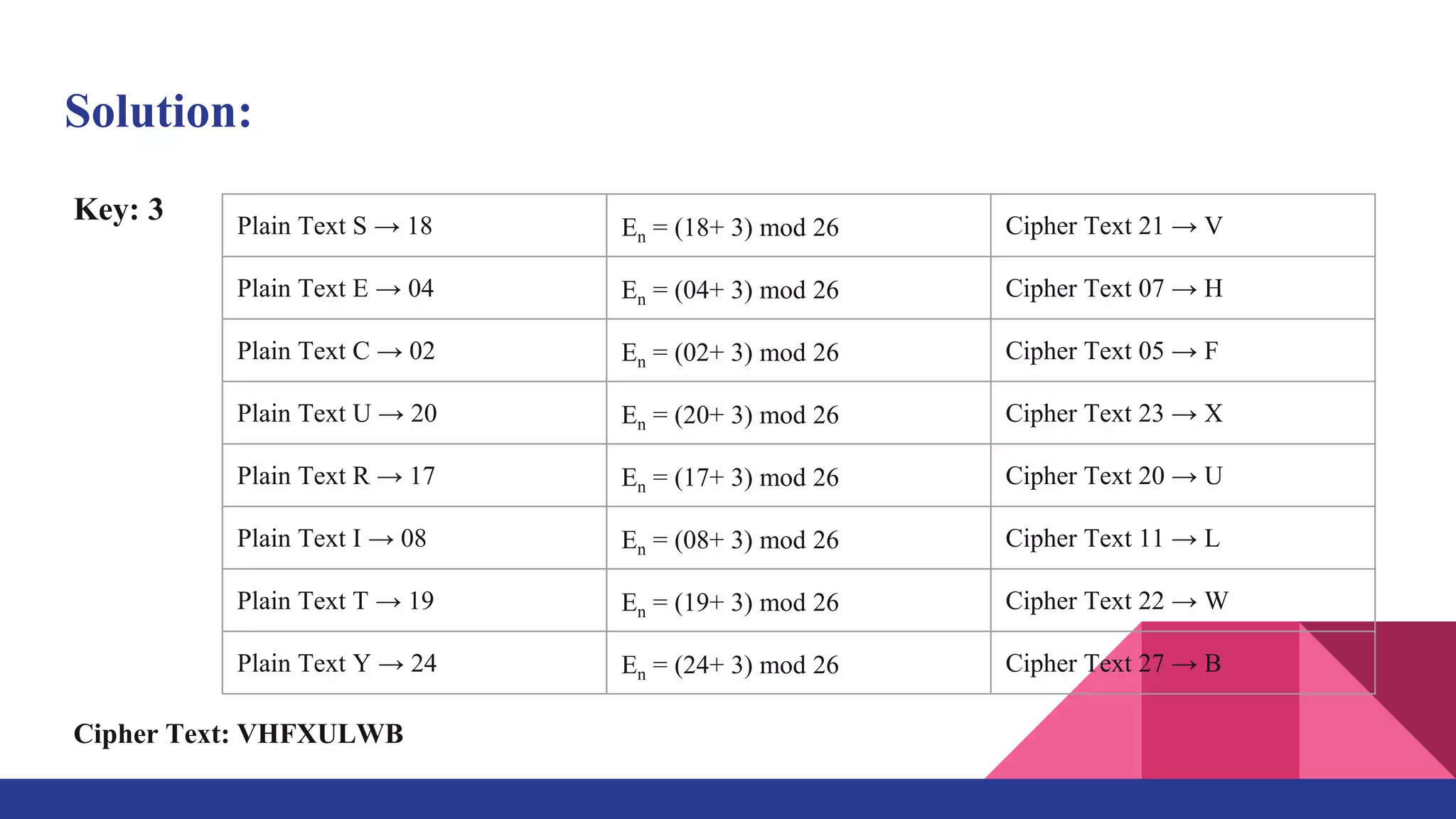
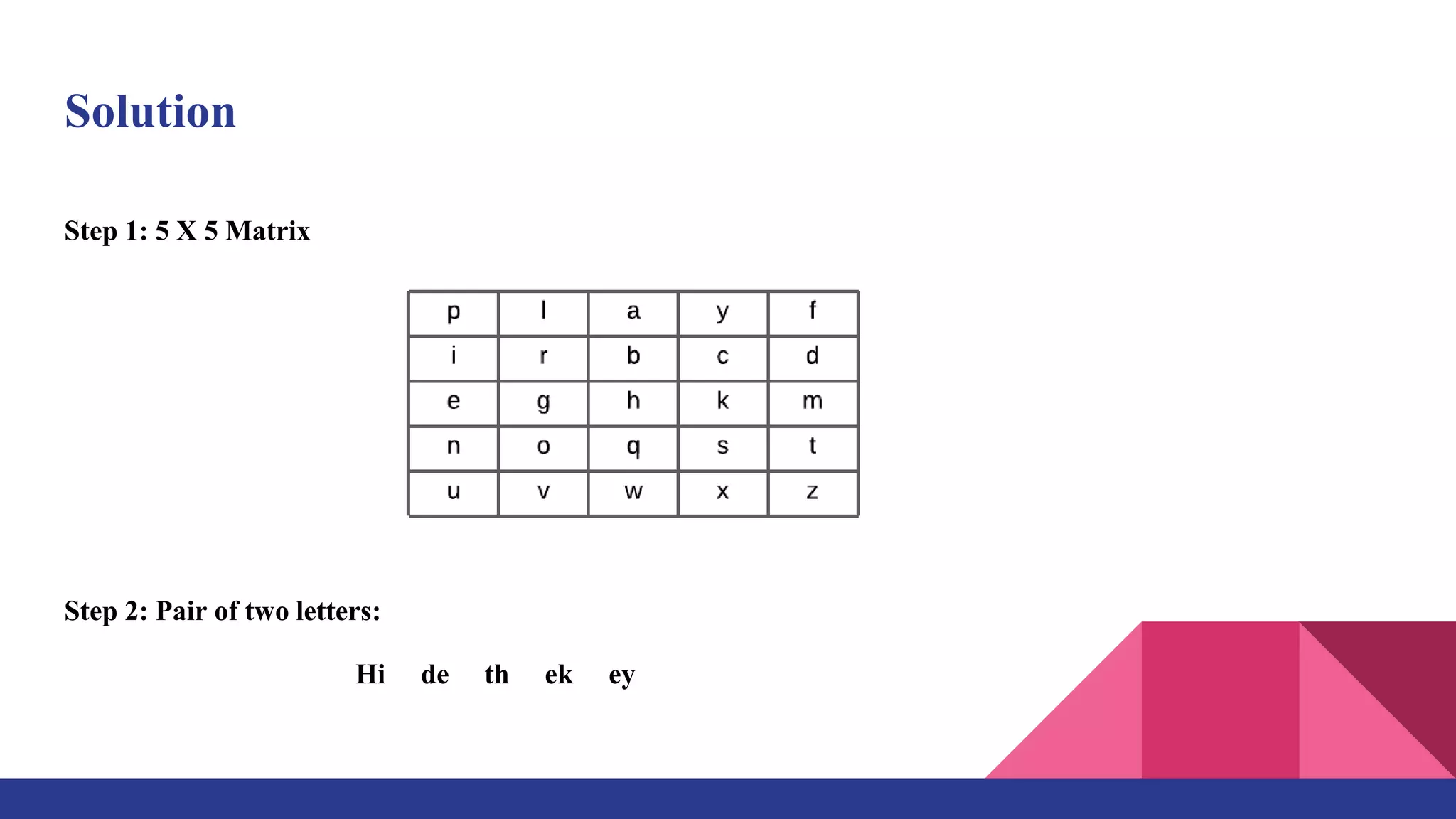
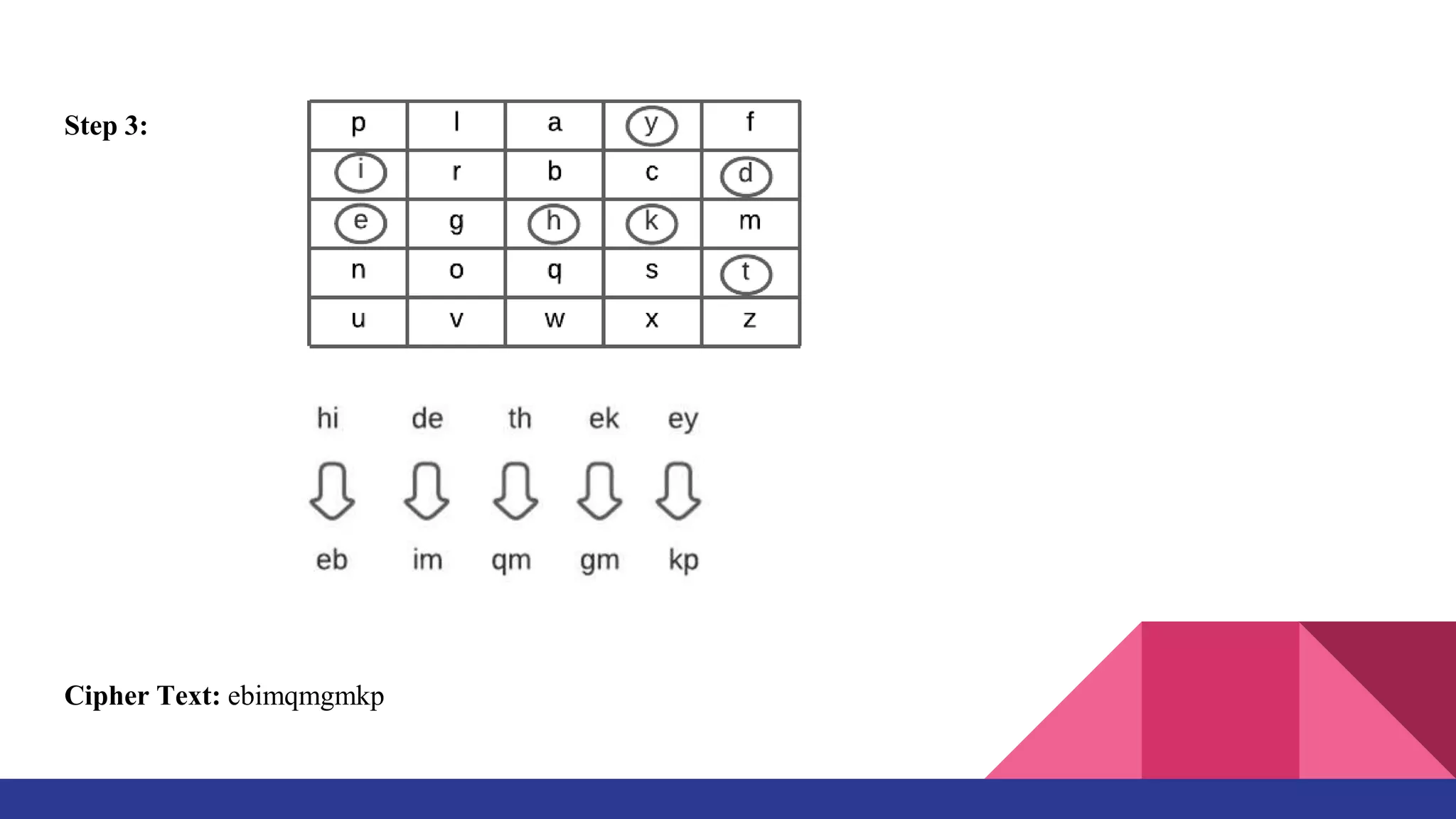
