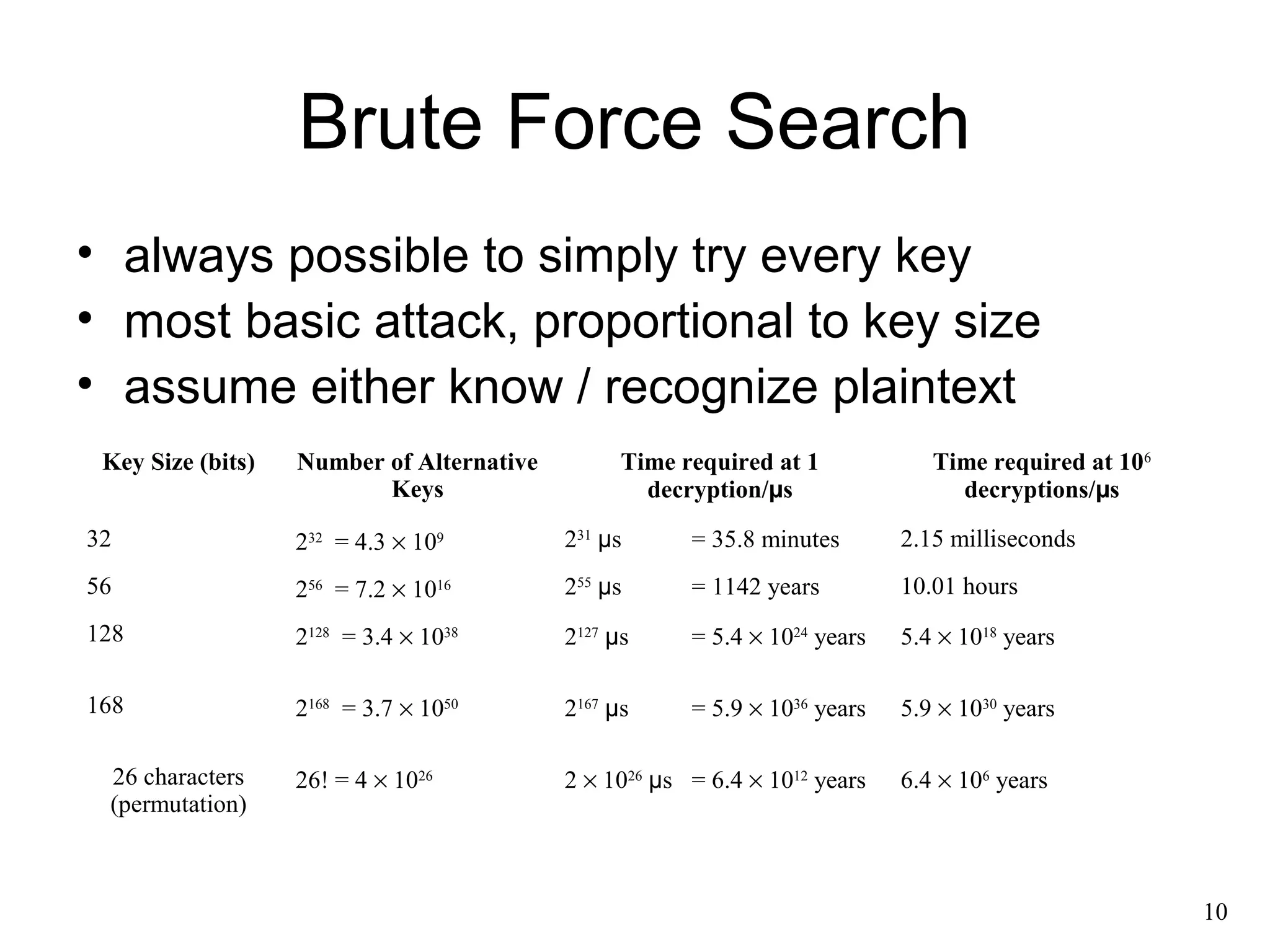
This document provides an overview of cryptographic techniques, including:
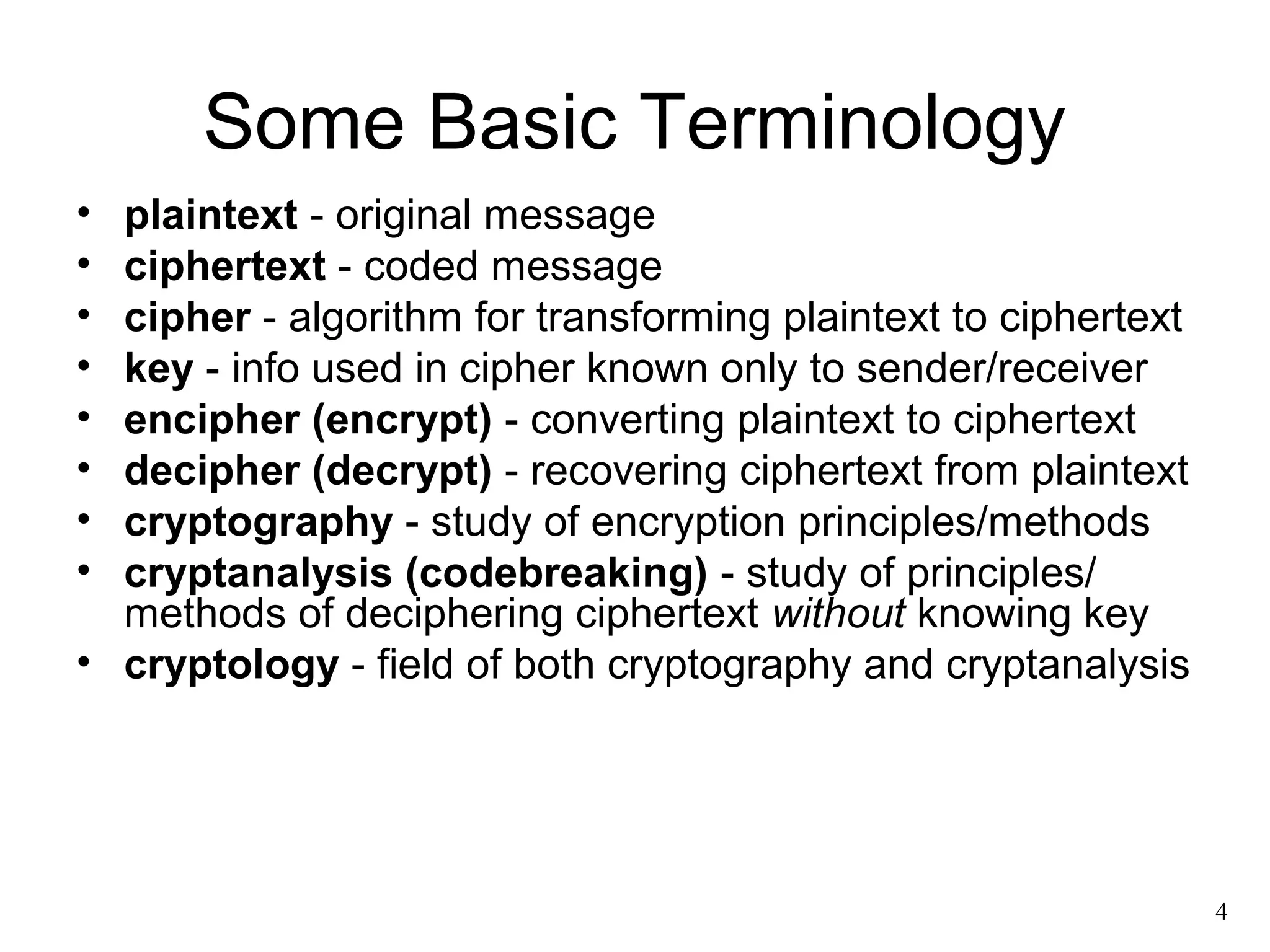
- Basic terminology related to cryptography like plaintext, ciphertext, encryption, decryption, etc.
