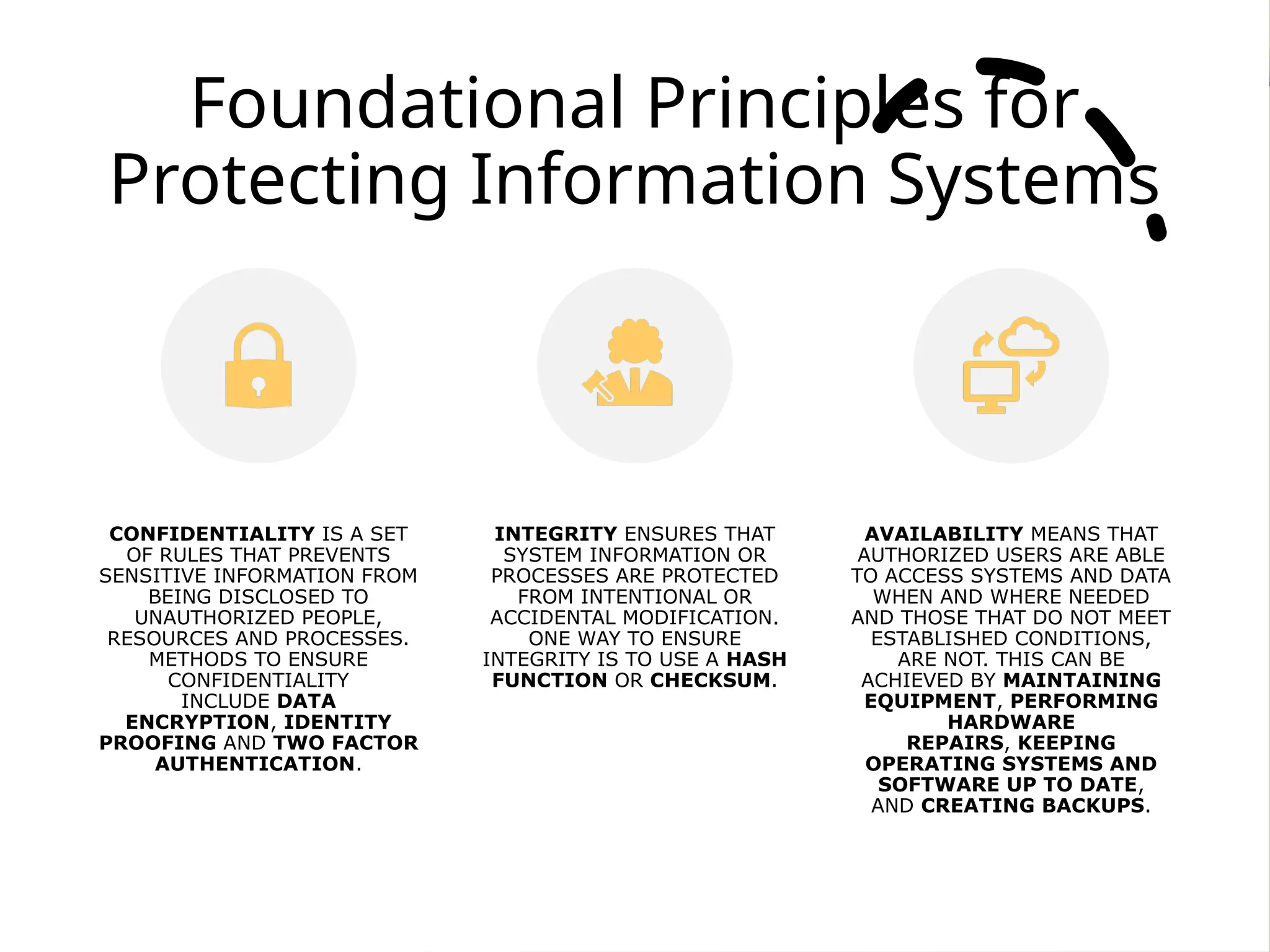
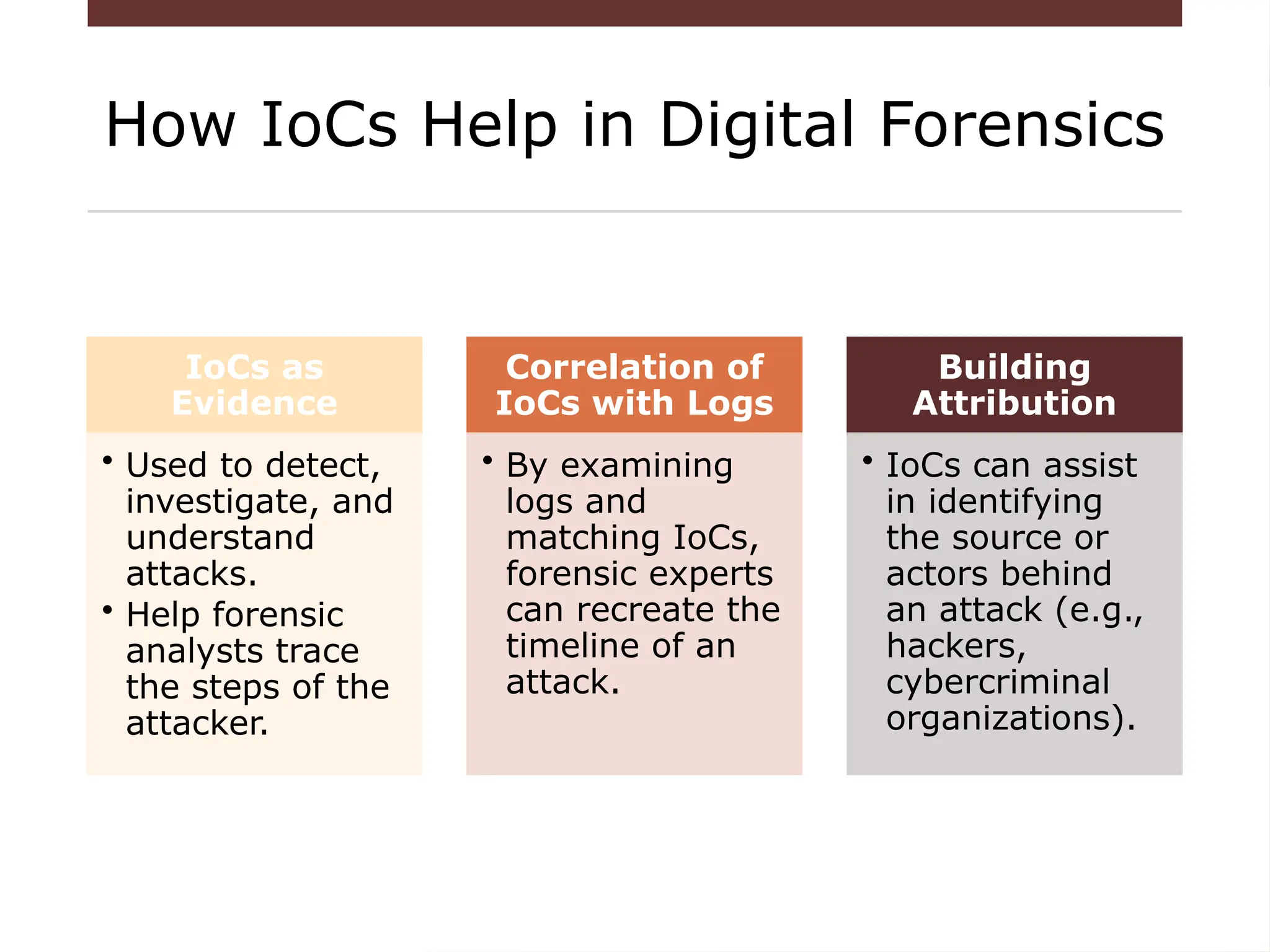
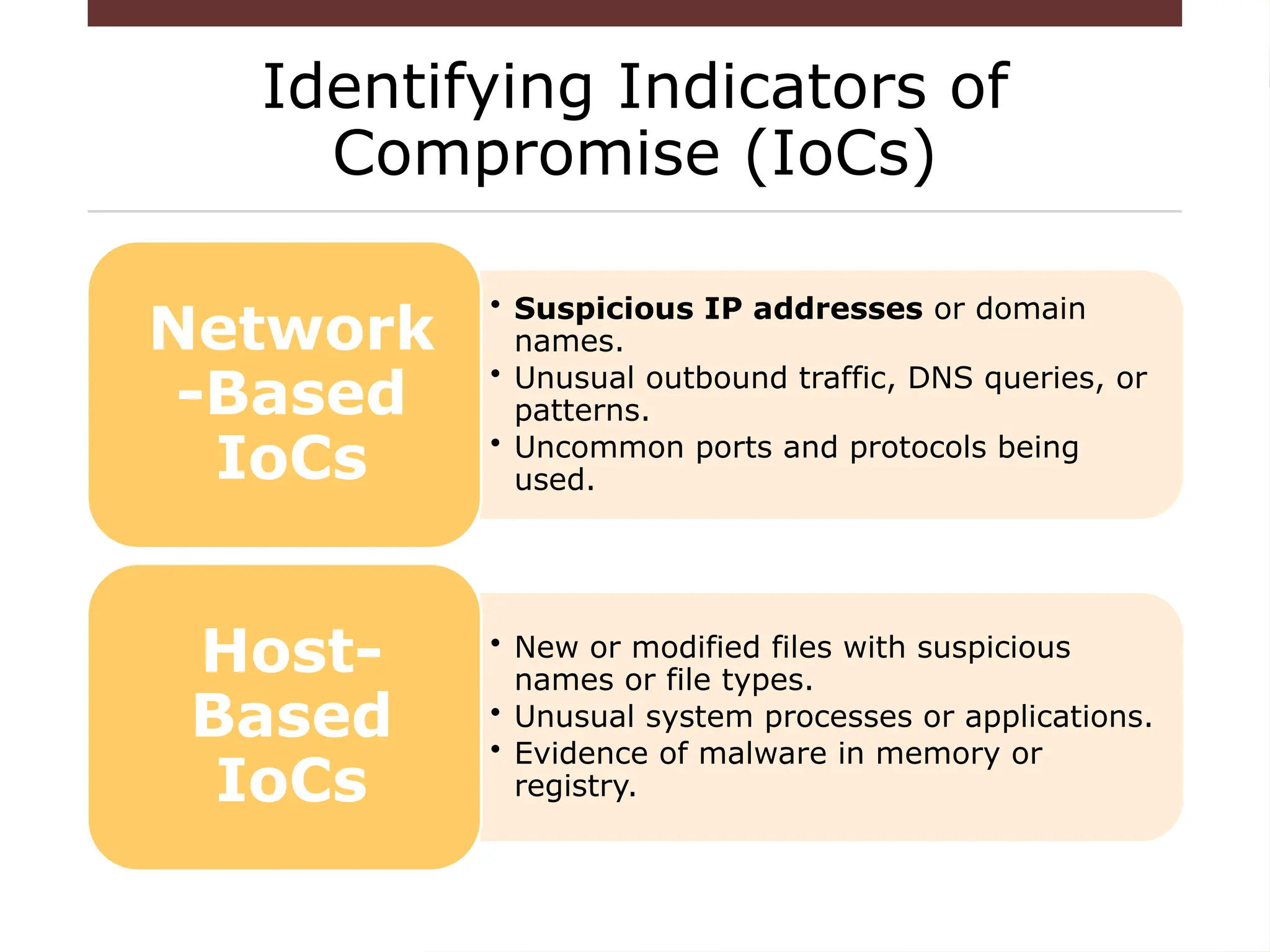
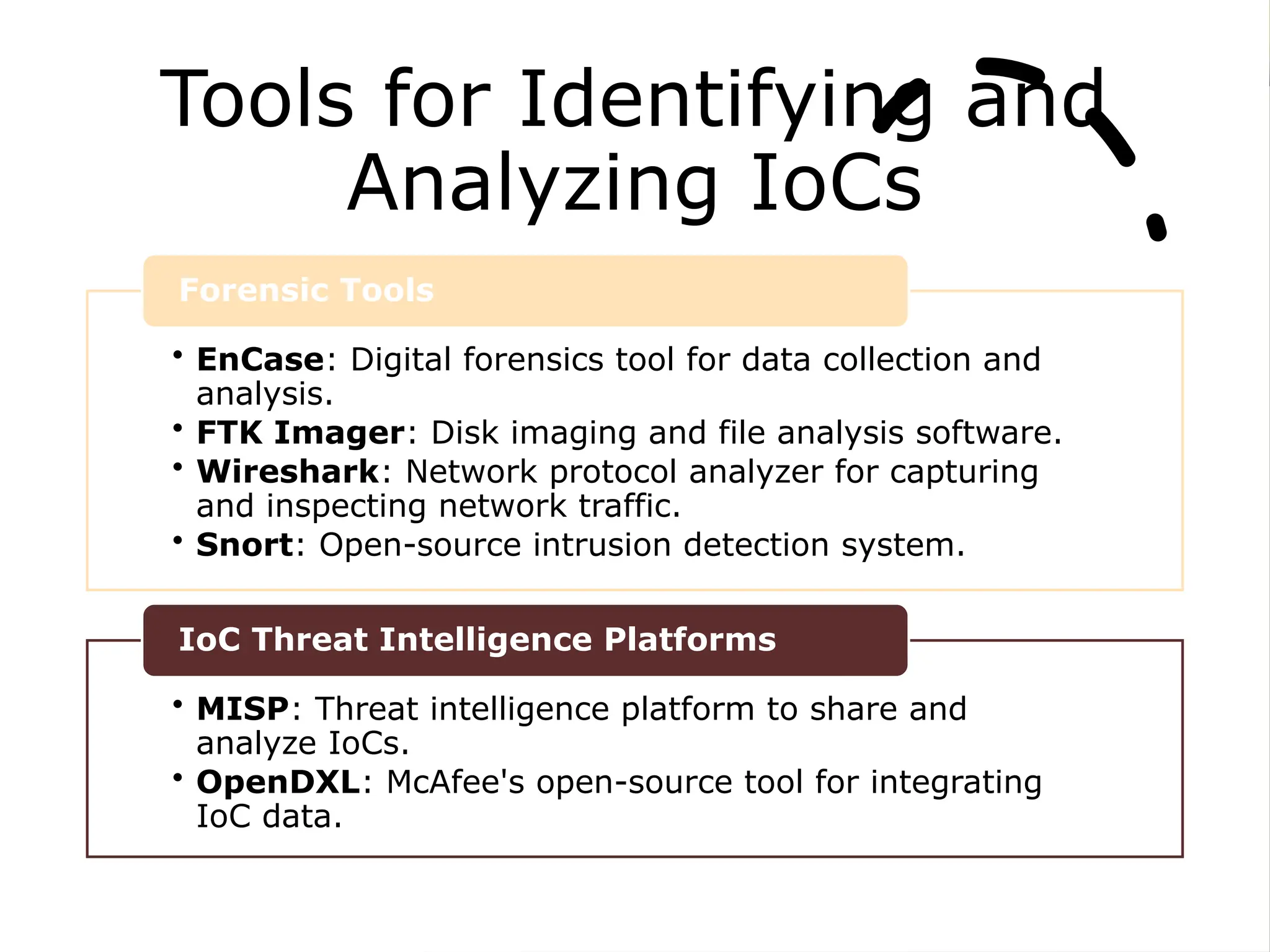