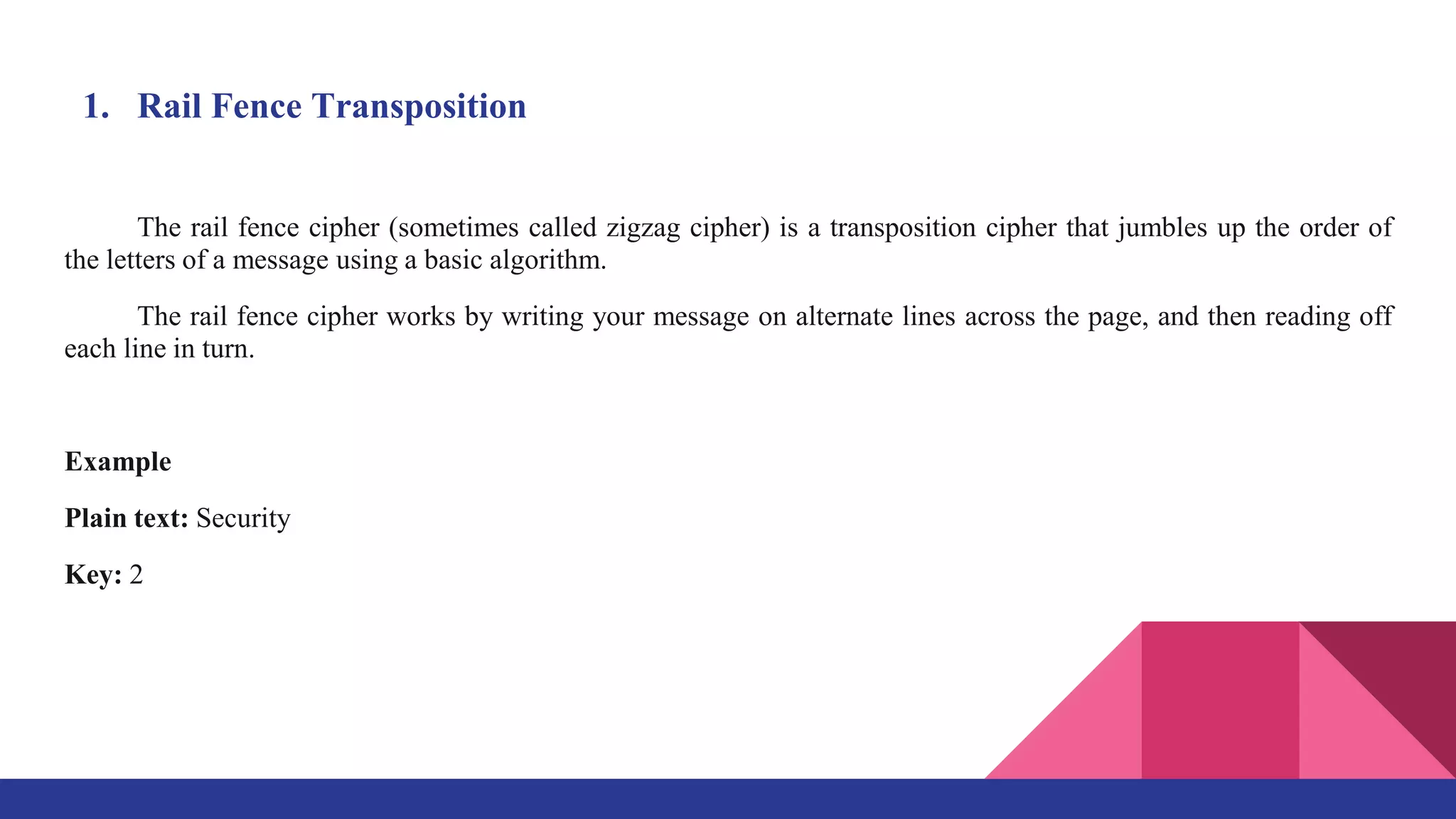
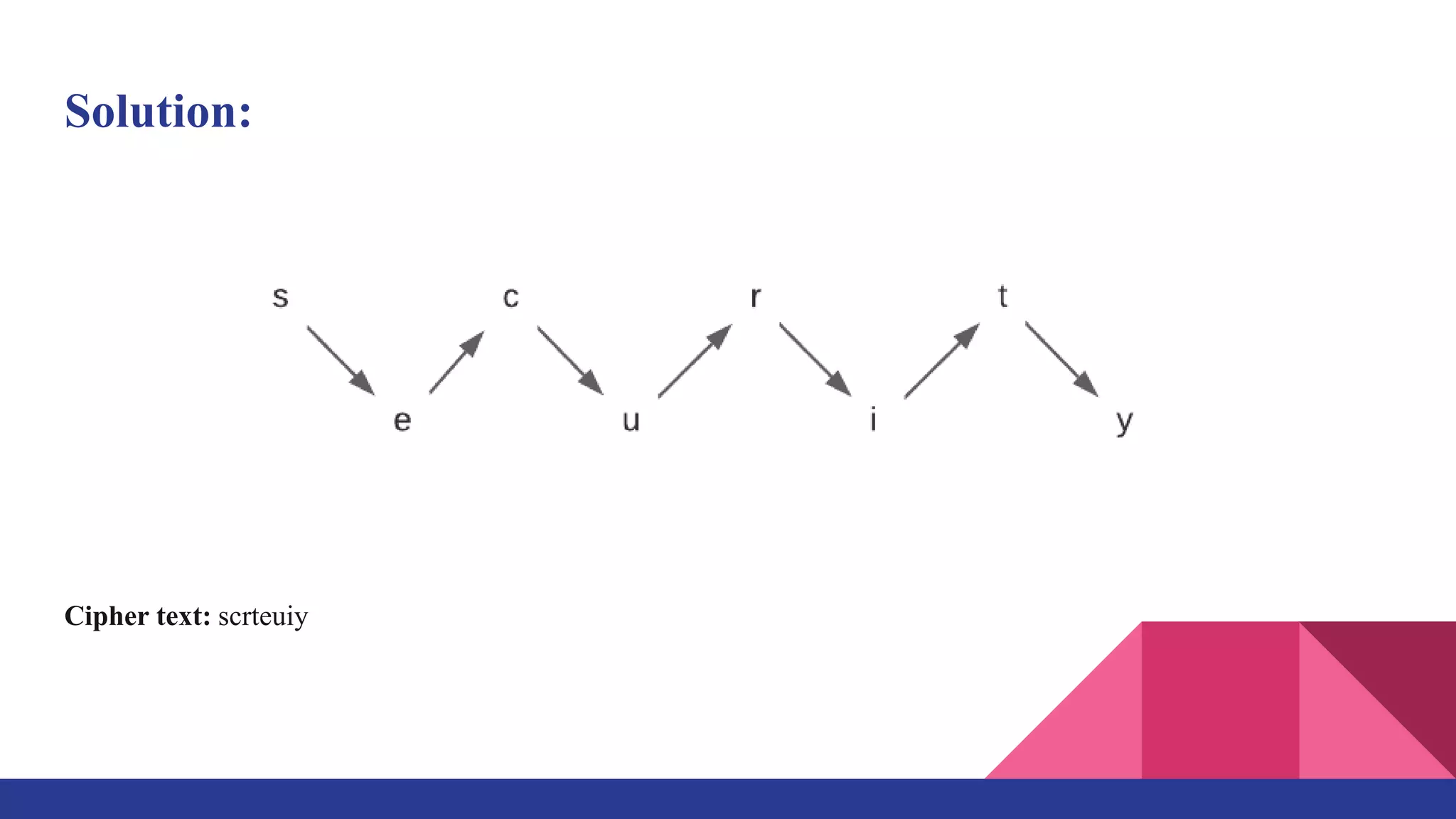
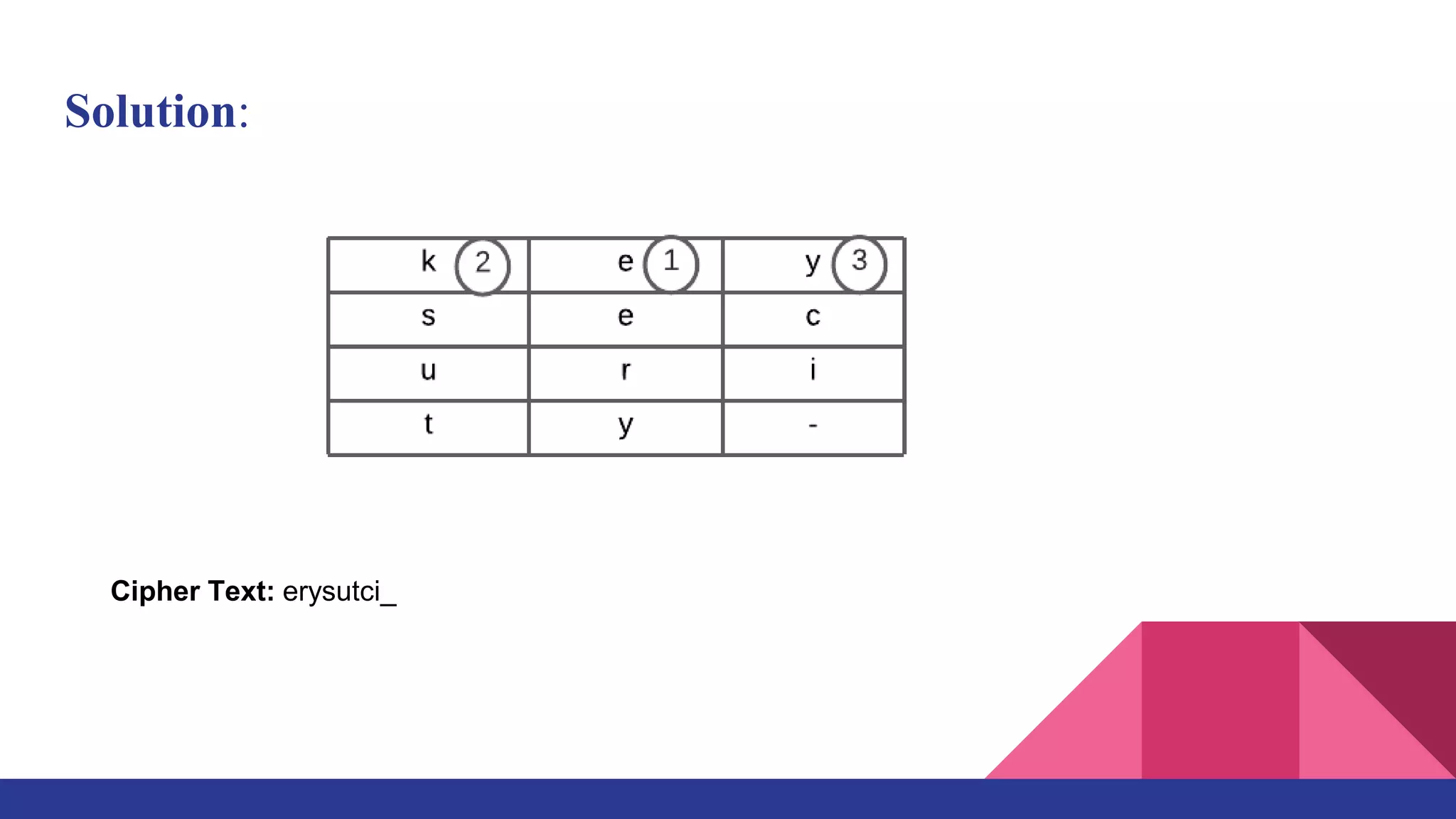
The document presents a web-based application for encrypting messages using substitution and transposition techniques like the Caesar cipher, Playfair cipher, rail fence transposition, and simple columnar transposition. The application aims to securely transmit sensitive information over the internet by making encryption accessible without specialized cryptography knowledge. It explains each encryption technique with examples, and concludes that combining multiple ciphers in the system ensures confidentiality and makes encrypted messages difficult to crack without the key.