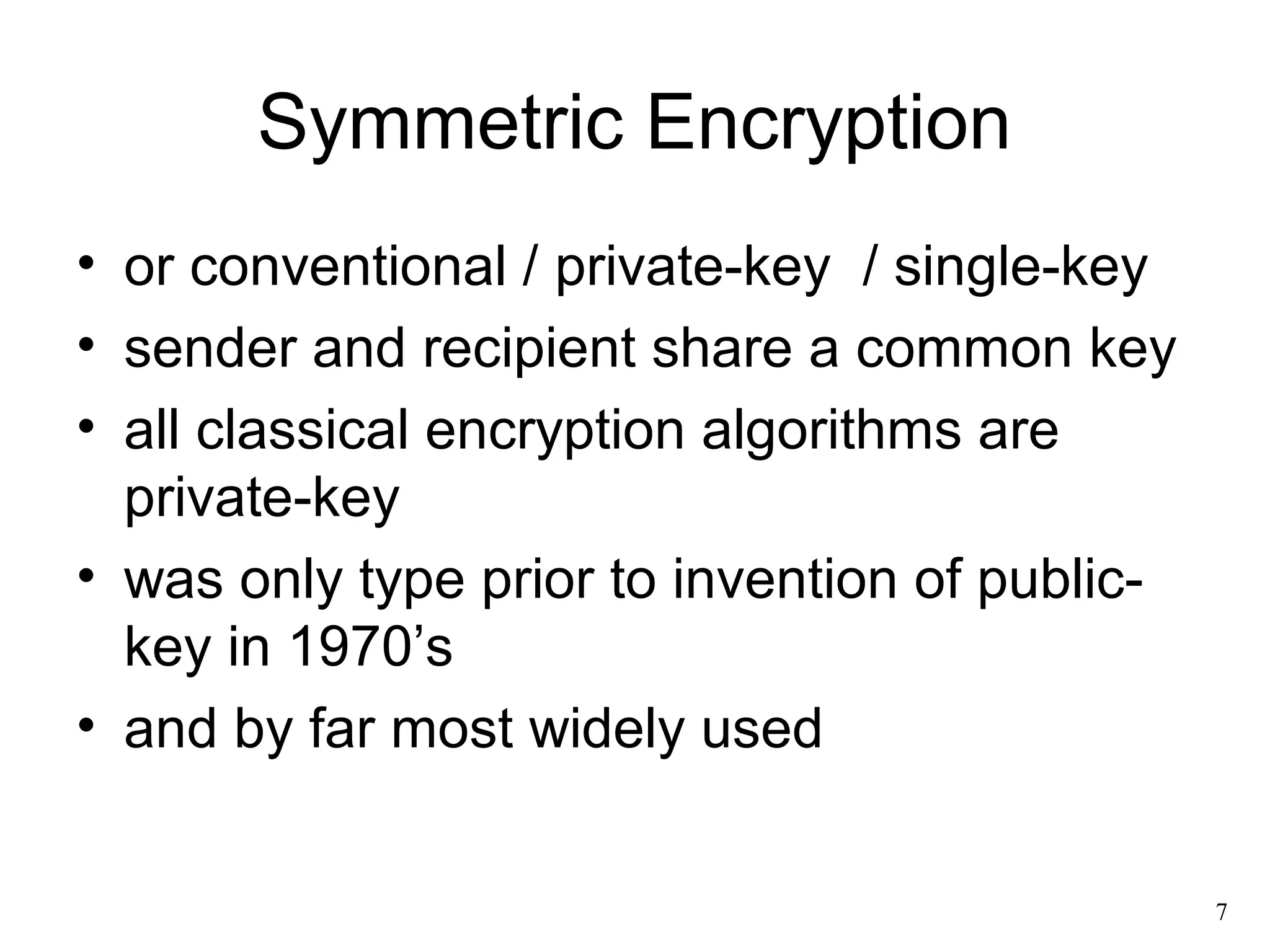
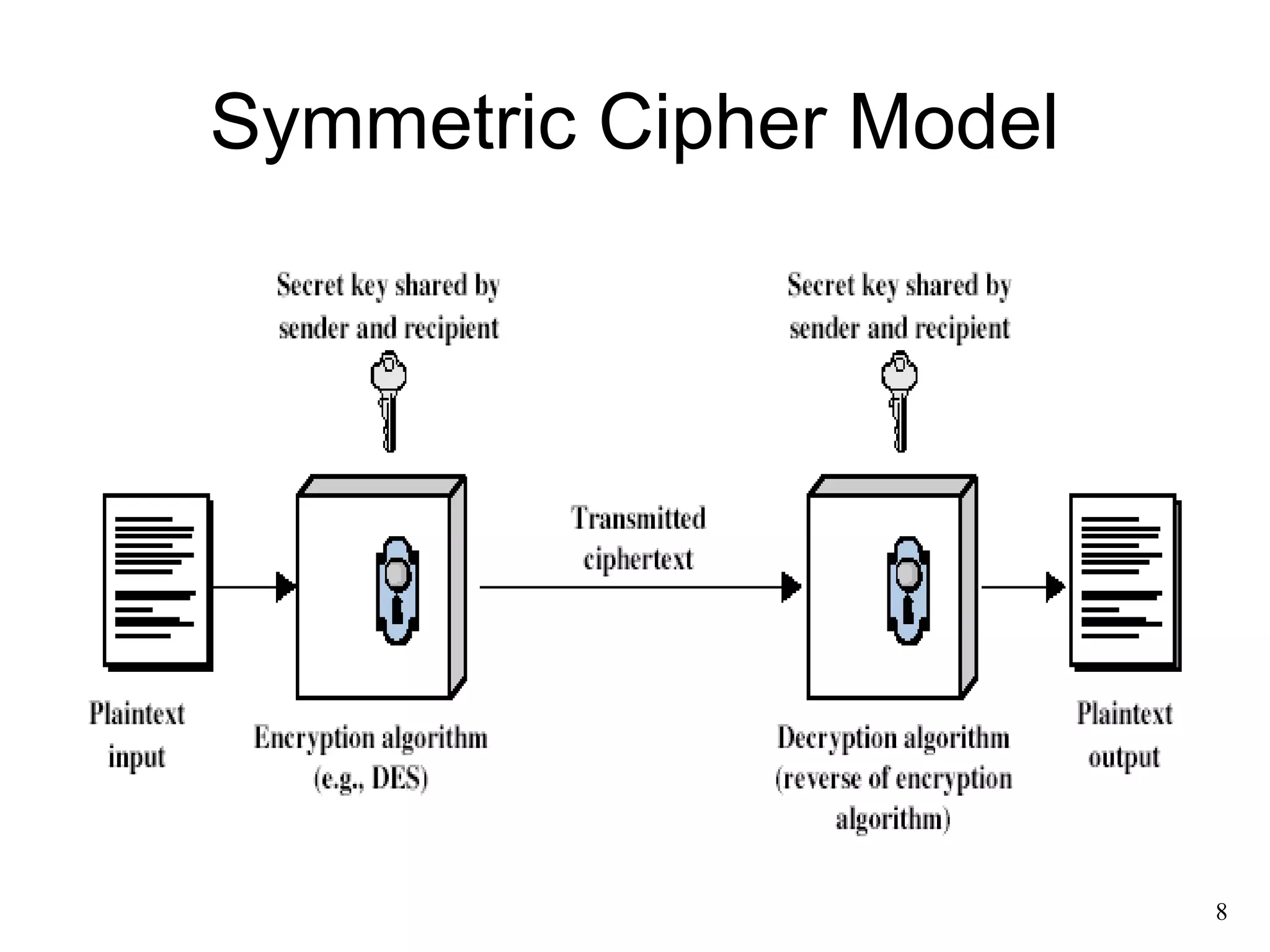
- Conventional encryption principles like the use of algorithms and secret keys.
