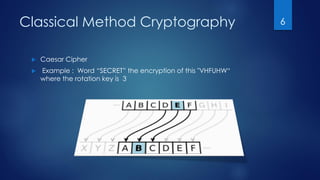
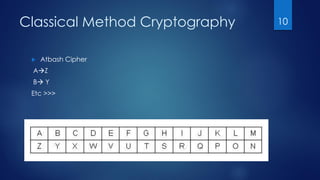
This document discusses old encryption algorithms from the classical method of cryptography, including replacement algorithms, the Caesar cipher, Vigenere cipher, Atbash cipher, and Affine cipher. It also describes the Jefferson cylinder, one of the strongest encryption devices of the time which was nearly unbreakable without stealing the entire device.