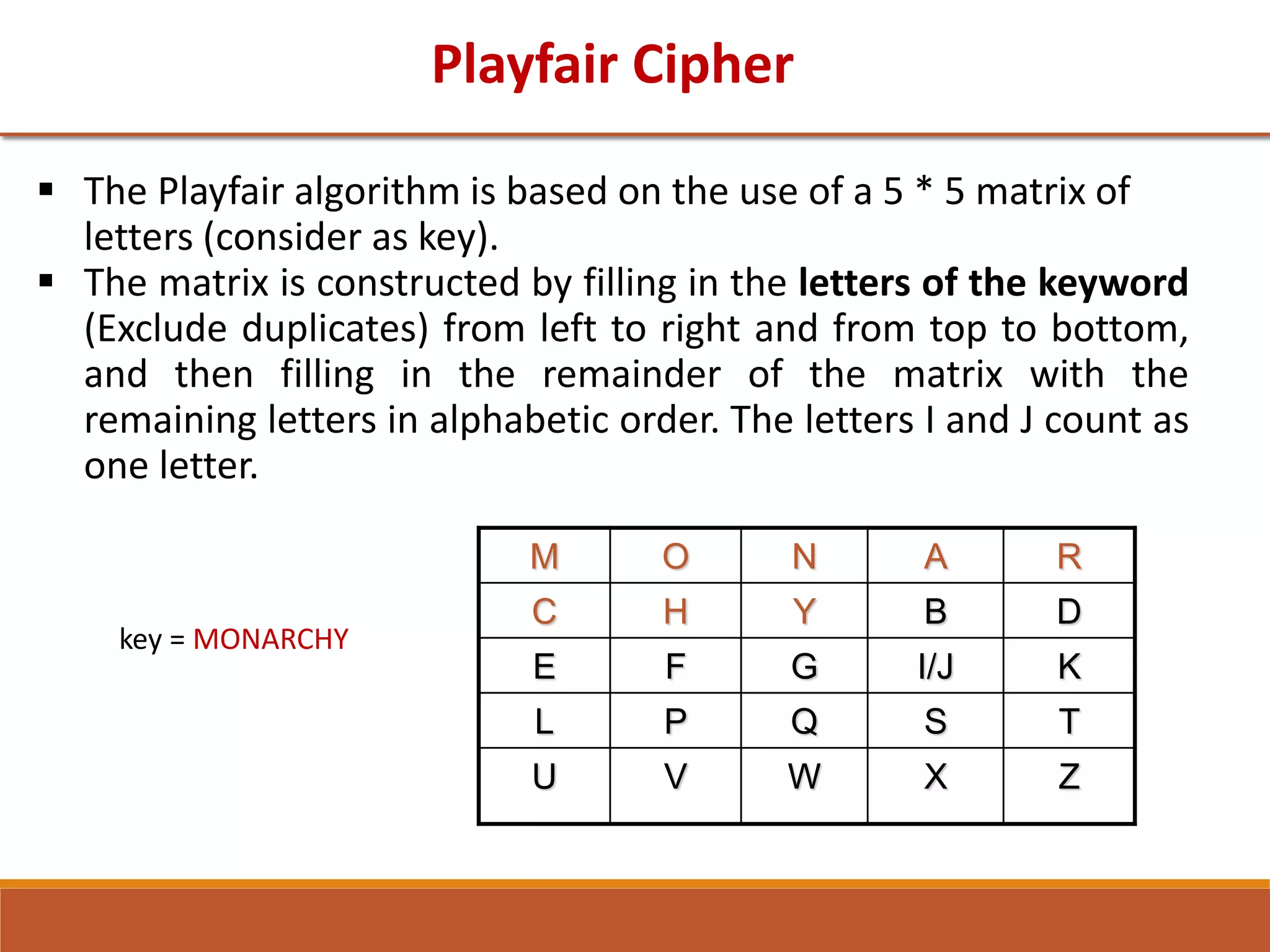
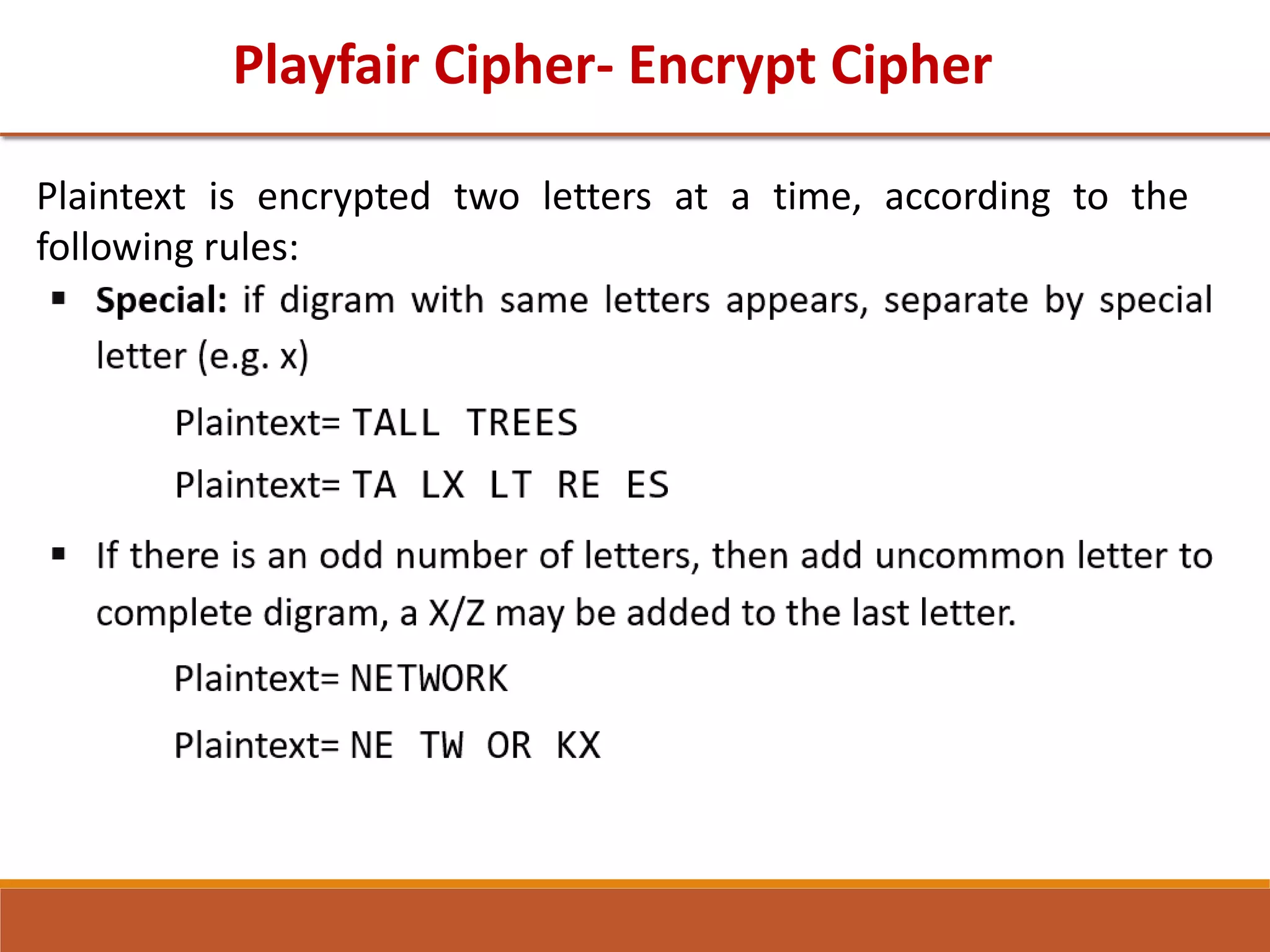
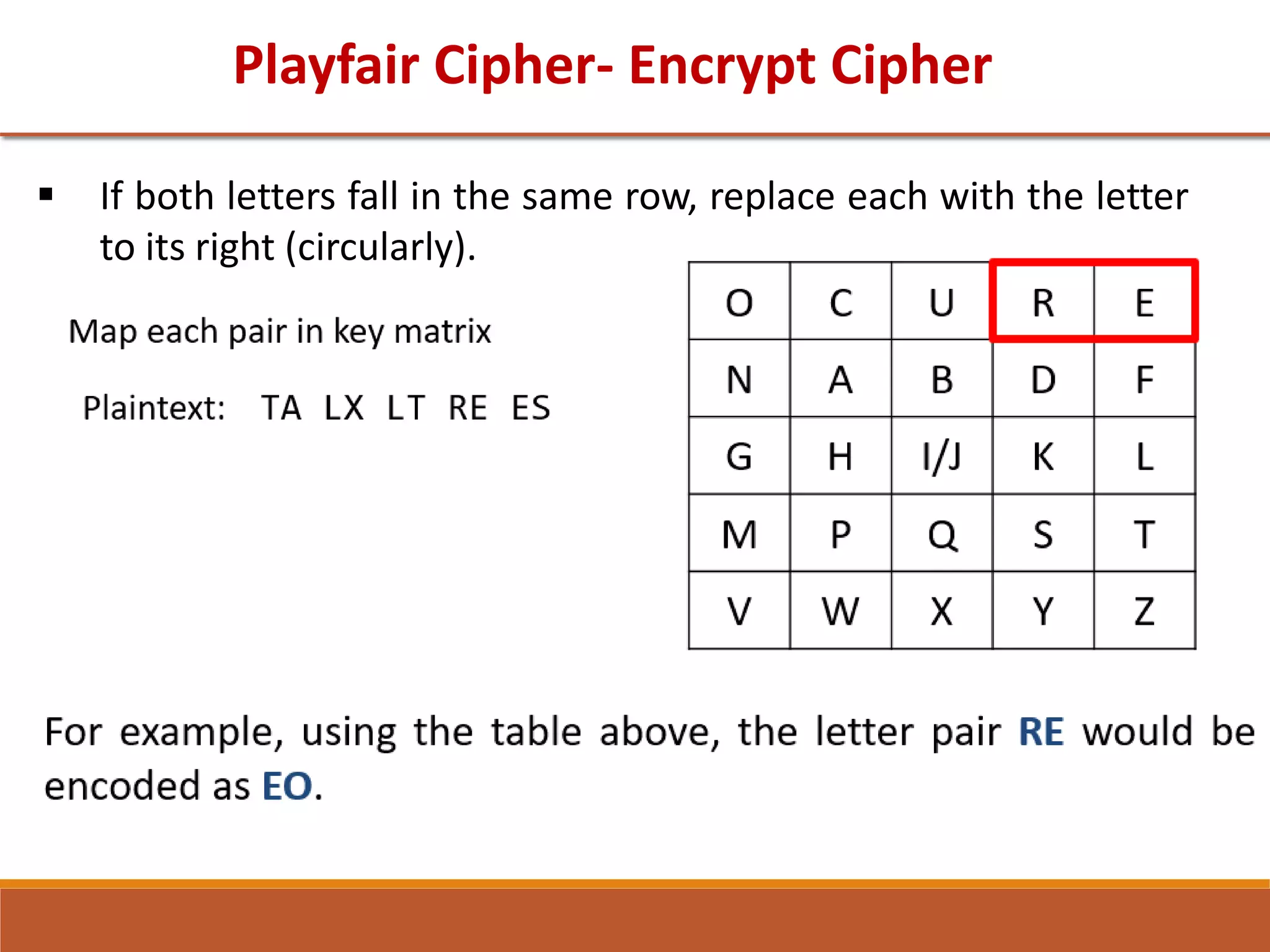
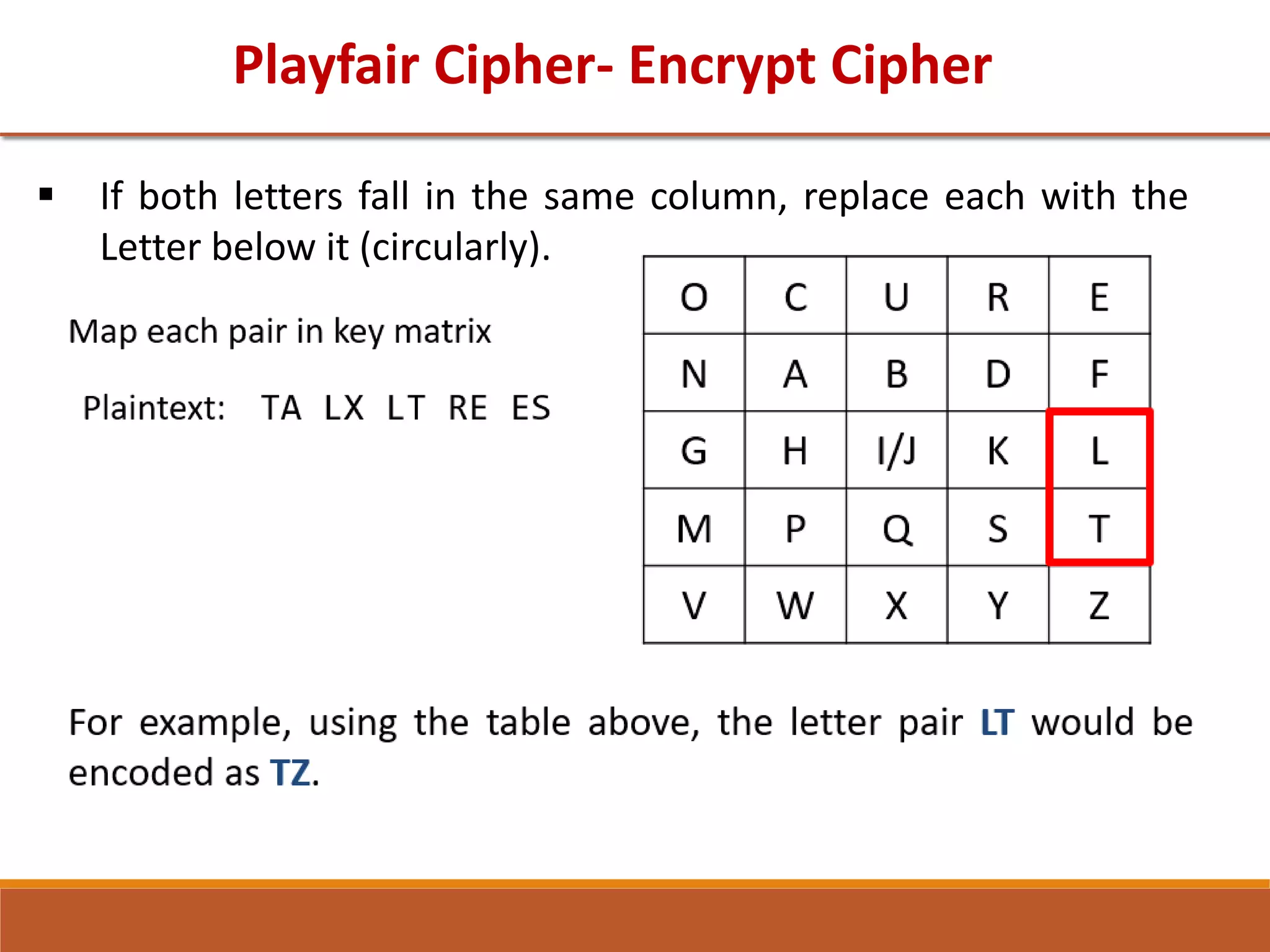
The document provides information on classical encryption techniques, specifically covering symmetric cipher models, cryptography, cryptanalysis, and attacks. It discusses substitution and transposition techniques, including the Caesar cipher, monoalphabetic cipher, and Playfair cipher. For each technique, it explains the encryption and decryption process, cryptanalysis methods, and provides examples to illustrate how the techniques work.










































