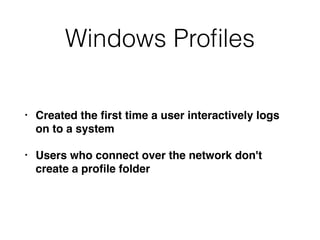
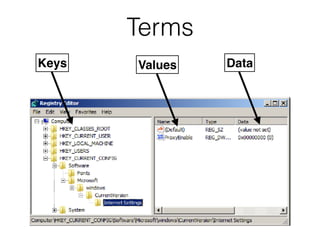
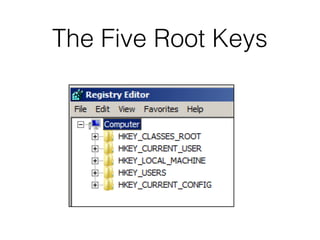
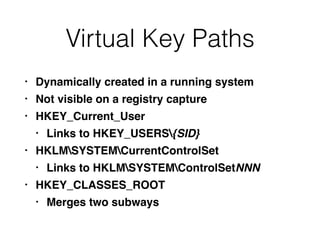
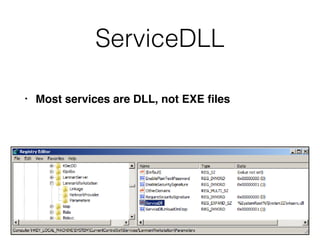
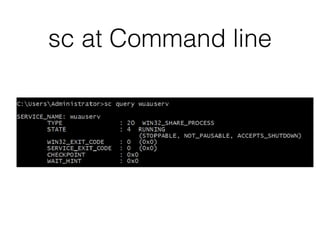
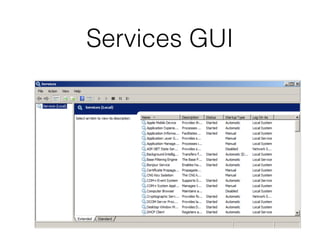
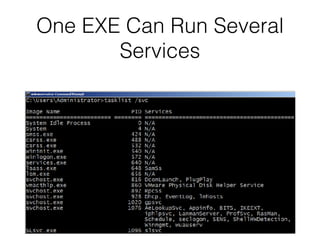
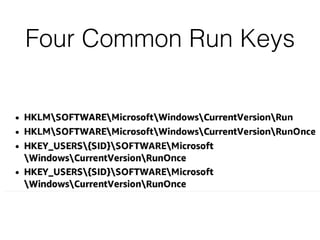
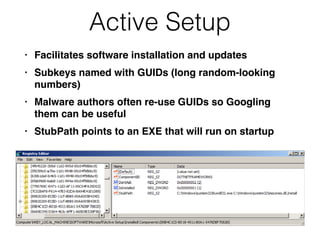
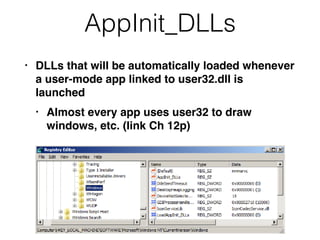
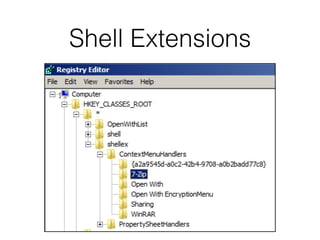
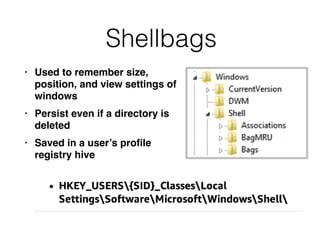
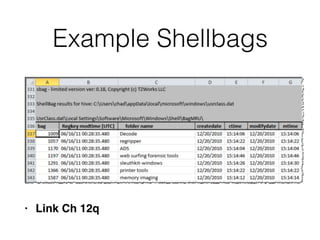
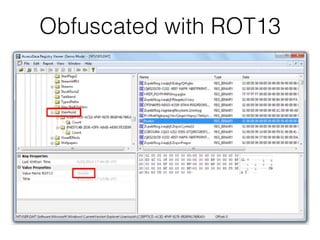
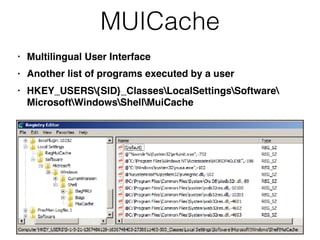
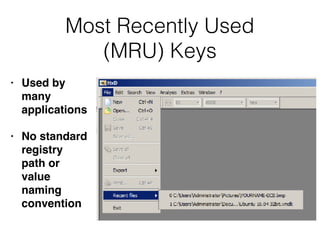
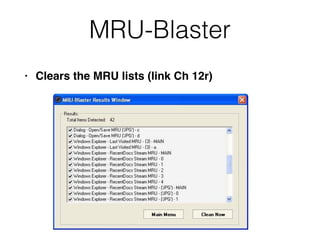
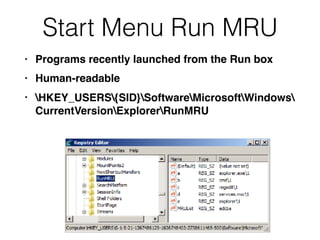
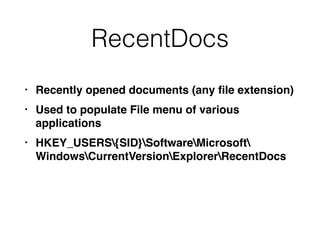
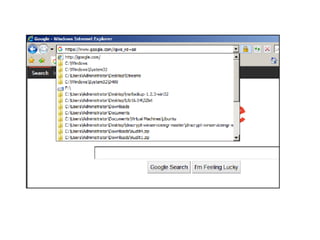
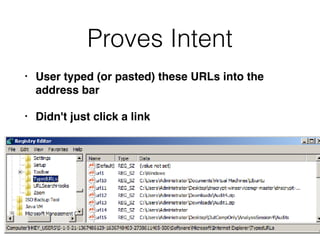
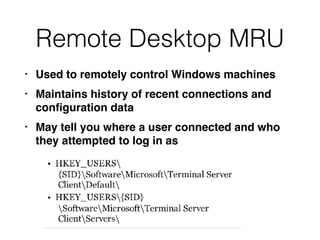
The document covers the investigation of Windows systems with a focus on the Windows registry, detailing its structure including hive files, keys, and values which are essential for forensic analysis. It outlines important artifacts, registry timestamps, and auto-run keys that could indicate malicious activity. Additionally, it describes user-specific registry information and various tools available for registry analysis, emphasizing the importance of understanding these elements in incident response.