This document covers topics in network security including:
- It outlines the OSI security architecture and describes security services like authentication, access control, and data confidentiality.
- It discusses security mechanisms like encipherment and digital signatures. Common security attacks are also defined, including passive attacks, active attacks, masquerade, replay, and denial of service.
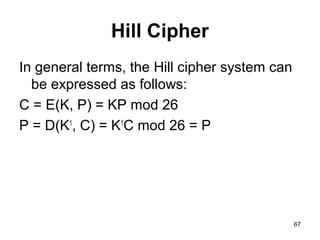
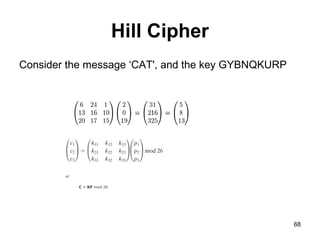
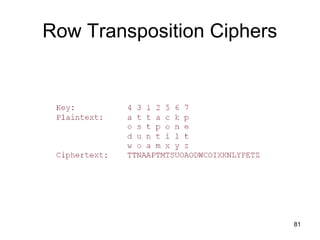
- Symmetric encryption techniques are introduced, including the Caesar cipher, monoalphabetic ciphers, Playfair cipher, and Hill cipher. Key concepts in classical cryptography are explained.


















































































































































































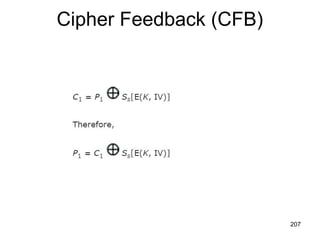
![A. Derive K1, the first-round sub key.
B. Derive L0, R0.
C. Expand R0 to get E[R0], where E[·] is the
expansion function.
D. Calculate A = E[R0] Ө K1.
E. Group the 48-bit result of (d) into sets of 6 bits
and evaluate the corresponding S-box
substitutions.
F. Concatenate the results of (e) to get a 32-bit
result, B.
G. Apply the permutation to get P(B).
H. Calculate R1 = P(B)Ө L0.
i. Write down the cipher text. 184](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-184-320.jpg)







































![Array Initialization
C Code:
char S[256];
Int i;
For(i=0; i< 256; i++)
S[i] = i;
After this the array would like this :
S[] = { 0,1,2,3, ……, 254, 255}](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-225-320.jpg)
![The KSA
• The initialized array S[256] is now run through
the KSA. The KSA uses the secret key to
scramble the array.
• C Code for KSA:
int i, j = 0;
for(i=0; i<256; i++)
{
j = ( j + S[i] + key[ i % key_len] ) % 256;
swap(S[i], S[j]);
}](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-226-320.jpg)
![The PRGA
• The KSA scrambled S[256] array is used to generate the
PRGA. This is the actual keystream.
• C Code:
i = j = 0;
while(output_bytes)
{
i = ( I + 1) % 256;
j = ( j + S[i] ) % 256;
swap( S[i], S[j] );
output = S[ ( S[i] + S[j] ) % 256 ]
}](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-227-320.jpg)



![KSA
First Iteration (i = 0, j = 0, S = {0, 1, 2, 3}):
j = (j + S[ i ] + K[ i ]) = (0 + 0 + 1) = 1
Swap S[ i ] with S[ j ]: S = {1, 0, 2, 3}
Second Iteration (i = 1, j = 1, S = {1, 0, 2, 3}):
j = (j + S[ i ] + K[ i ]) = (1 + 0 + 7) = 0 (mod 4)
Swap S[ i ] with S[ j ]: S = {0, 1, 2, 3}](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-231-320.jpg)
![KSA
Third Iteration (i = 2, j = 0, S = {0, 1, 2, 3}):
j = (j + S[ i ] + K[ i ]) = (0 + 2 + 1) = 3
Swap S[ i ] with S[ j ]: S = {0, 1, 3, 2}
Fourth Iteration (i = 3, j = 3, S = {0, 1, 3, 2}):
j = (j + S[ i ] + K[ i ]) = (3 + 2 + 7) = 0 (mod 4)
Swap S[ i ] with S[ j ]: S = {2, 1, 3, 0}](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-232-320.jpg)
![PRGA
Reset i = j = 0, Recall S = {2, 1, 3, 0}
i = i + 1 = 1
j = j + S[ i ] = 0 + 1 = 1
Swap S[ i ] and S[ j ]: S = {2, 1, 3, 0}
Output z = S[ S[ i ] + S[ j ] ] = S[2] = 3](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-233-320.jpg)






















