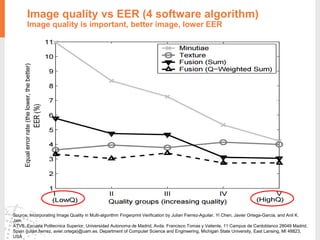
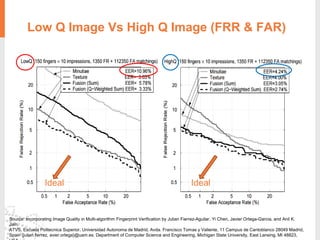
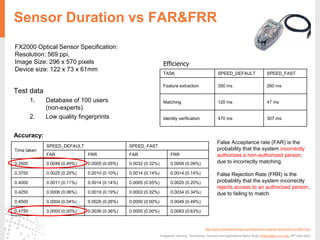
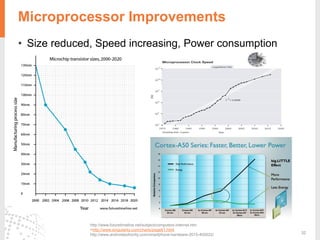
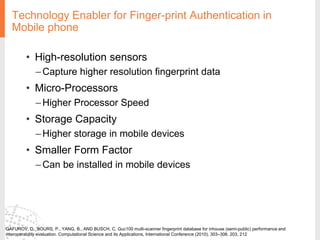
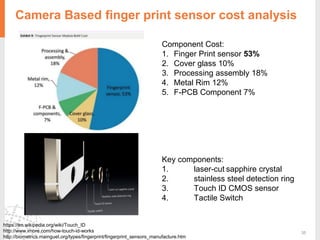
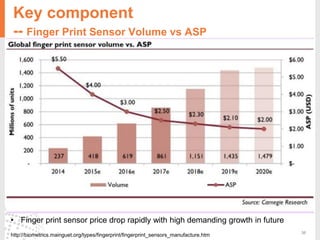
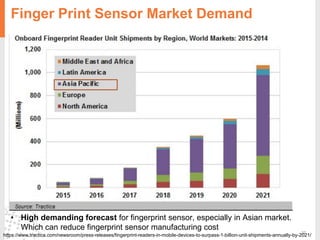
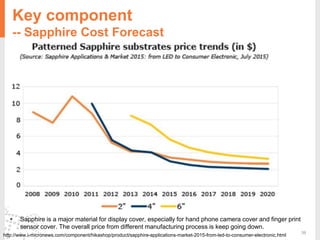
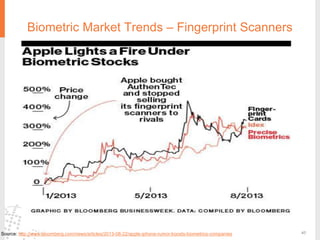
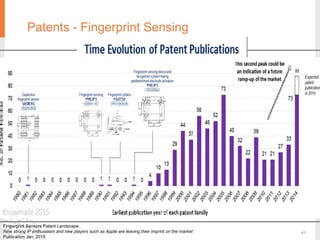
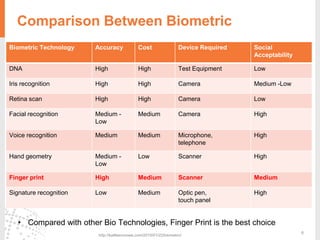
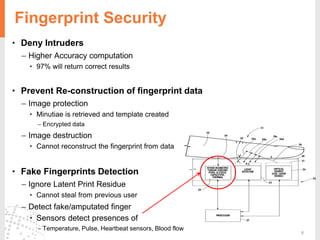
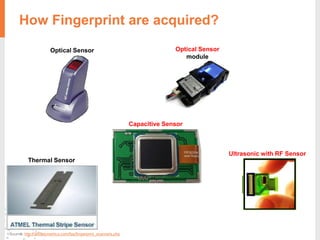
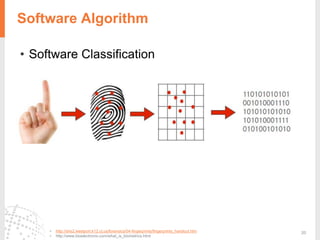
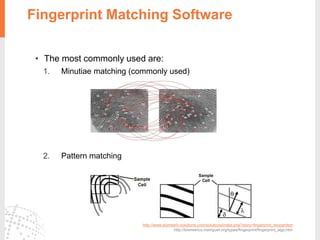
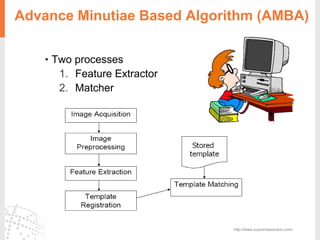
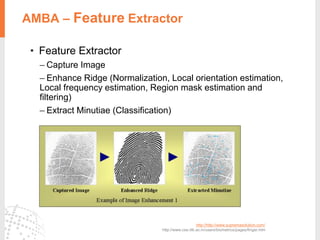
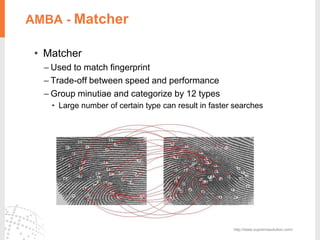
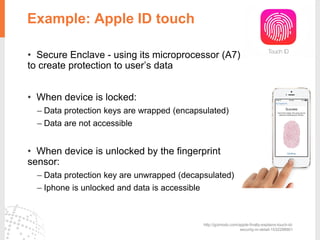
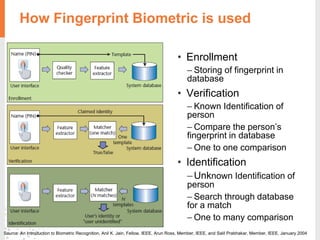
The document provides a comprehensive overview of fingerprint biometric technology, detailing its unique characteristics, advantages over traditional security methods, and various applications. It highlights the high accuracy and security of fingerprint recognition compared to other biometric types, outlines the technology's hardware and software requirements, and discusses market trends and consumer acceptance. Fingerprint technology is positioned as a reliable and convenient solution for personal and mobile security, facilitating a shift towards a new lifestyle in the digital age.



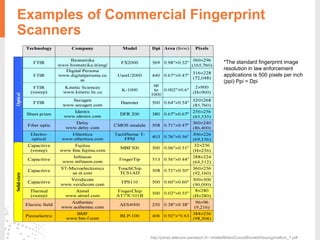

![Optical Resolution vs Accuracy
http://biolab.korea.ac.kr/pubs/JainFpMatching_IEEEComp10.pdf
Jain, Feng, Nandakumar, Anil K. Kain, Jianjiang Fengm Karthik Nandakumar, 2010. Fingerprint Matching. Computer, 0018-9162, 36-44.
[a] http://itlaw.wikia.com/wiki/False_non-match_rate
[b] http://itlaw.wikia.com/wiki/False_match_rate
False Non-Match Rate (FNMR) is the failure of a biometric system to identify a biometric
subject or to verify the legitimate claimed identity of a biometric subject.
False Match Rate (FMR) is the proportion of the completed biometric non-match
comparison trials that result in a false match. [b]
False Positive Identification Rate (FPIR) occurs when the system finds a hit for a query
fingerprint that is not enrolled in the system.
False Negative Identification Rate (FNIR) occurs when it finds no hit or a wrong hit for
a query fingerprint enrolled in the system.](https://image.slidesharecdn.com/mt5009presentation-biometric-fingerprintfinalversion-160417073707/85/Biometrics-fingerprint-sensors-28-320.jpg)