- Characteristics of cryptographic techniques like symmetric vs asymmetric encryption.
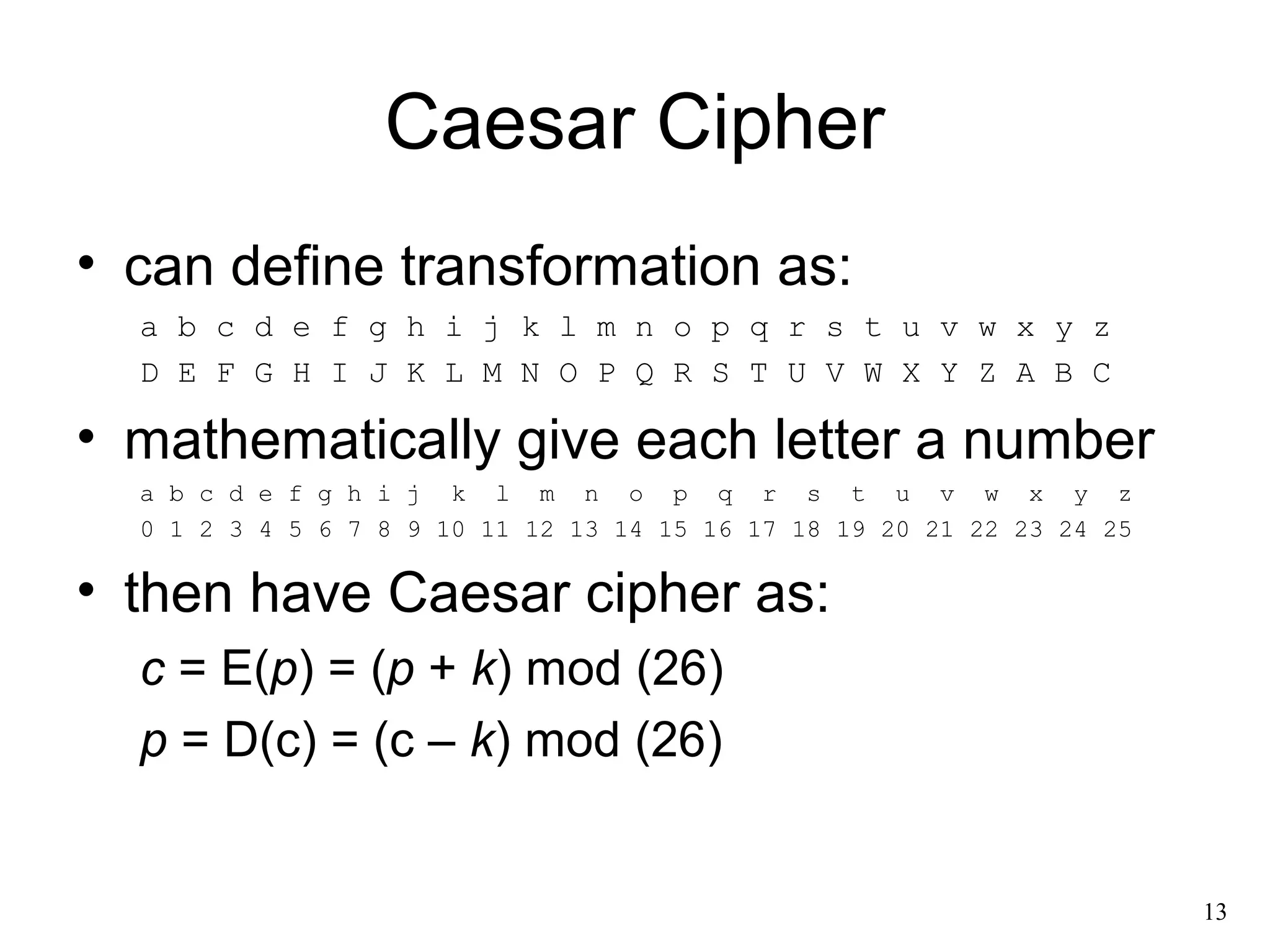
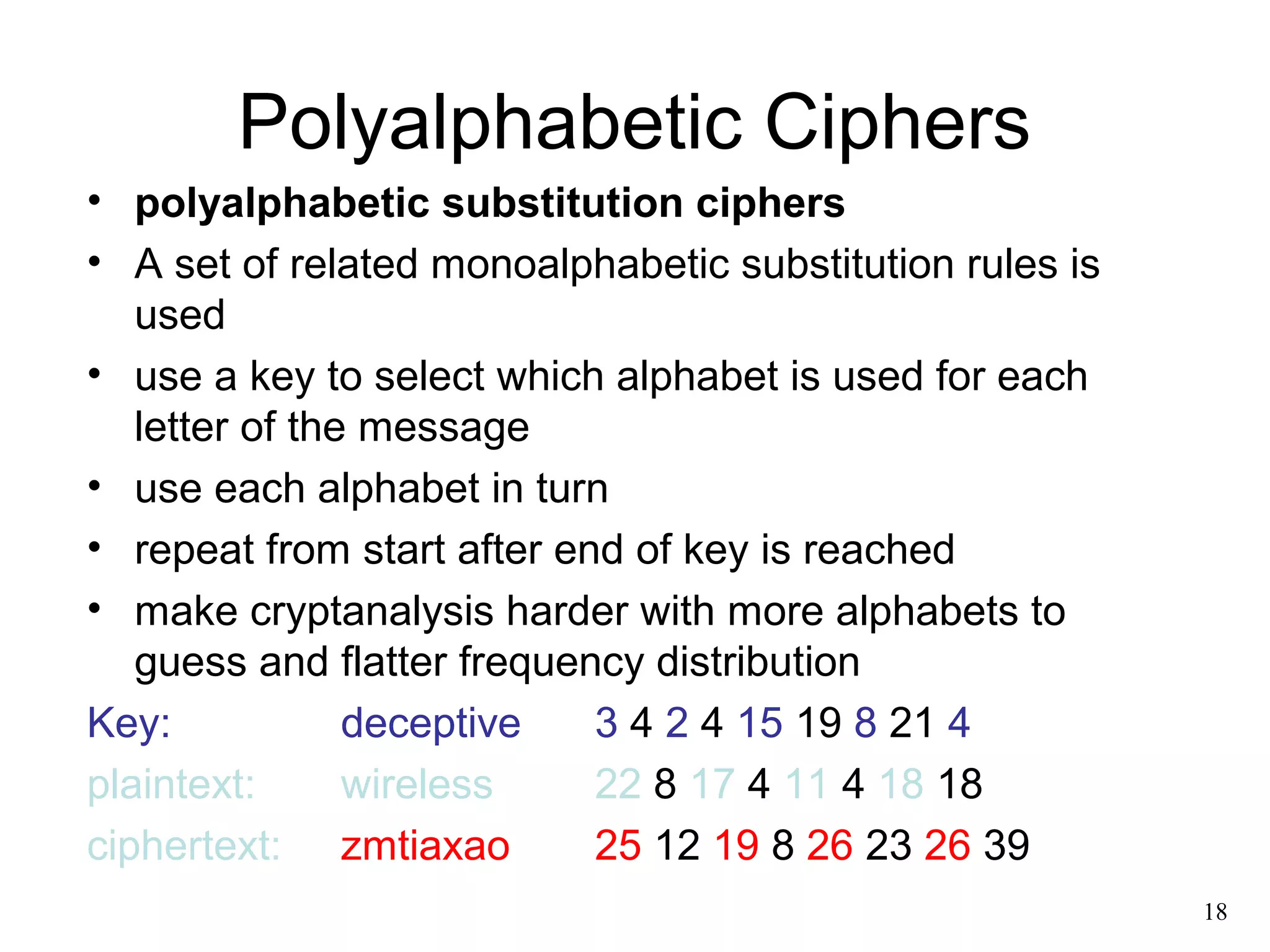
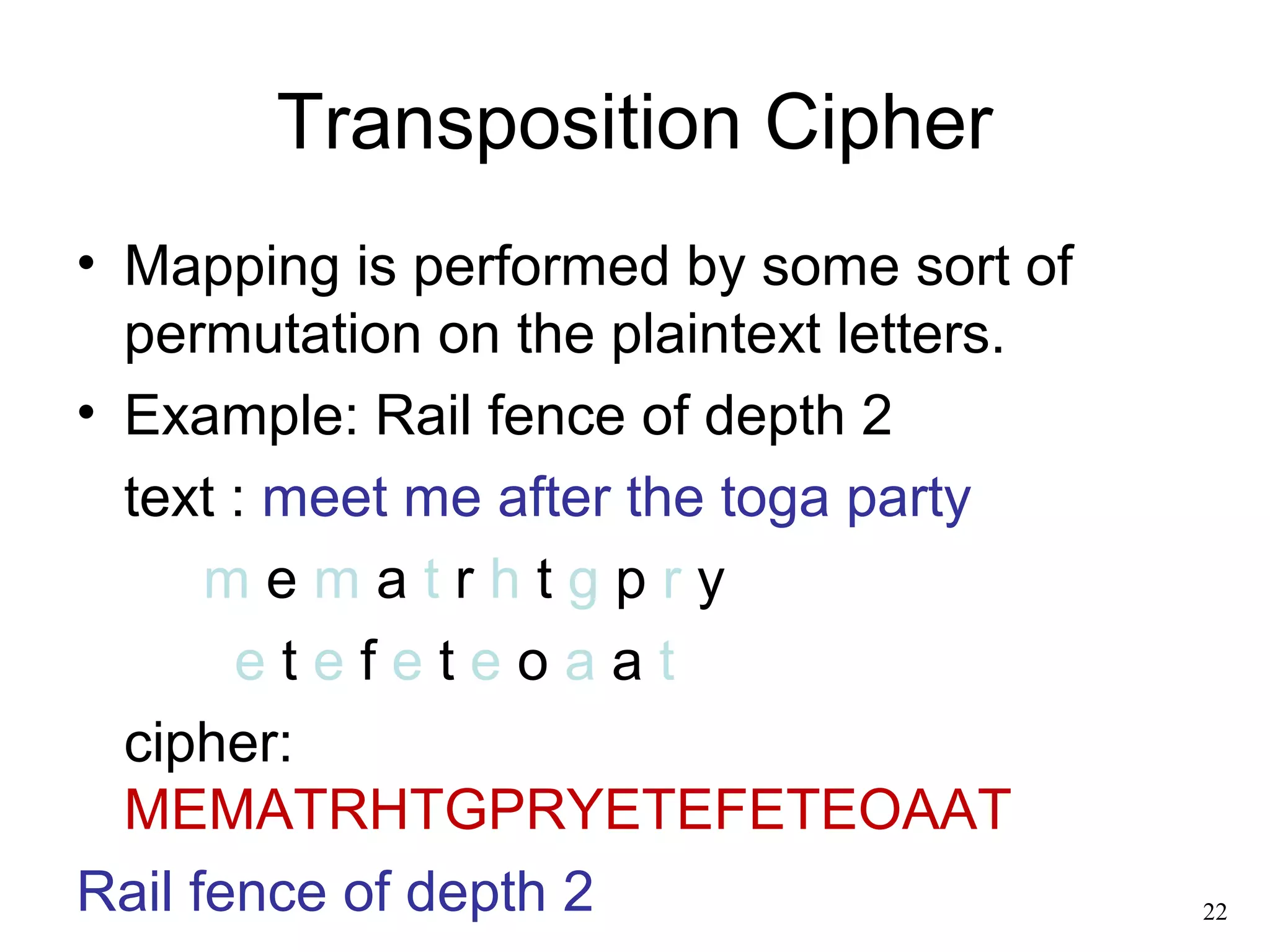
- Classical symmetric encryption algorithms like the Caesar cipher, monoalphabetic cipher, Playfair cipher, polyalphabetic ciphers like the Vigenère cipher, and transposition ciphers.