![GTU Question
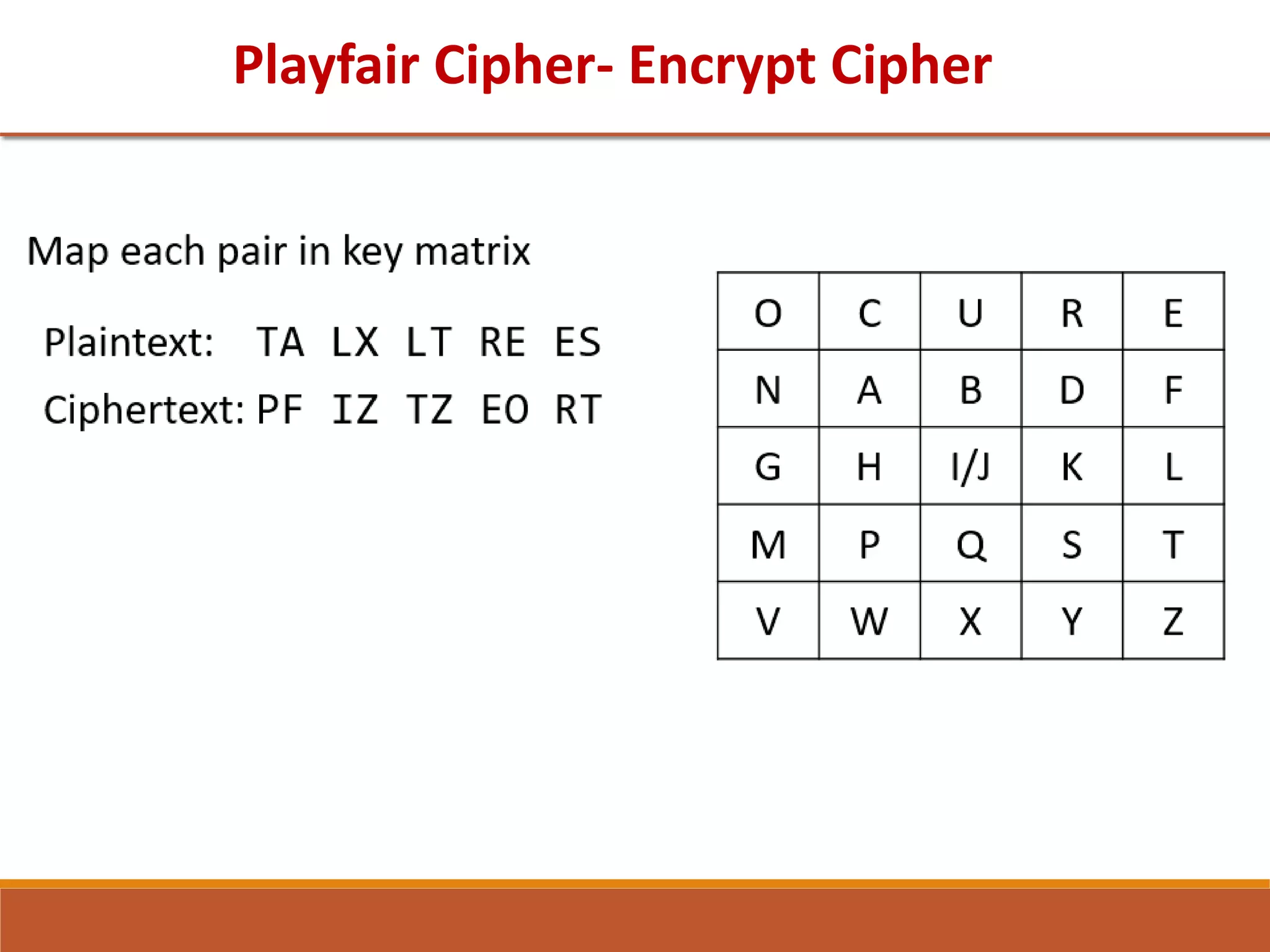
Encrypt the Message “Surgical Strike” with key “GUJAR” using
PLAYFAIR technique. [Winter 2018] [4 Marks]
Explain Playfair Cipher in detail. Find out cipher text for the
following given plain text and key. [Winter 2017] [7 Marks]
Key = GOVERNMENT
Plain text = PLAYFAIR
Use the key “hidden” and encrypt the message “Message” using
playfair cipher. [Summer 2019] [7 Marks]
Explain playfair cipher substitution technique in detail. Find out
