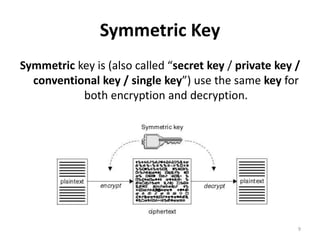
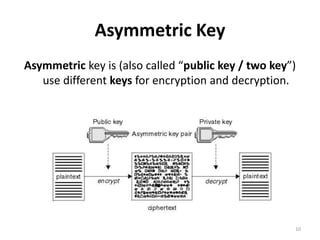
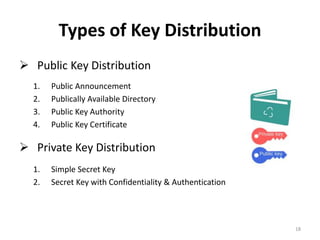
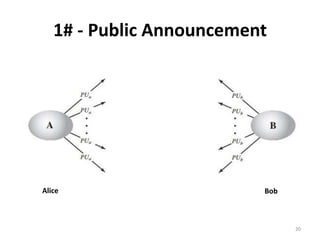
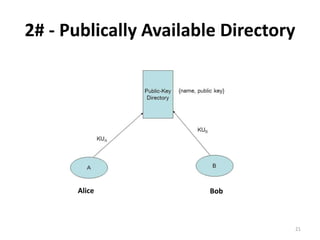
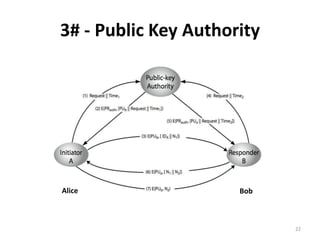
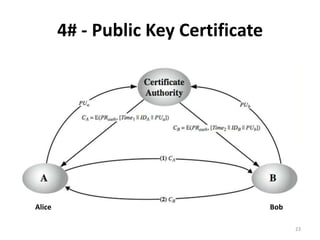
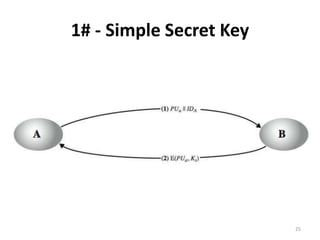
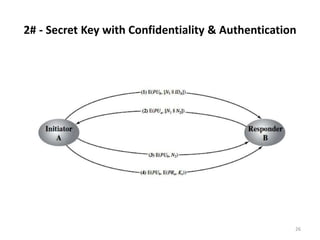
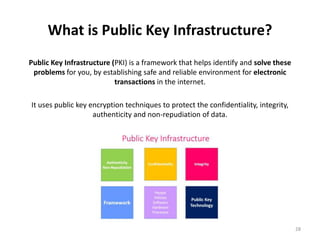
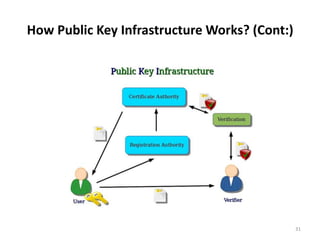
The document discusses key management and distribution in cryptography. It covers topics such as key generation, the different types of keys including symmetric and asymmetric keys, how symmetric and asymmetric encryption works, different methods of key distribution including public key distribution and private key distribution, and an overview of public key infrastructure. The goal of key management is to support the establishment and maintenance of secure key relationships between authorized parties.