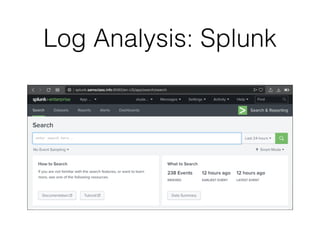
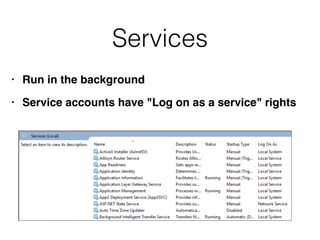
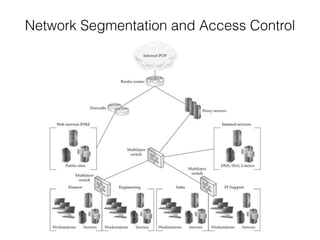
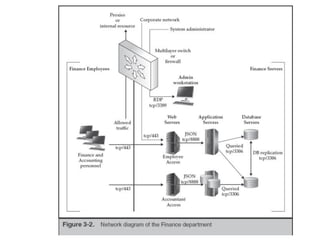
This document discusses three key areas of preparation for effective incident response: preparing the organization, preparing the incident response team, and preparing the infrastructure. It provides details on identifying risks, policies to promote successful IR, educating users, defining the IR team mission, training the team, equipping the team, asset management, hardening hosts, implementing centralized logging, network segmentation, access controls, and documentation. The overall goal is to outline steps organizations can take before an incident occurs to facilitate rapid identification, containment, eradication and recovery.