cipher text for the following given key and plaintext. [Summer
2017] [7 Marks]
Key = ENGINEERING
Plaintext=COMPUTER](https://image.slidesharecdn.com/unit1-211122112533/75/Unit-1-62-2048.jpg)
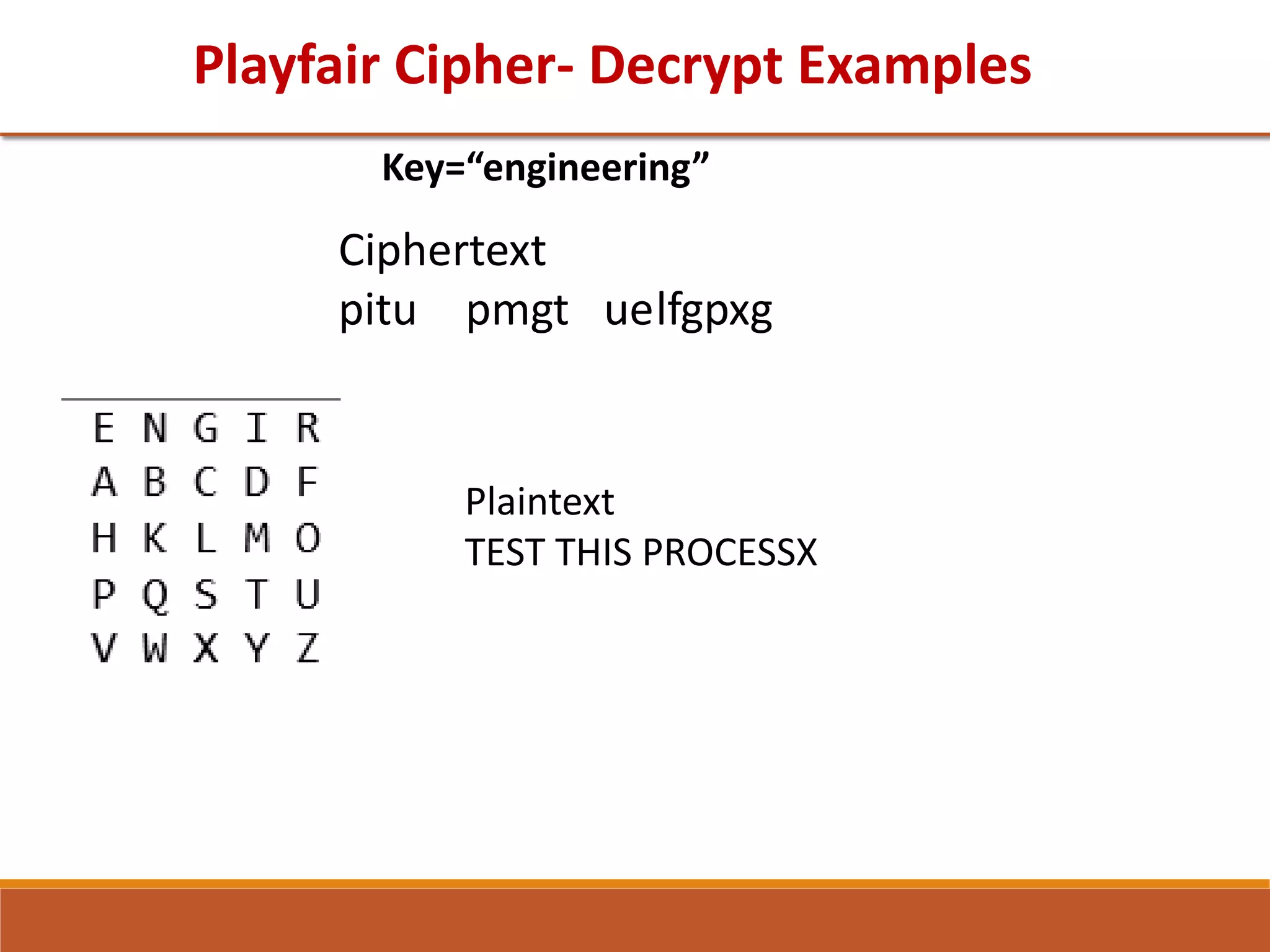
![GTU Question
Perform encryption in Playfair Cipher algorithm with plain text as
“INFORMATION AND NETWORK SECURITY”, Keyword is
“MONARCHY”. (Note: 1.Put j and i both combine as a single field in
5*5 matrix) [ Winter 2019] [07 Marks]](https://image.slidesharecdn.com/unit1-211122112533/75/Unit-1-63-2048.jpg)

![for (i = 0; i < strlen(str); i++) {
