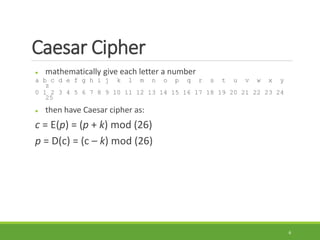
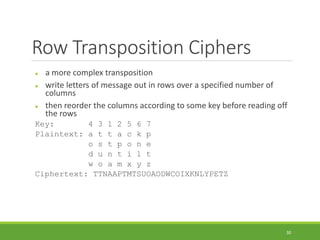
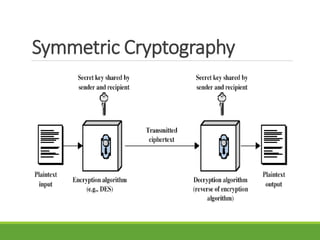
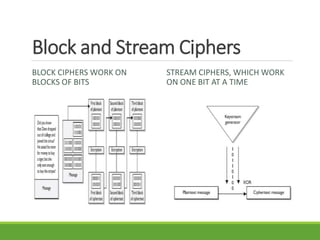
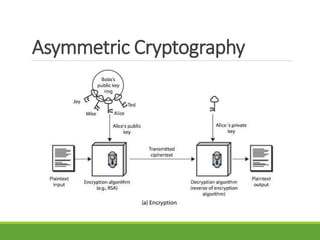
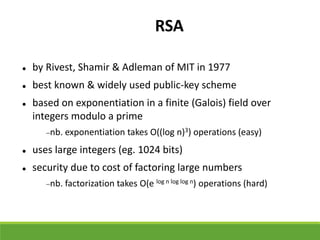
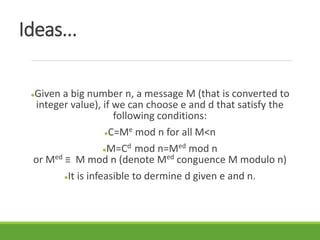
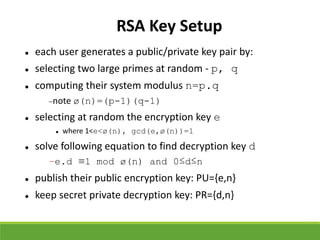
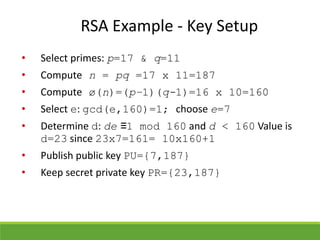
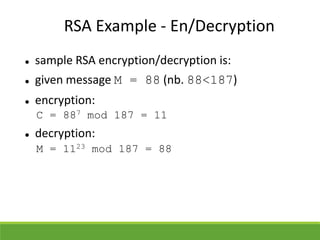
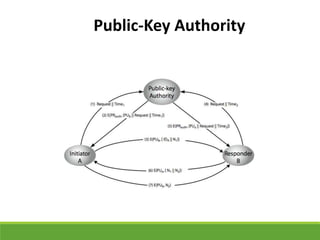
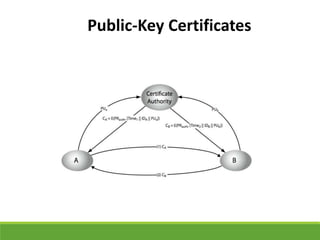
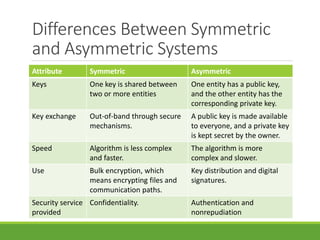
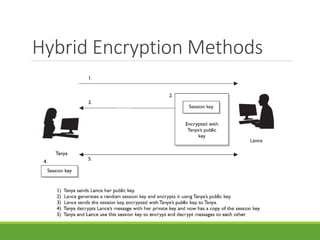
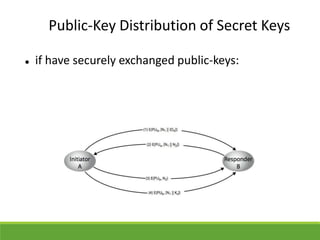
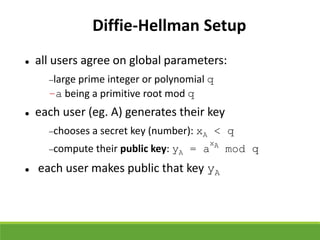
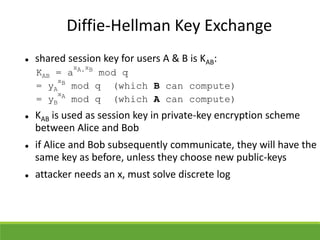
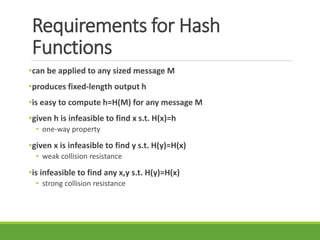
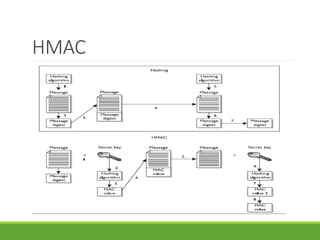
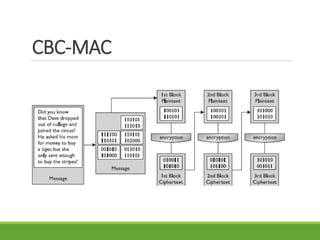
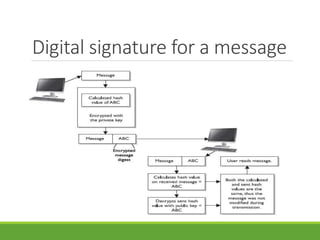
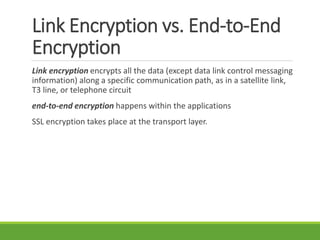
This document provides an overview of cryptography and its applications. It discusses the history of cryptography beginning in ancient Egypt. It defines basic cryptography terminology like plaintext, ciphertext, cipher, key, encryption, decryption, cryptography, and cryptanalysis. It describes classical ciphers like the Caesar cipher and substitution ciphers. It also discusses cryptanalysis techniques, transposition ciphers, modern symmetric ciphers, public key cryptography including RSA, key distribution methods, and hybrid encryption.