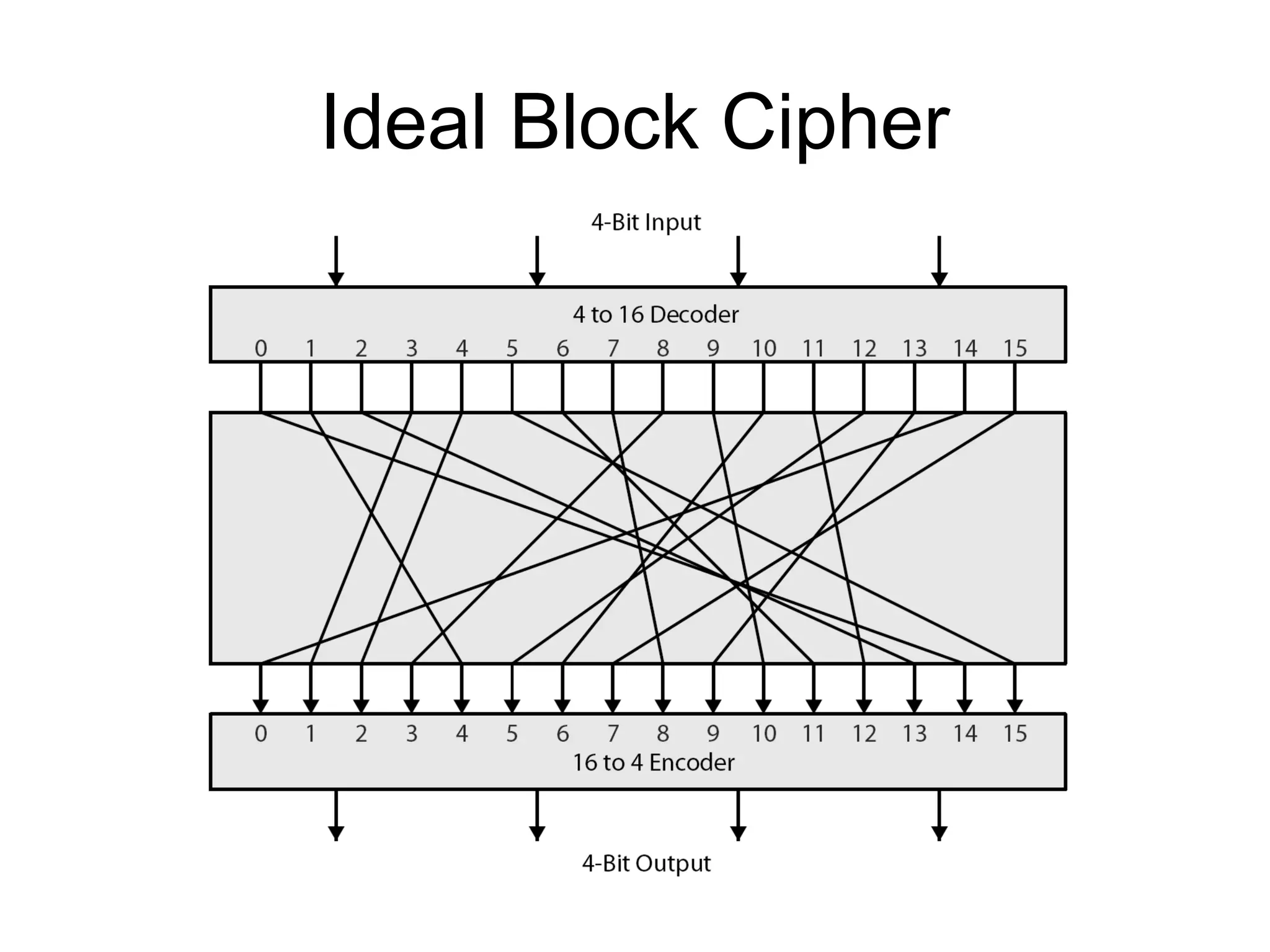
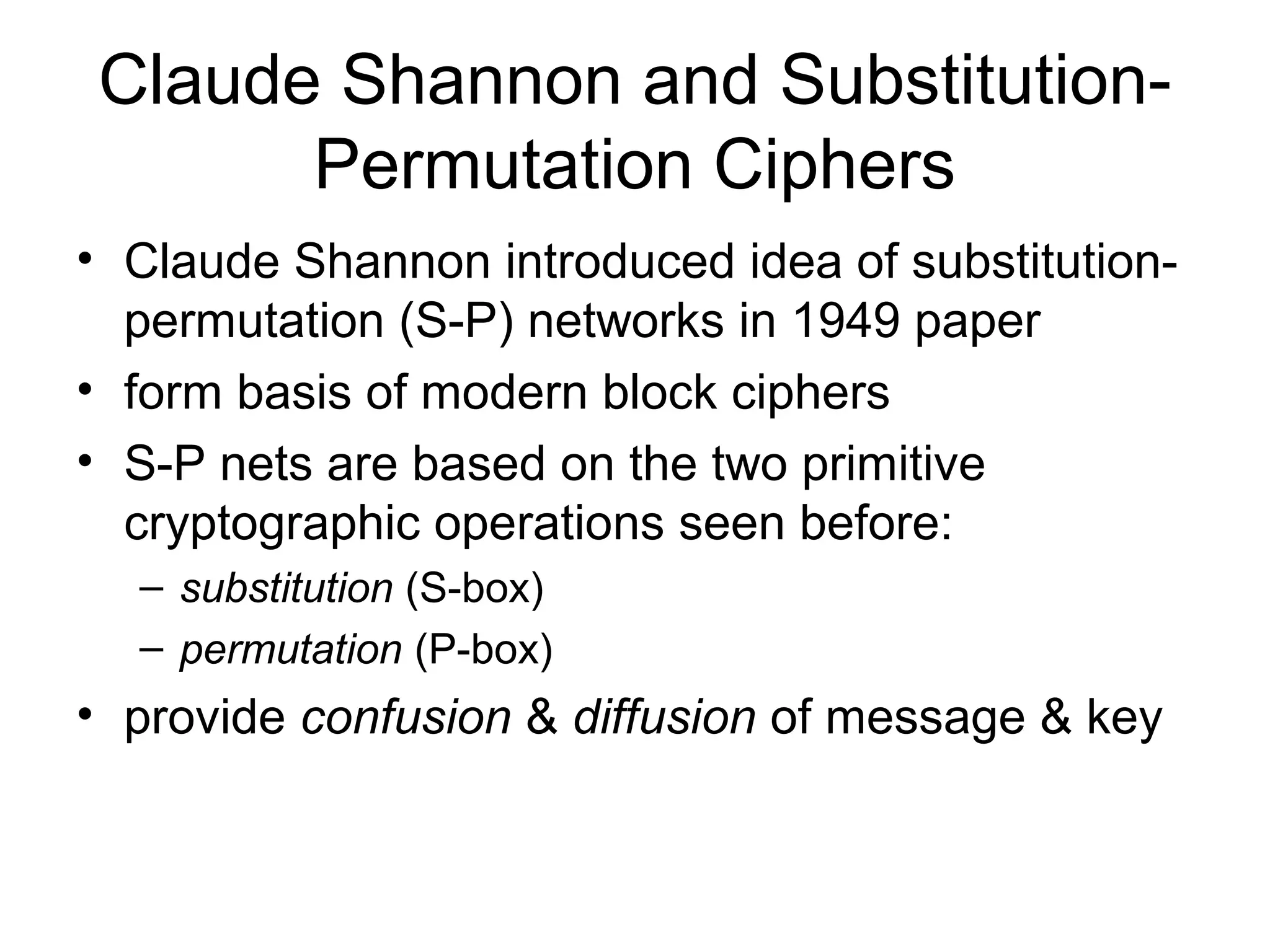
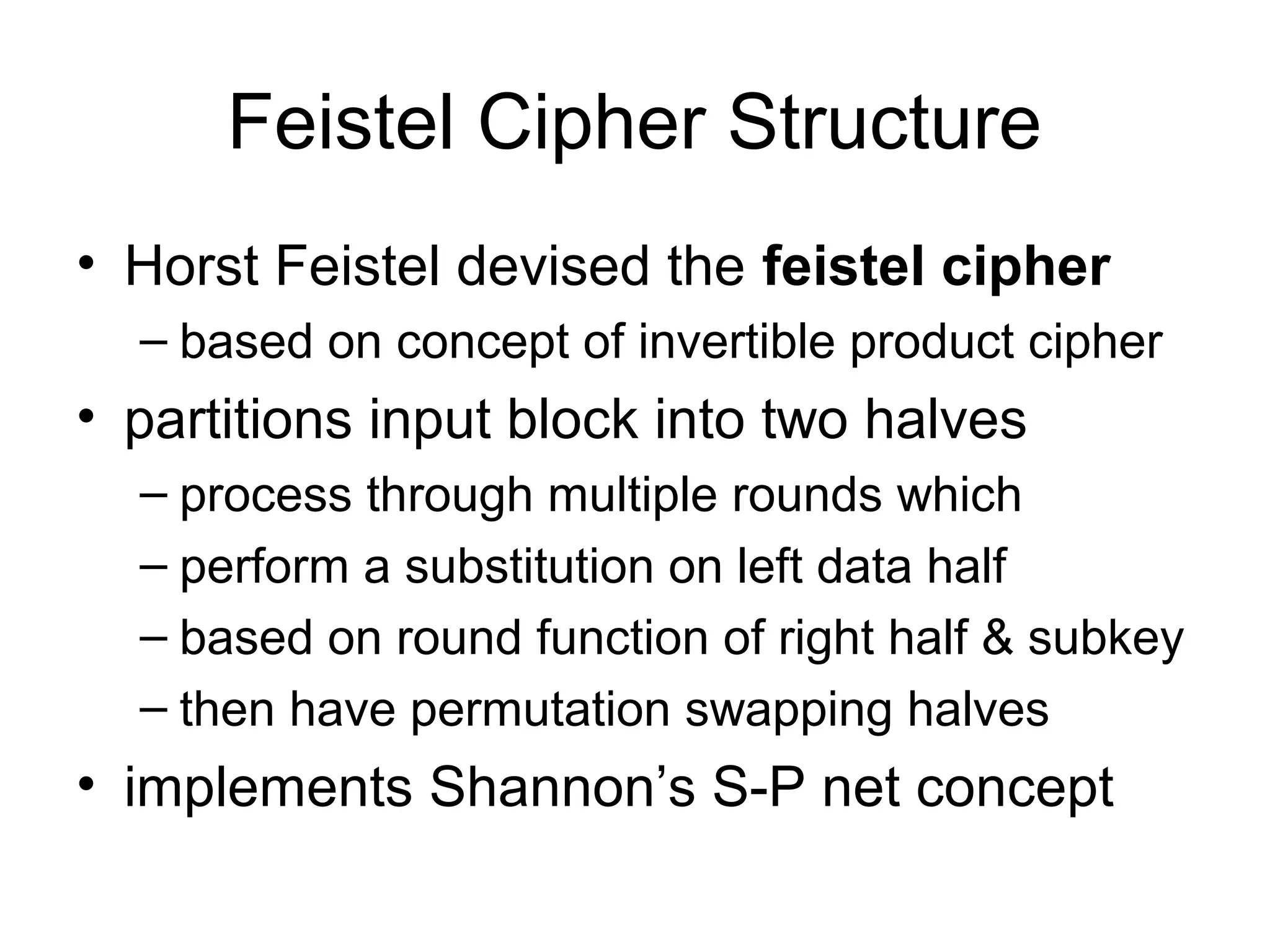
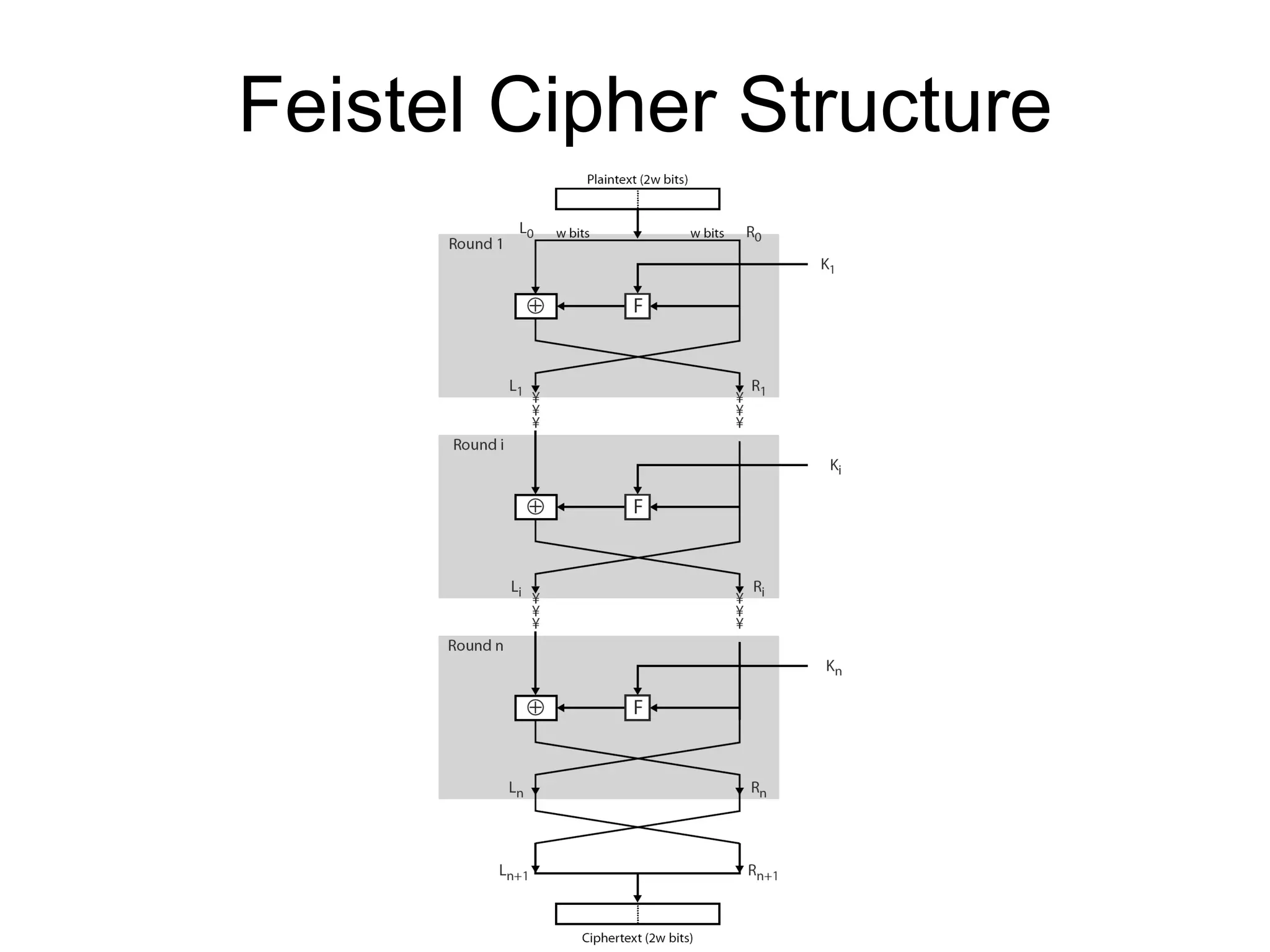
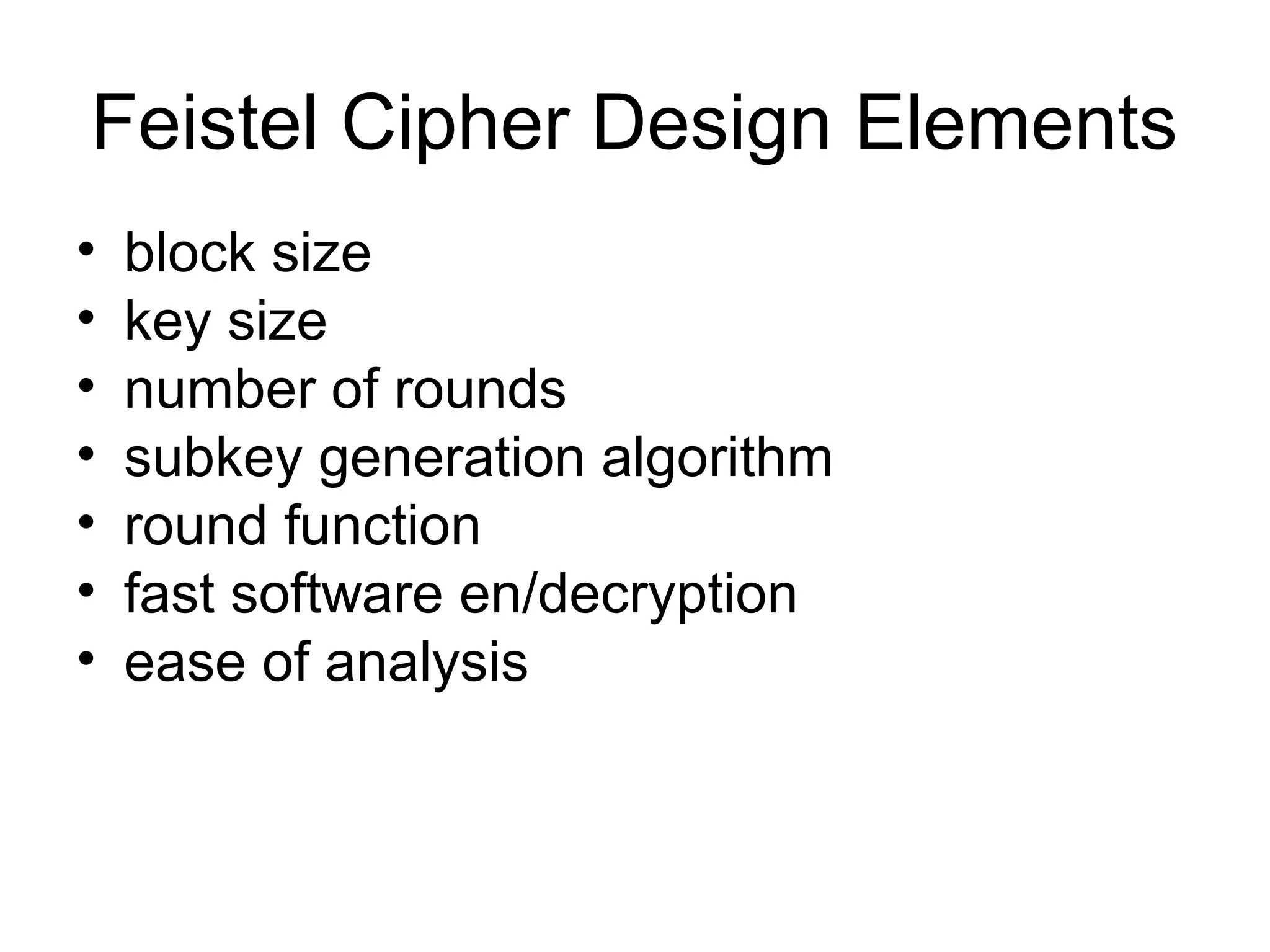