if (str[i] == 'J') str[i] = 'I';
if (str[i + 1] == '0') playfair(str[i], 'X', key);
else {
if (str[i + 1] == 'J') str[i + 1] = 'I';
if (str[i] == str[i + 1]) playfair(str[i], 'X', key);
else {
playfair(str[i], str[i + 1], key);
i++;
}
}
}](https://image.slidesharecdn.com/unit1-211122112533/75/Unit-1-65-2048.jpg)
![Playfair function
Step 1 : Find the position of Diagram into Key matrix
void playfair(char ch1, char ch2, char key[MX][MX]) {
int i, j, w, x, y, z;
for (i = 0; i < MX; i++) {
for (j = 0; j < MX; j++) {
if (ch1 == key[i][j]) { // First char in diagram
w = i;
x = j;
} else if (ch2 == key[i][j]) { // second char in diagram
y = i;
z = j;
}
}
}](https://image.slidesharecdn.com/unit1-211122112533/75/Unit-1-66-2048.jpg)
![Playfair function
Step 2 : Both char in Diagram are in same row
if (w == y) {
if(choice==1){
//encryption --same row - move right // change column
x = (x + 1) % 5;
z = (z + 1) % 5;
}
else{
//decryption -- same row - move left
x = ((x - 1)+5)%5;
z = ((z - 1)+5)%5;
}
printf("%c%c", key[w][x], key[y][z]);
}](https://image.slidesharecdn.com/unit1-211122112533/75/Unit-1-67-2048.jpg)