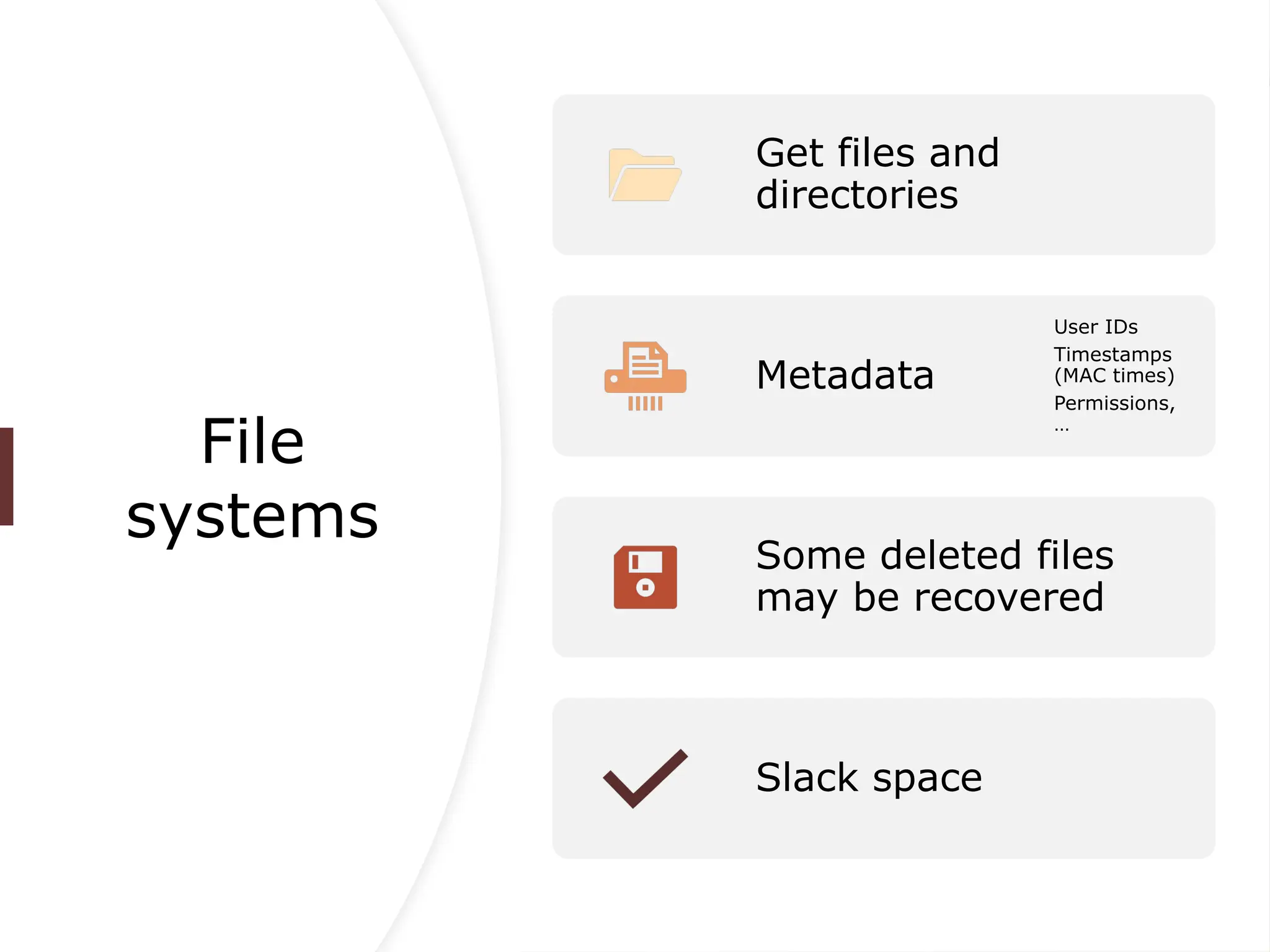
The document provides an overview of cybersecurity, emphasizing the protection of systems, networks, and data from digital threats while highlighting the importance of confidentiality, integrity, and availability. It outlines indicators of compromise (IOCs) used in identifying and tracking cyberattacks, detailing various threats like malware, phishing, and advanced persistent threats (APTs). Furthermore, it explores digital forensics, phases of investigation, and the need for standardization and research in the field.