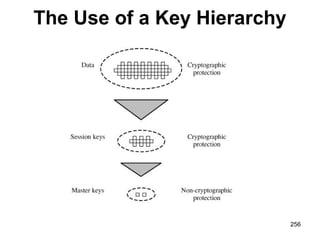


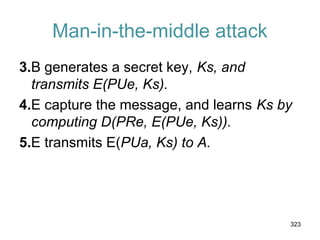
![Key Distribution Scenario
• A stores the session key for use in the upcoming
session and forwards to B the information that
originated at the KDC for B, namely, E(Kb, [Ks ||
IDA]). Because this information is encrypted with
Kb, it is protected from eavesdropping.
• B now knows the session key (Ks), knows that
the other party is A (from IDA), and knows that
the information originated at the KDC (because it
is encrypted using Kb).
259](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-259-320.jpg)
















![Public-Key Cryptosystem:
Secrecy
• With the message X and the encryption
key PUb as input, A forms the cipher text
Y = [Y1, Y2,..., YN]:
• Y = E(PUb, X)
• The intended receiver, in possession of
the matching private key, is able to invert
the transformation:
• X = D(PRb, Y)
276](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-276-320.jpg)



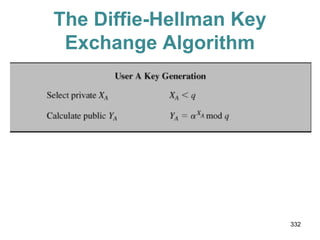
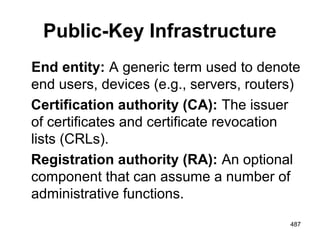
![Requirements for Public-Key
Cryptography
1.It is computationally easy for a party B to
generate a pair (public key PUb, private key
PRb).
2. It is computationally easy for a sender A,
knowing the public key and the message to be
encrypted, M, to generate the corresponding
cipher text: C = E(PUb, M)
3.It is computationally easy for the receiver B to
decrypt the resulting cipher text using the private
key to recover the original message: M = D(PRb,
C) = D[PRb, E(PUb, M)] 280](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-280-320.jpg)













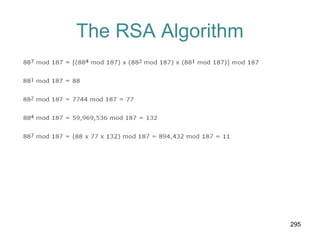















































































![Hash Functions & MAC Security
• cryptanalytic attacks exploit structure
– like block ciphers want brute-force attacks to be the
best alternative
• have a number of analytic attacks on iterated
hash functions
– CVi = f[CVi-1, Mi]; H(M)=CVN
– typically focus on collisions in function f
– like block ciphers is often composed of rounds
– attacks exploit properties of round functions](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-380-320.jpg)































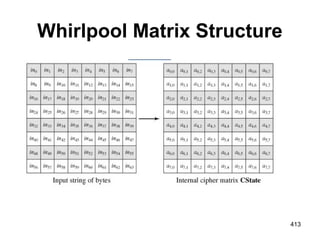

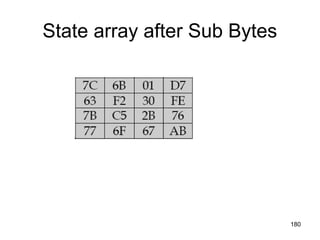
![The Nonlinear Layer SB
The leftmost 4 bits of the byte are used as
a row value and the rightmost 4 bits are
used as a column value.
These row and column values serve as
indexes into the S-box to select a unique
8-bit output value.
For example, the hexadecimal value[3]
{95}references row 9, column 5 of the S-
box, which contains the value {BA}.
Accordingly, the value {95}is mapped into
the value {BA}. 415](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-415-320.jpg)






