![Playfair function
Step 3 : Both char in Diagram are in same Column
else if (x == z) {
if(choice==1){
//encryption --same col - move down //change row
w = (w + 1) % 5;
y = (y + 1) % 5;
}
else{
//Decryption --same col - move Up //change row
w = ((w - 1)+5)%5;
y = ((y - 1) +5)%5;
}
printf("%c%c", key[w][x], key[y][z]);
}](https://image.slidesharecdn.com/unit1-211122112533/75/Unit-1-68-2048.jpg)
![Playfair function
Step 4 : Both char in Diagram are not in same row and col
else {
printf("%c%c", key[w][z], key[y][x]);
}](https://image.slidesharecdn.com/unit1-211122112533/75/Unit-1-69-2048.jpg)


















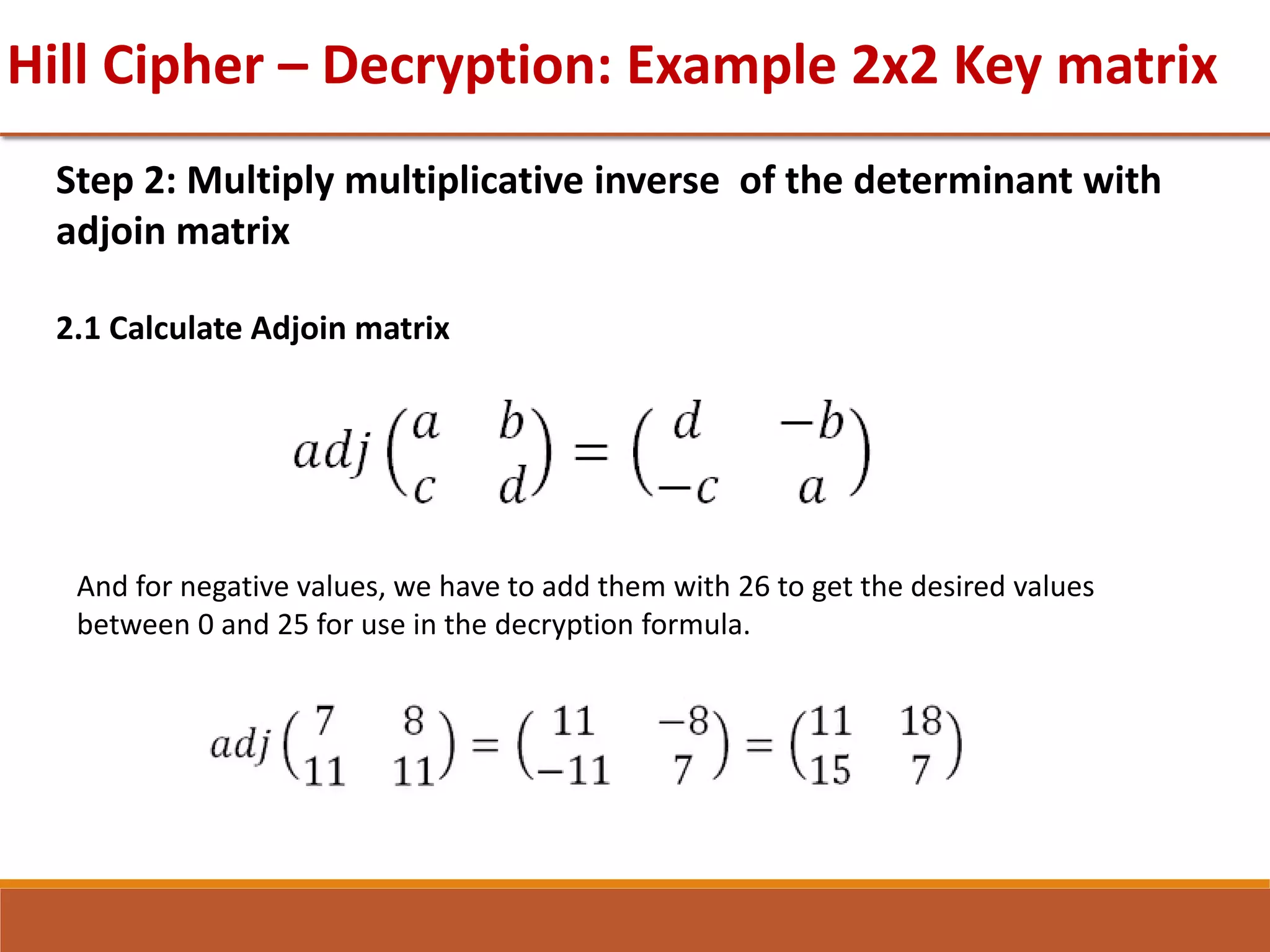

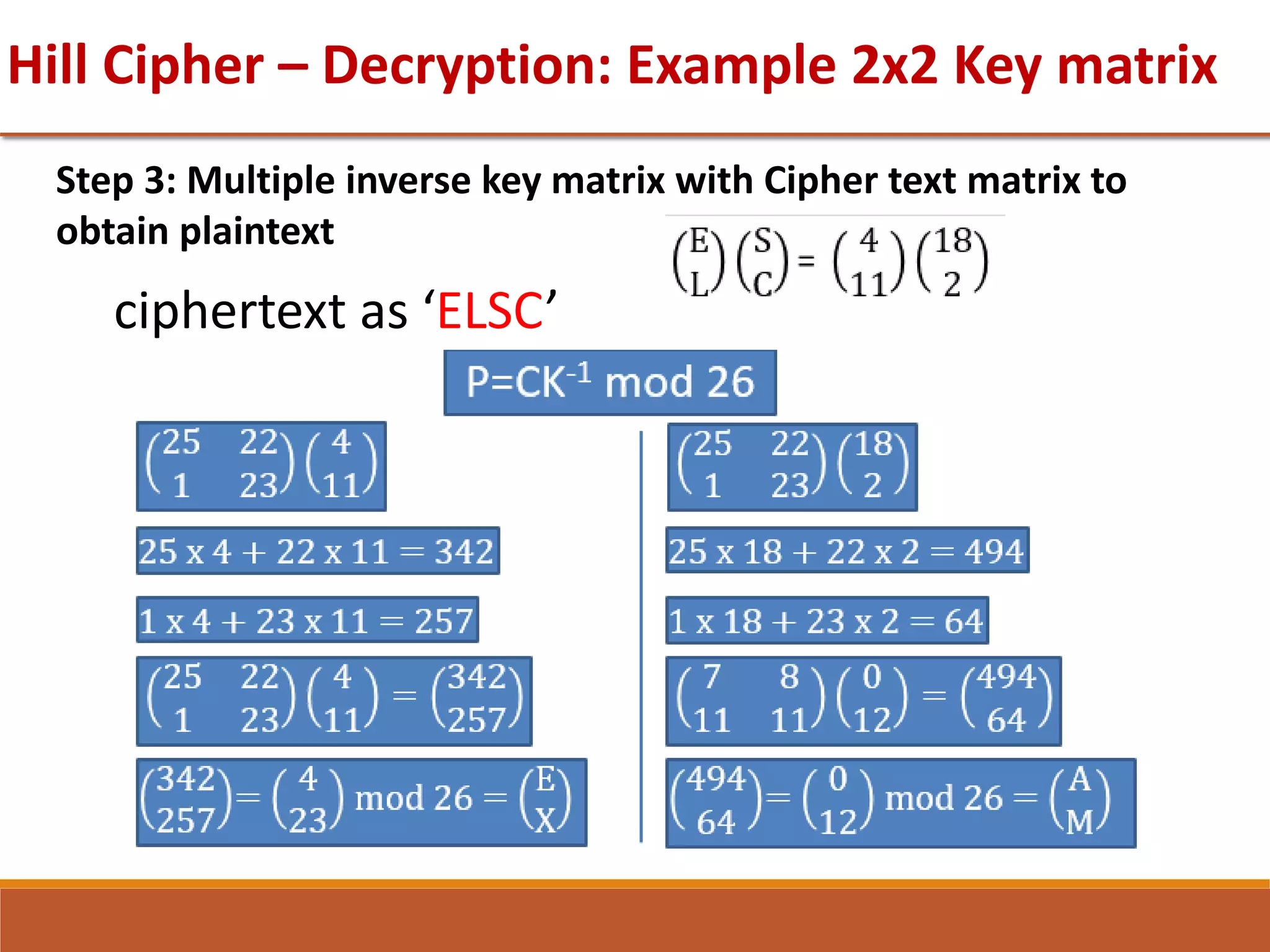



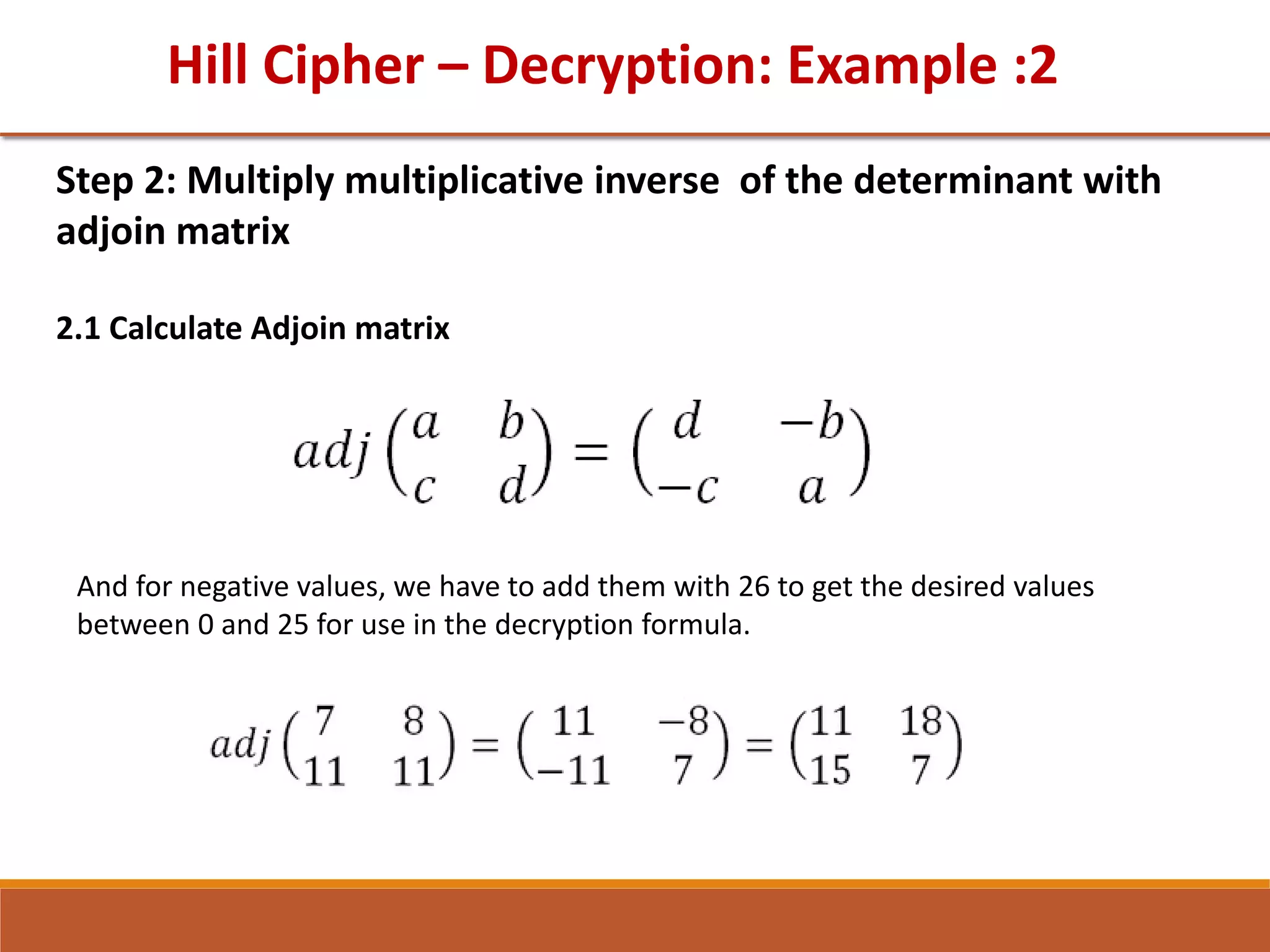
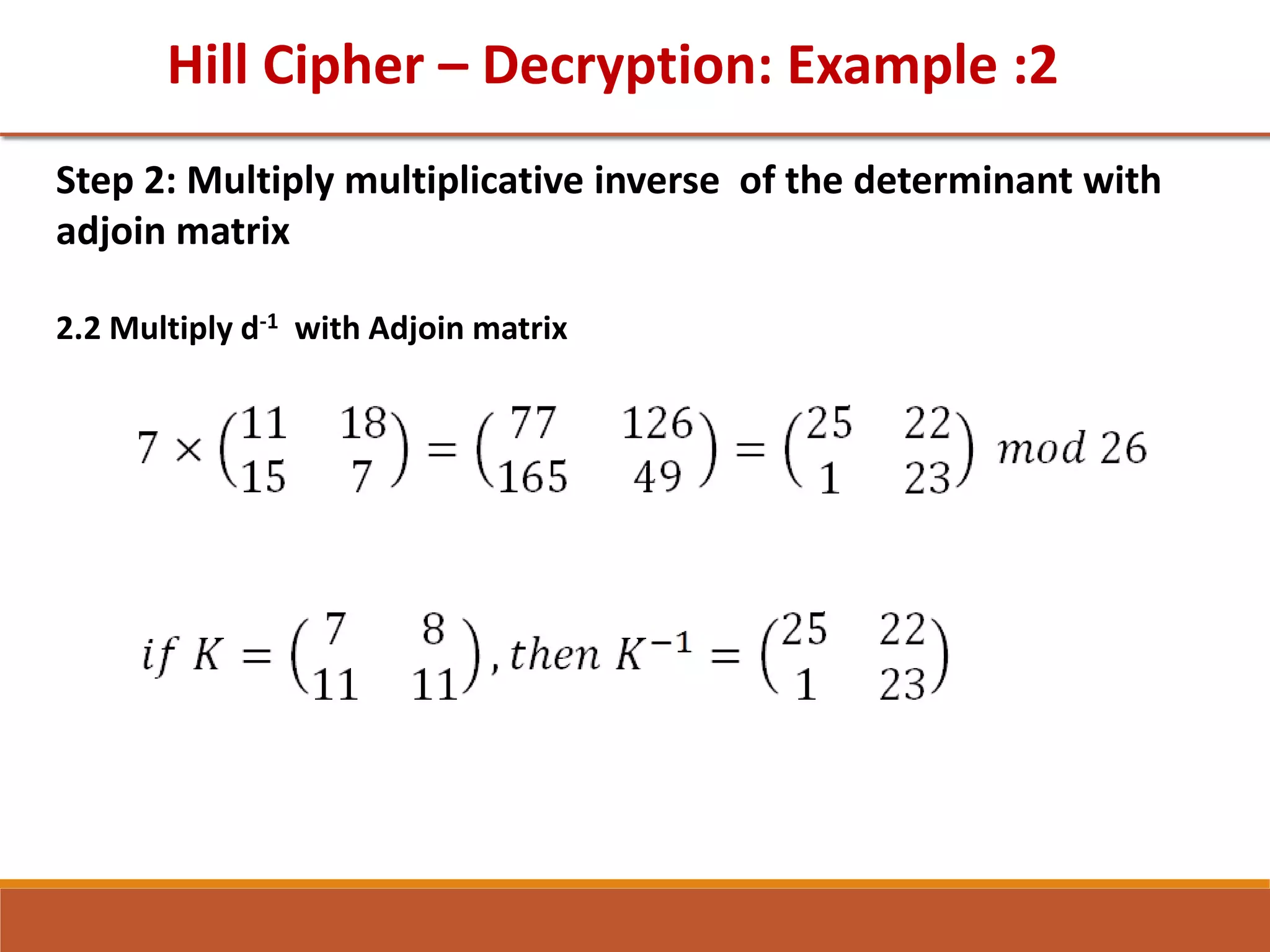


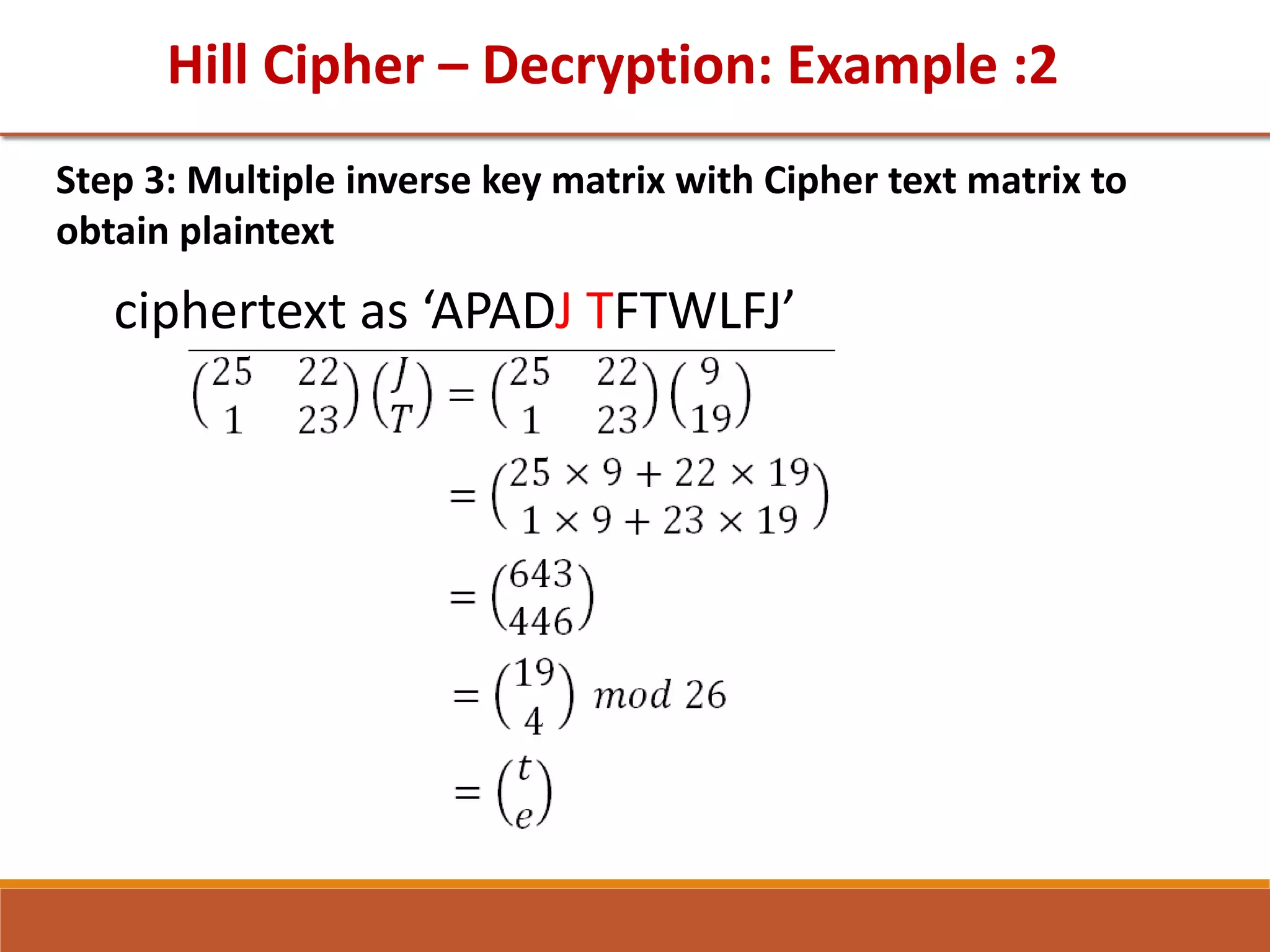
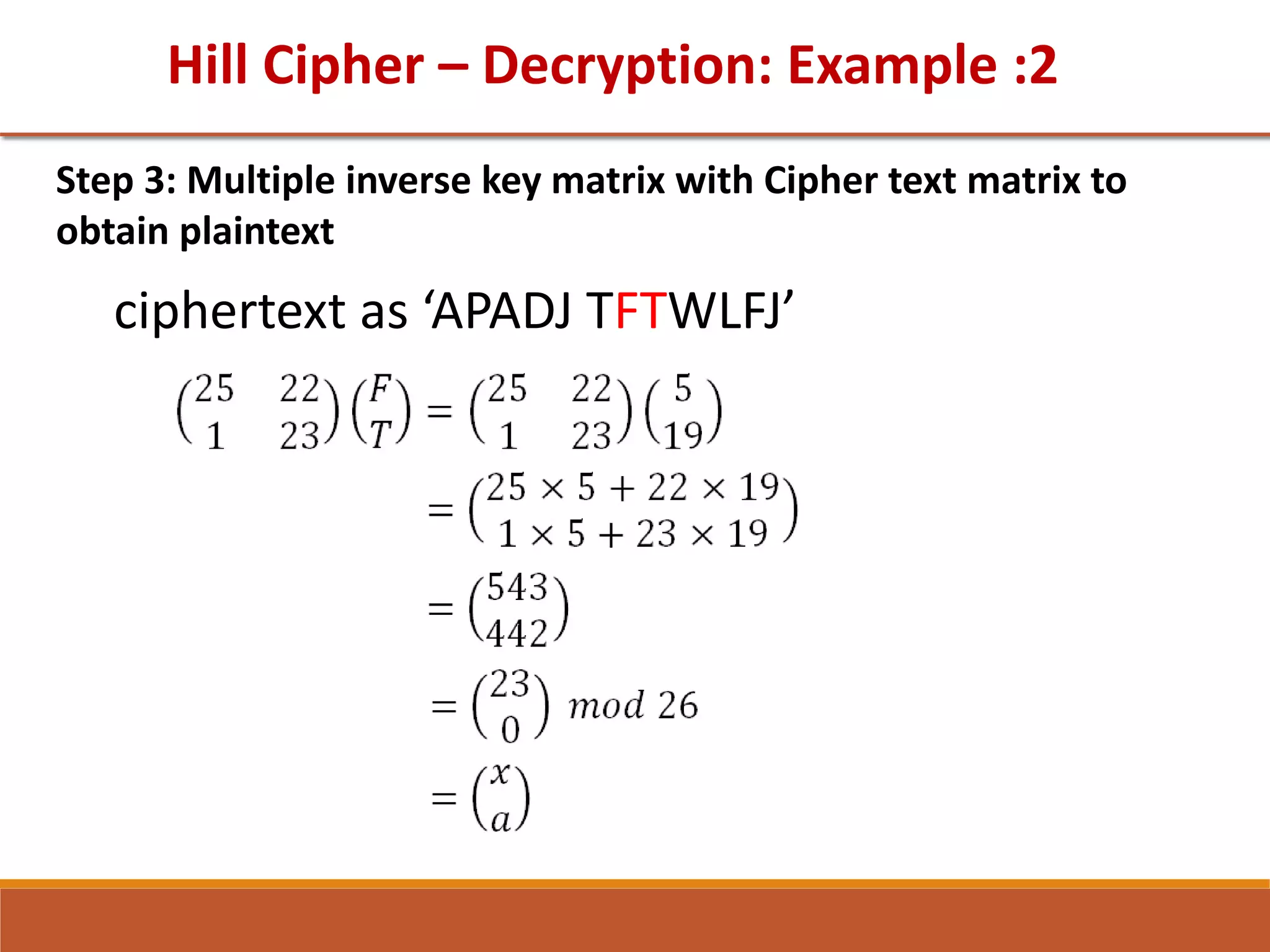

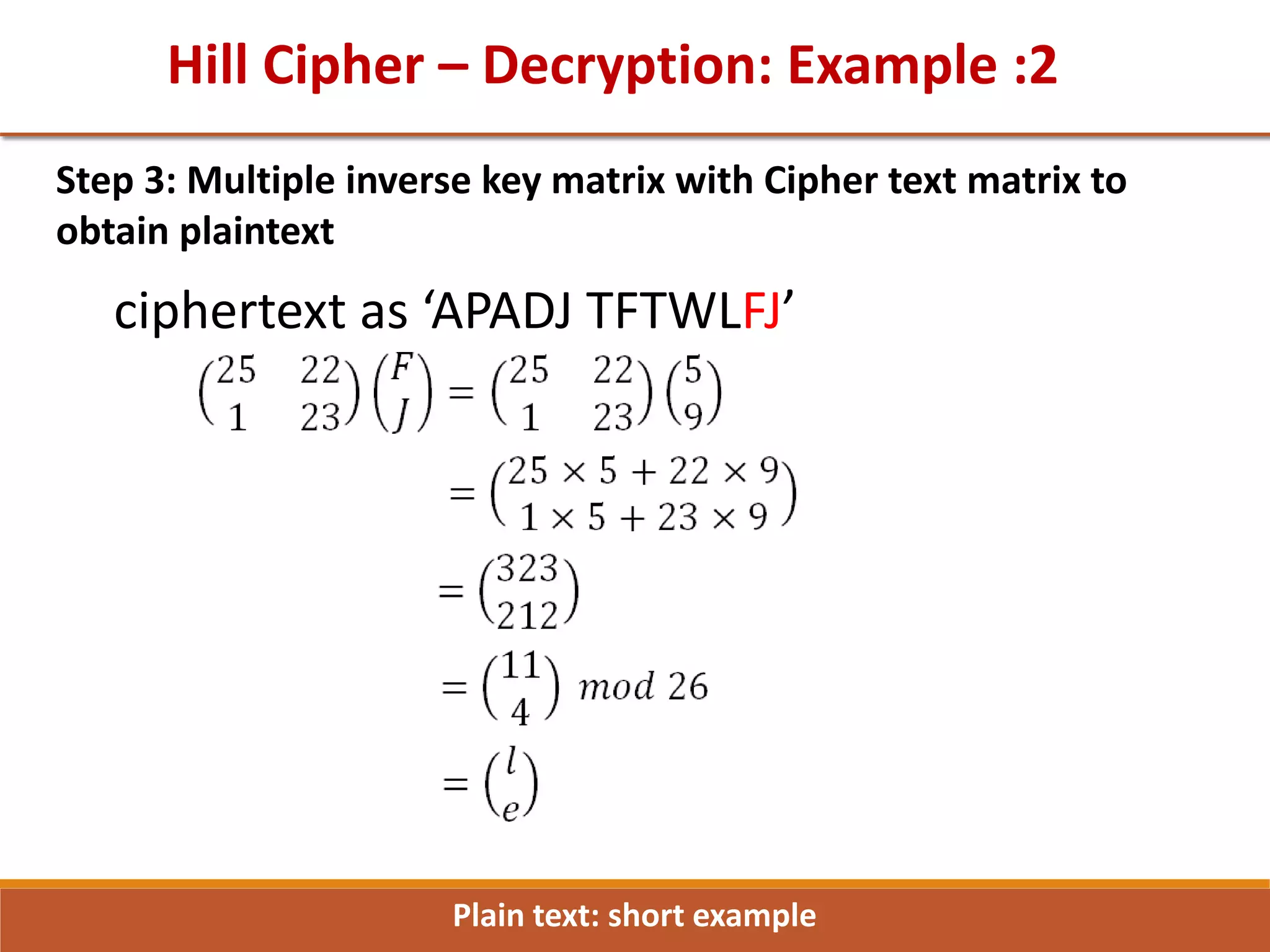
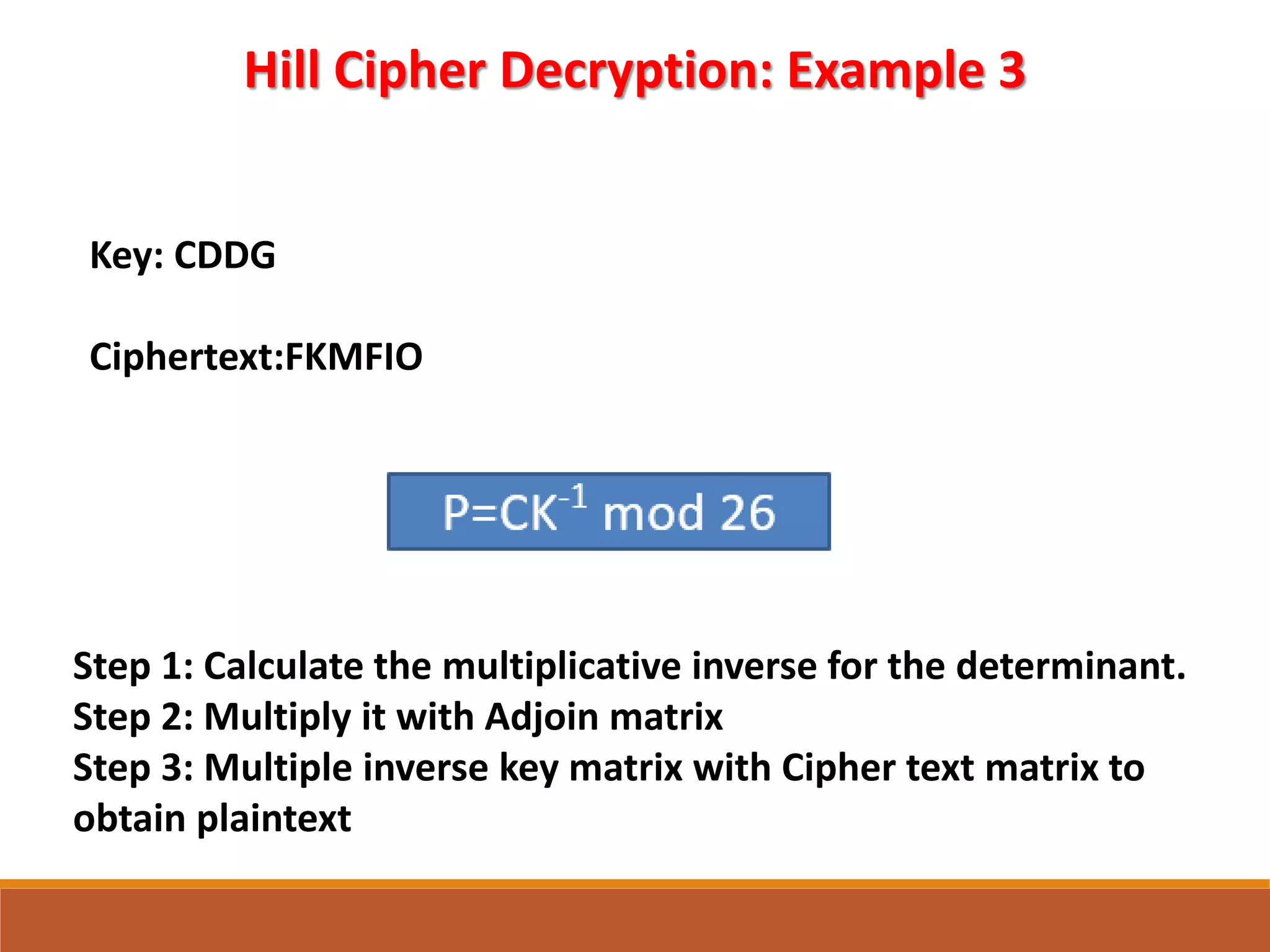




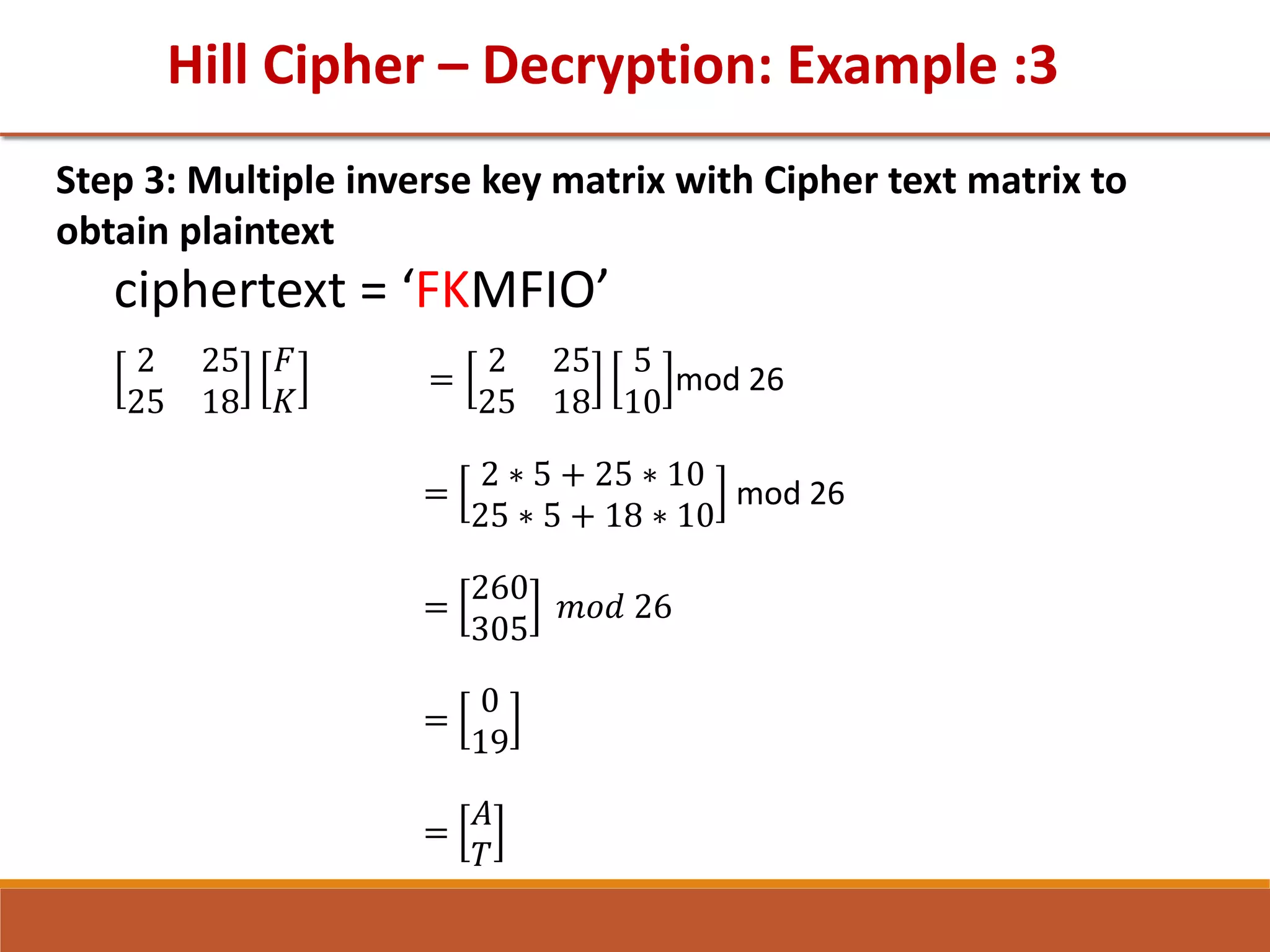

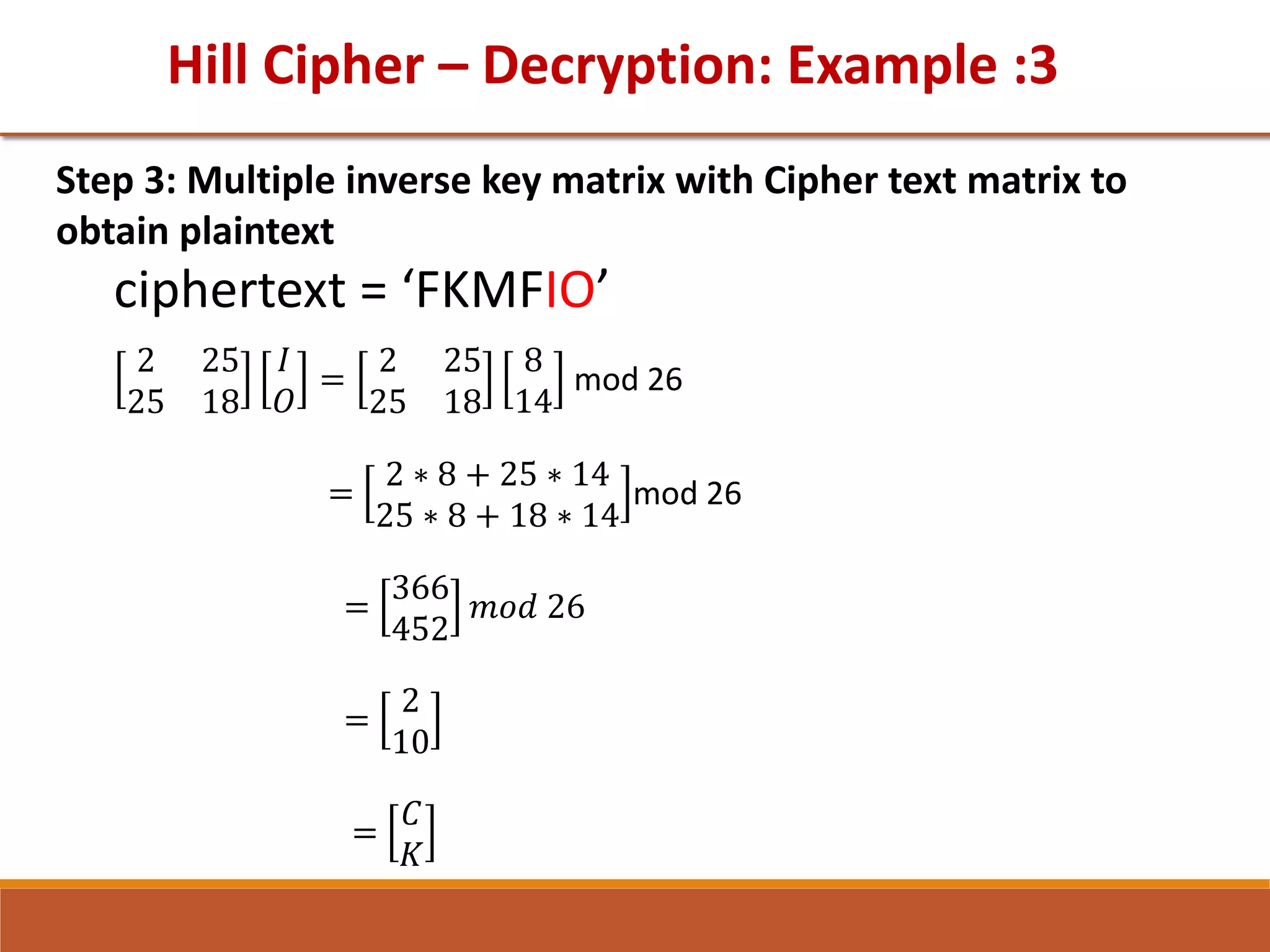


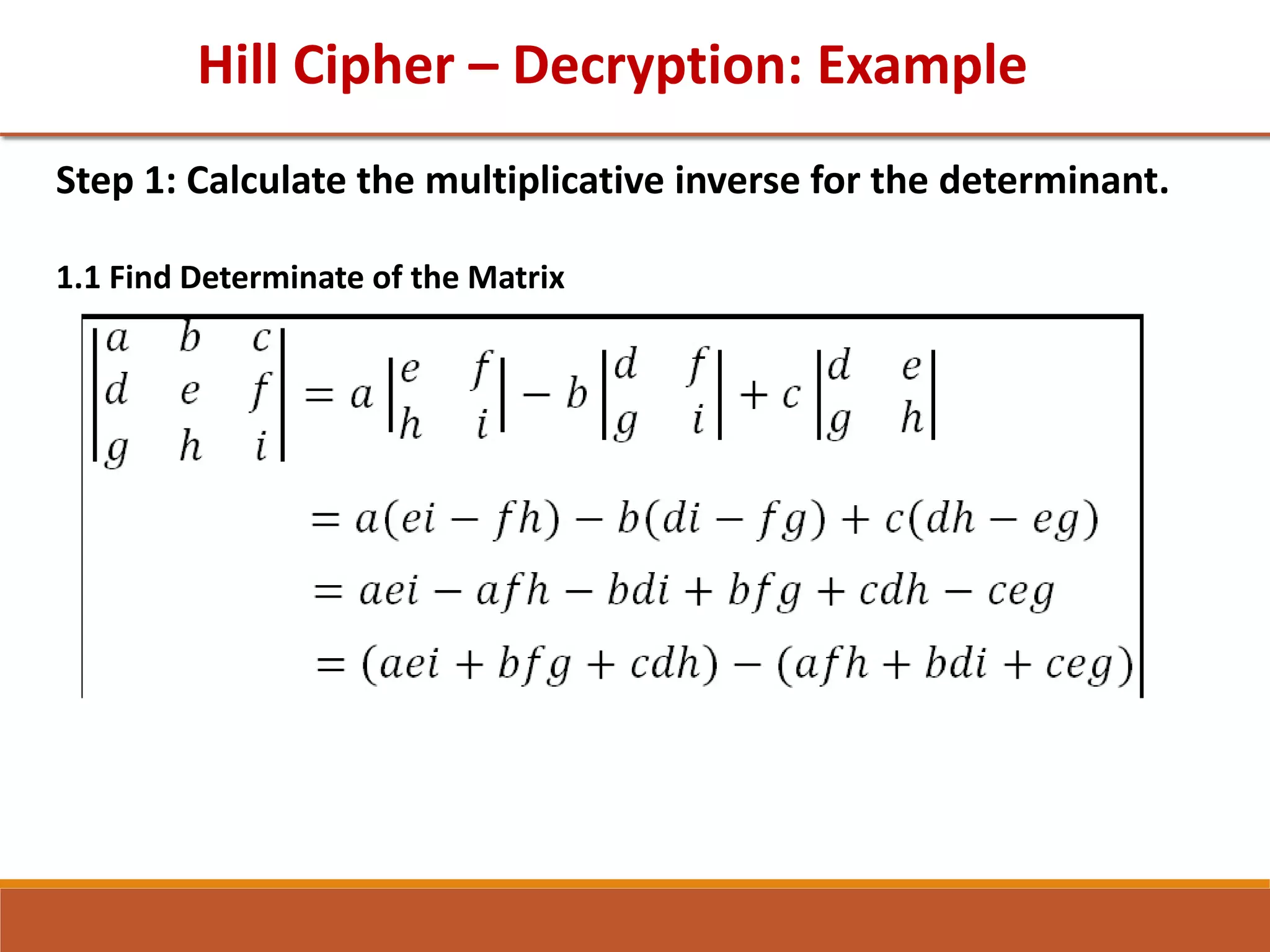



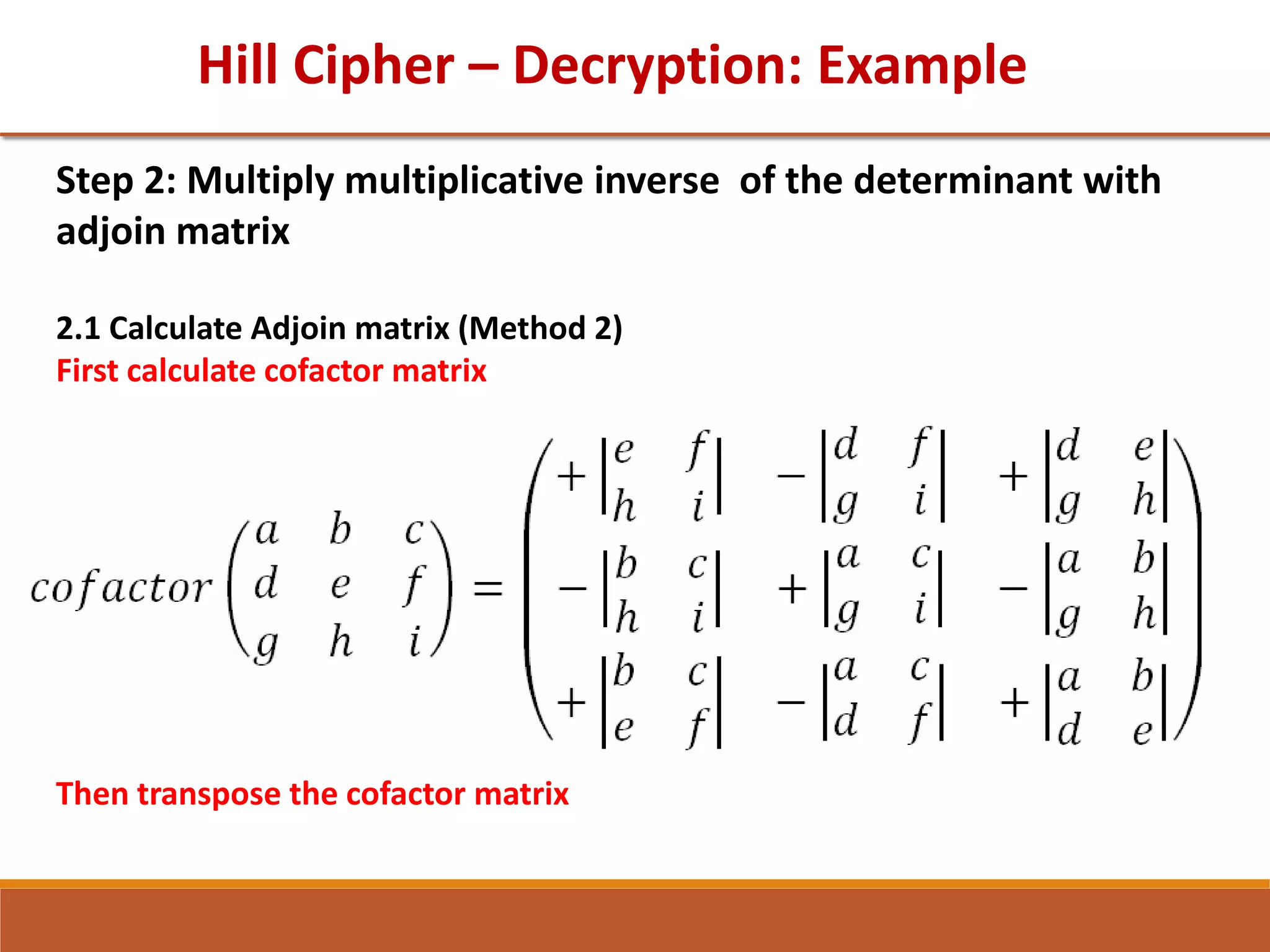


![GTU Question
