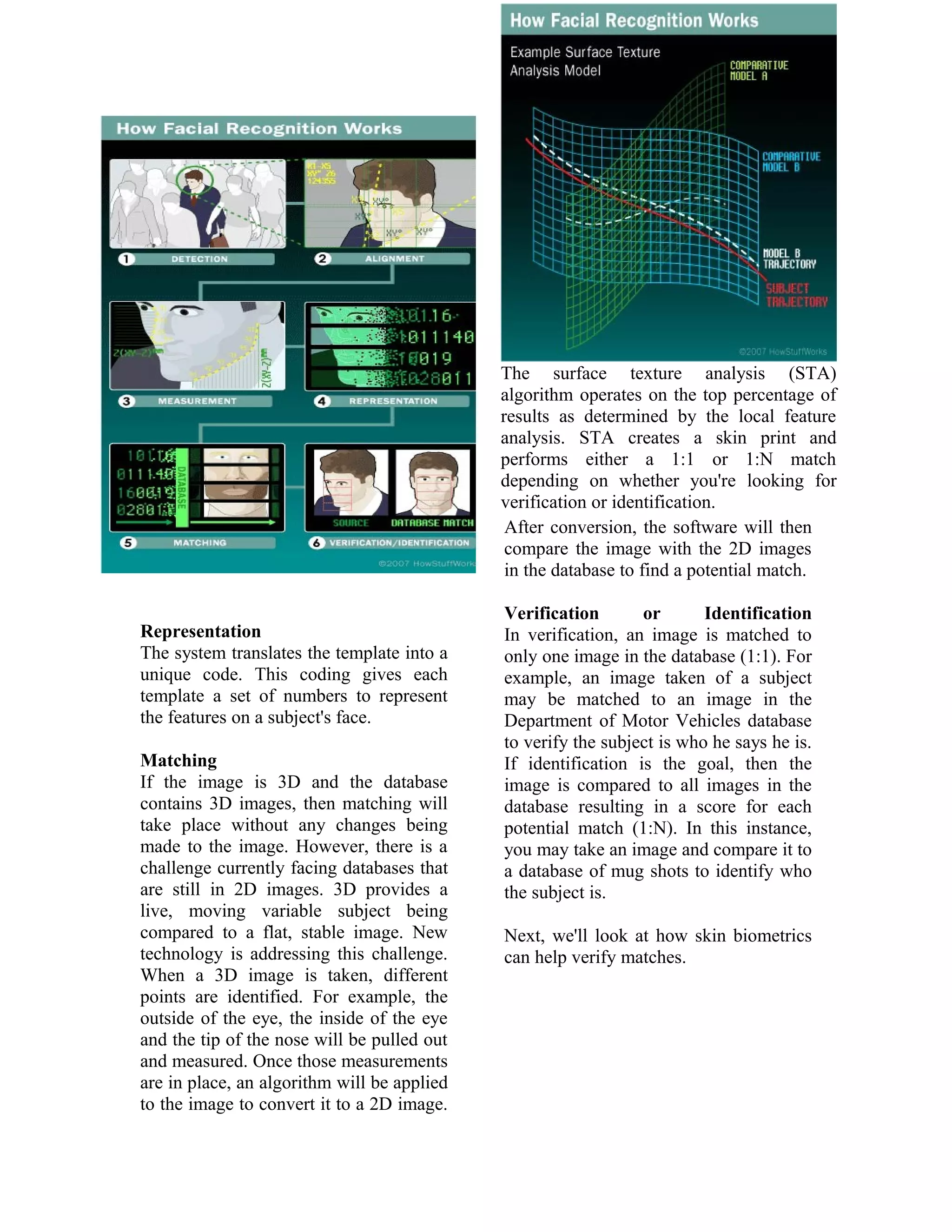
This document summarizes face recognition technology. It discusses how face recognition works by measuring facial landmarks and creating a face print for identification and verification purposes. Recent advances include 3D facial recognition, which can identify faces from different angles. The document outlines the history of facial recognition and discusses current and potential uses, such as border security and ATM verification. However, it also notes privacy and security concerns about the use of facial recognition without consent.