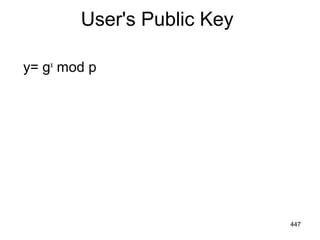
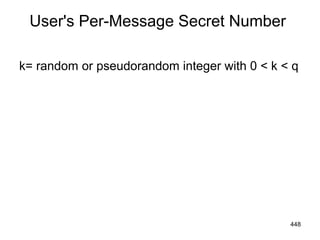
![Signing
r= (gk
mod p) mod q
s= [k-1
(H(M) + xr)] mod q
Signature = (r, s)
449](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-449-320.jpg)
![Verifying
w= (s')-1
mod q
u1= [H(M')w] mod q
u2=(r')w mod q
v= [(gu1
yu2
) mod p] mod q
450](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-450-320.jpg)
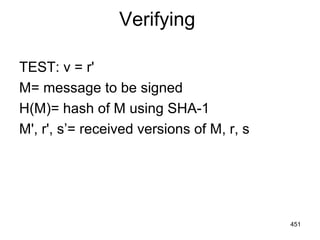





![457
A Simple Authentication Dialogue
1- IDc + Pc+IDv
2- Ticket
3- IDc +Ticket
Ticket=Ekv[IDc,ADc,IDv]
kv=Secret Key between AS and
V (Server)
Pc=password of client](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-457-320.jpg)
























![31/03/2005 Authentication Applications 483
One-Way Authentication:
• 1 message ( A->B) used to establish
– the identity of A and that message is from A
– message was intended for B
– integrity & originality of message
A B1-A {ta,ra,B,sgnData,KUb[Kab]}
Ta-timestamp rA=nonce B =identity
sgnData=signed with A’s private key](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-483-320.jpg)
![31/03/2005 Authentication Applications 484
Two-Way Authentication
• 2 messages (A->B, B->A) which also
establishes in addition:
– the identity of B and that reply is from B
– that reply is intended for A
– integrity & originality of reply
A B
1-A {ta,ra,B,sgnData,KUb[Kab]}
2-B {tb,rb,A,sgnData,KUa[Kab]}](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-484-320.jpg)
![31/03/2005 Authentication Applications 485
Three-Way Authentication
• 3 messages (A->B, B->A, A->B) which
enables above authentication without
synchronized clocks
A B
1- A {ta,ra,B,sgnData,KUb[Kab]}
2 -B {tb,rb,A,sgnData,KUa[Kab]}
3- A{rb}](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-485-320.jpg)










































































































































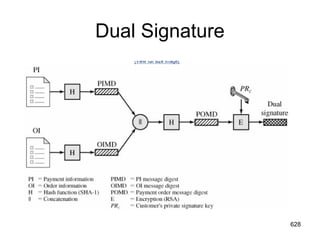
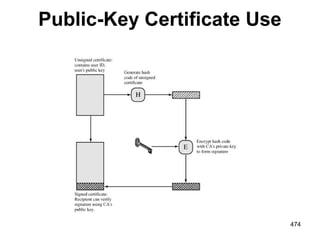
![Dual Signature
The customer takes the hash (using SHA-1) of the PI
and the hash of the OI, concatenates them, and hashes
the result.
Finally, the customer encrypts the final hash with his
or her private signature key, creating the dual
signature. This can be summarized as: DS=E(PRc,
[H(H(PI)||H(OI))])
627](https://image.slidesharecdn.com/cns-140517233933-phpapp02/85/Cyptography-and-network-security-627-320.jpg)