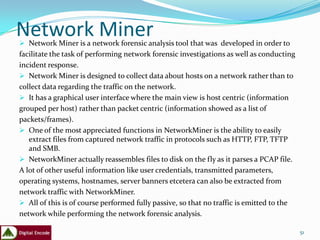
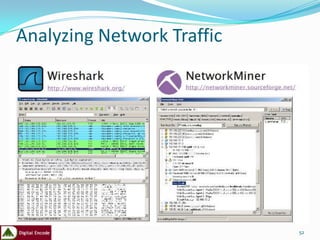
The document provides an overview of a training on practical demonstrations of digital forensic tools. It introduces the instructor and their qualifications. The agenda includes an introduction to digital forensics, computer forensic processes, and demonstrations of forensic tools like FTK Imager and EnCase. Key points covered are the forensic investigation process of acquiring, analyzing, and reporting evidence from a computer, and types of data like active, latent, and archival that can be extracted.
























![Data in Unexpected Places
Anti-virus alerts, real-time anti-virus scans
License enforcement / application metering
[anything]Management Software
Patch management
Software management
Configuration management
Asset management
25](https://image.slidesharecdn.com/latestpresentation-121126094747-phpapp02/85/Latest-presentation-25-320.jpg)














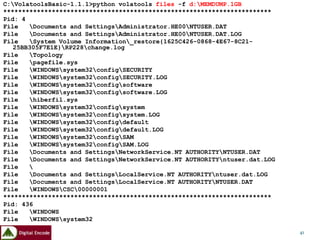





![FSPC and FRUC
FSPC is the server component, which resides on your forensic workstation. This
system will be where all of the data you collect is stored and managed, and then
eventually analyzed.
FSPC [-d case dir] [-n case name] [-p port] [-i investigator]
[-l logfile] [-c] [-v] [-h]
-d case dir....Case directory (default: cases)
-n case name...Name of the current case
-i invest......Investigator's name
-p port........Port to listen on (default: 7070)
-l logfile.....Case logfile (default: case.log)
-v.............Verbose output (more info, good for monitoring
activity)
-c.............Close FSP after CLOSELOG command sent (best used
when collecting data from only one system)
-h.............Help (print this information)
Ex: C:>fspc -d cases -n testcase -i "H. Carvey"
C:>fspc -n newcase -p 80
47](https://image.slidesharecdn.com/latestpresentation-121126094747-phpapp02/85/Latest-presentation-46-320.jpg)
![FRUC is the client component, used to collect data from "victim" system. Download the
zipped archive, and extract all of the files (2 EXE files and several DLLs) into a directory,
add your third party tools, update your INI file (the default is "fruc.ini") appropriately,
and then burn everything to a CD (or copy it to a thumb drive). Then you're ready.
Launch the FRUC with the "-h" switch and you'll see...
FRUC v 1.2 [-s server IP] [-p port] [-f ini file] [-h]
First Responder Utility (CLI) v.1.2, data collection utility
of the Forensics Server Project
-s system......IP address of Forensics Server
-p port........Port to connect to on the Forensics Server
-f file........Ini file to use (use other options to override ini file configuration settings)
-v.............Verbose output (more info, good for monitoring activity)
-h.............Help (print this information)
Ex: C:>fruc -s -p -f
48](https://image.slidesharecdn.com/latestpresentation-121126094747-phpapp02/85/Latest-presentation-47-320.jpg)