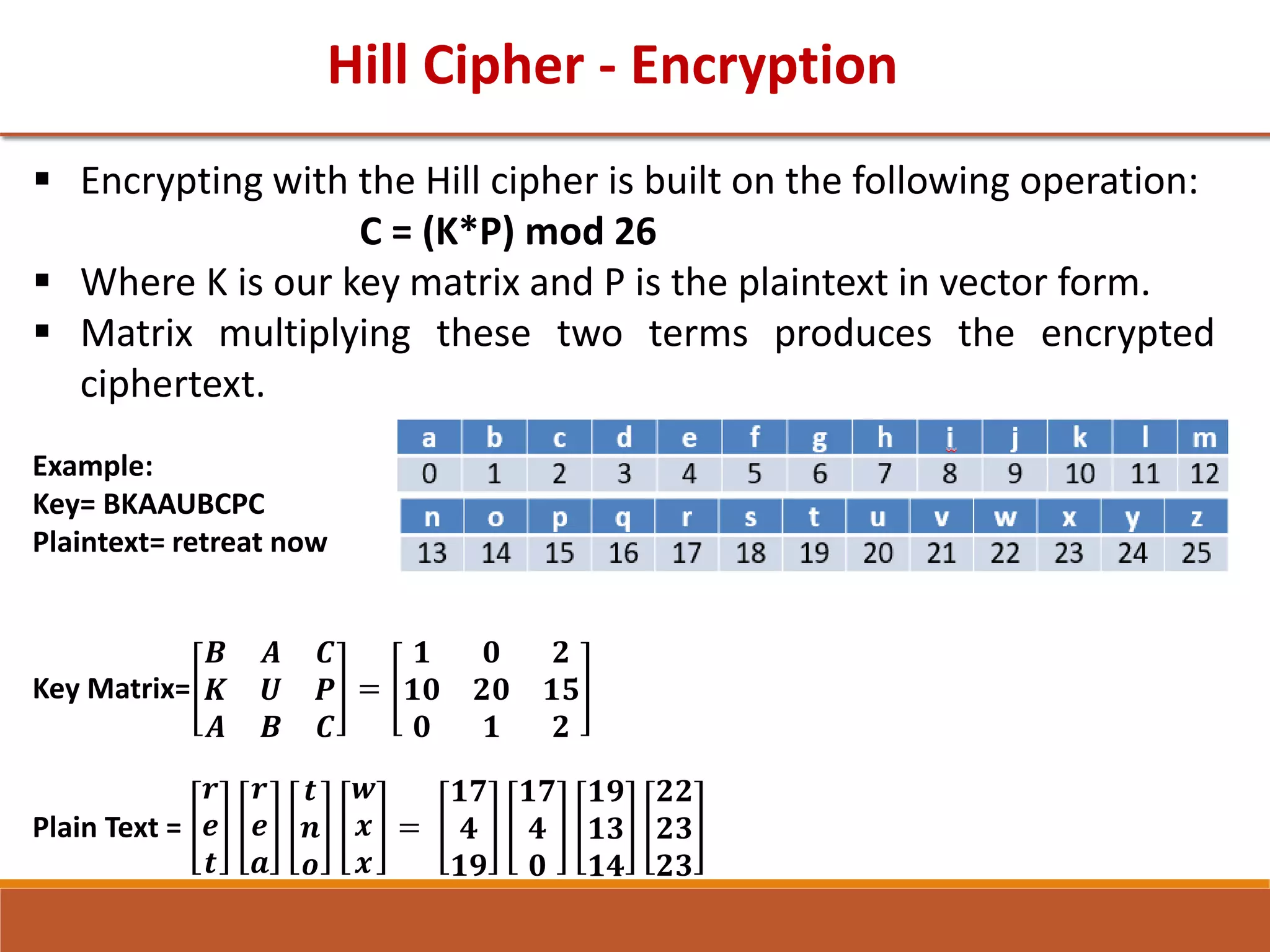
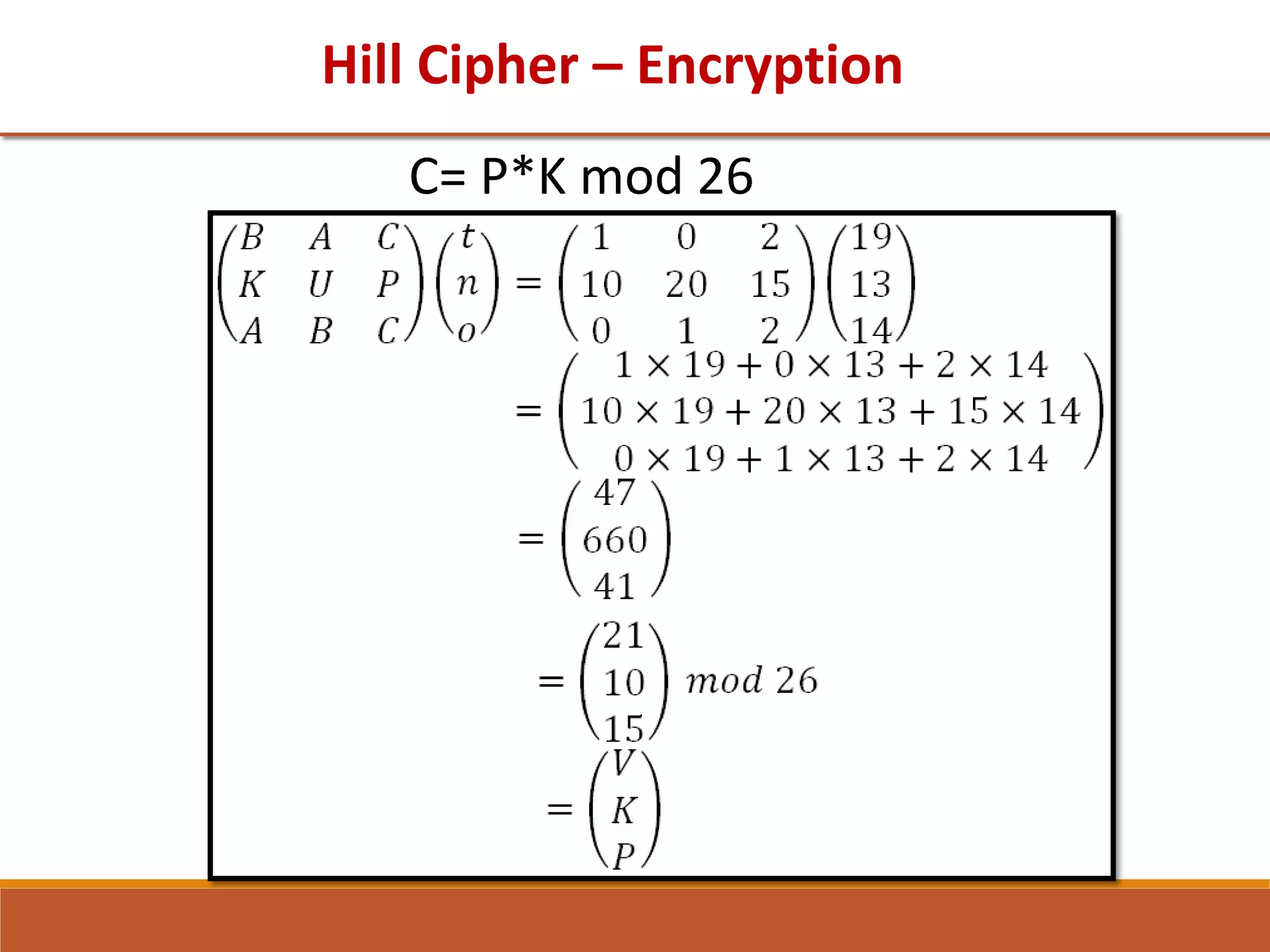
• Encrypt the message "meet me at the usual place " using the Hill
cipher with the key
9 4
5 7
[winter 2018] [7 Marks]
• Given key K=
17 17 5
21 18 21
2 2 19
and plaintext =”ney”. Find out the
ciphertext applying Hill Cipher. [ 7 Marks] [Summer 2019]
• Encrypt the message “GTU Examination” using the Hill cipher
algorithm with the key matrix
5 17
4 15
. Show your calculations
and the result. [Winter 2019] [7 marks]](https://image.slidesharecdn.com/unit1-211122112533/75/Unit-1-125-2048.jpg)