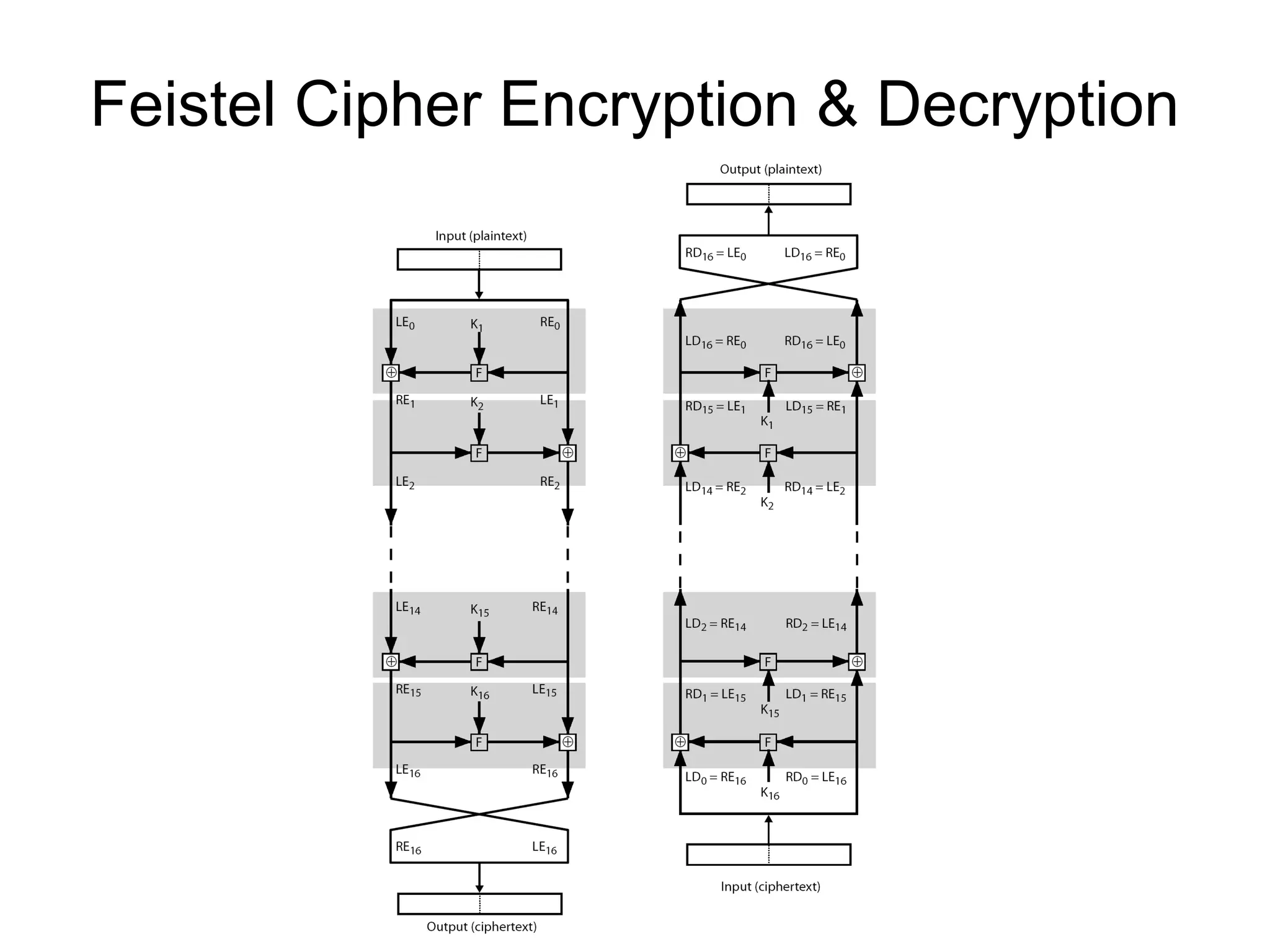
- Principles of modern block ciphers like DES, including the use of Feistel networks, confusion and diffusion properties, and encryption/decryption processes.





![9
Requirements
• two requirements for secure use of
symmetric encryption:
– a strong encryption algorithm
– a secret key known only to sender / receiver
• mathematically have:
Y = EK(X) [= E(K, X) ]
X = DK(Y) [= D(K, Y) ]
• assume encryption algorithm is known
• implies a secure channel to distribute key](https://image.slidesharecdn.com/03-overviewofcryptographictechniques-141101143838-conversion-gate02/75/overview-of-cryptographic-techniques-9-2048.jpg)