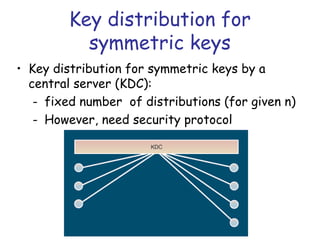
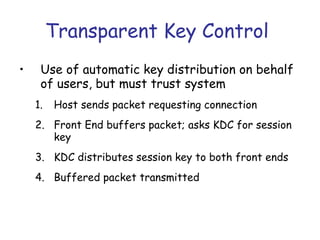
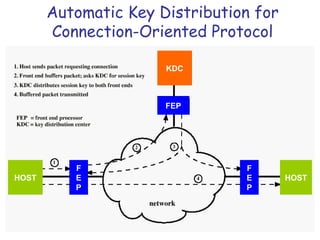
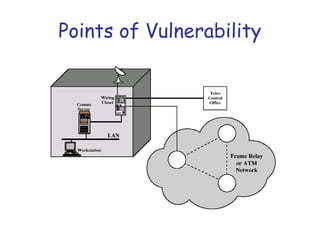
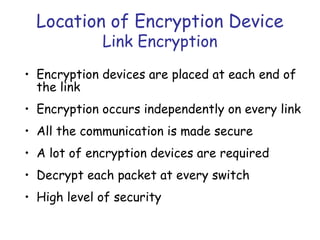
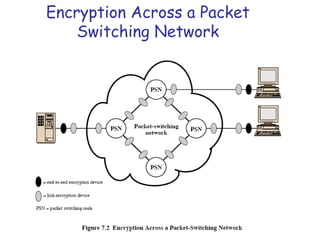
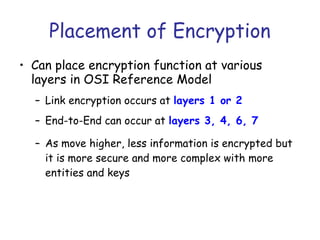
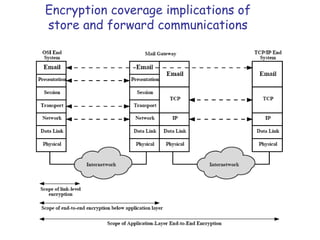
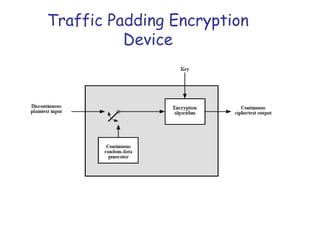
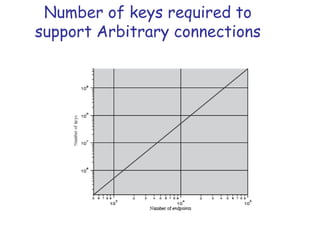
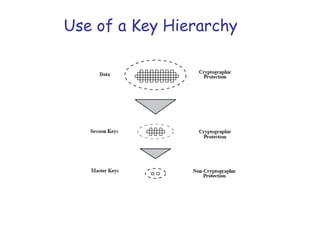
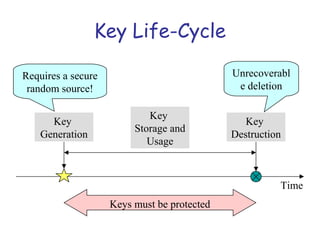
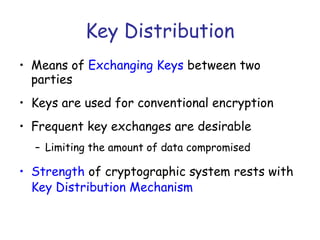
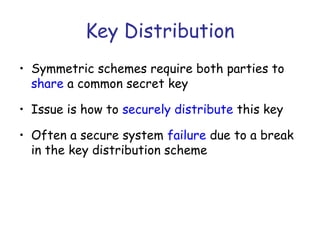
Symmetric encryption uses the same key to encrypt and decrypt data, providing confidentiality. Keys must be distributed securely between parties. Common approaches involve using a key distribution center (KDC) that shares secret keys with parties and can provide temporary session keys. Link encryption protects data as it travels over each network link, while end-to-end encryption protects data for its entire journey but leaves some header data unencrypted. Key distribution, storage, renewal and replacement are important aspects of maintaining security when using symmetric encryption.









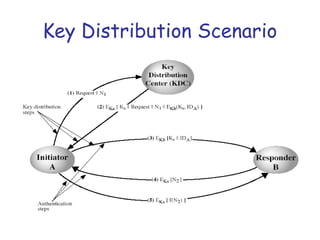

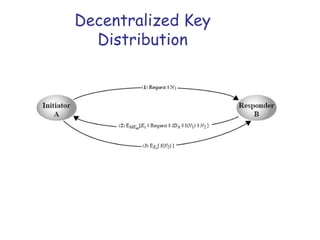
![Key Distribution Scenario
3. A stores KS and forwards information for B
i.e., EKB[KS||IDA]
4. B sends a nonce to A encrypted with KS
5. A responds by performing some function on
nonce like incrementing
The last two steps assure B that the
message it received was not a replay](https://image.slidesharecdn.com/cns-13f-lec07-keydistribution-131023123327-phpapp02/85/key-distribution-in-network-security-27-320.jpg)