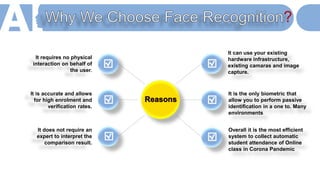
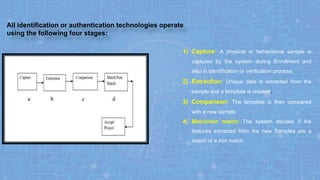
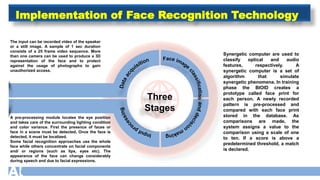
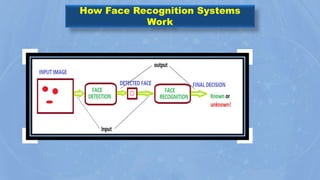
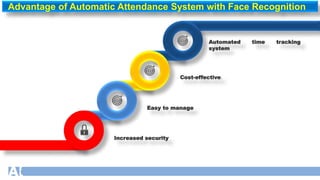
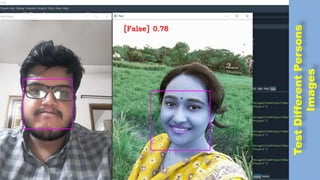
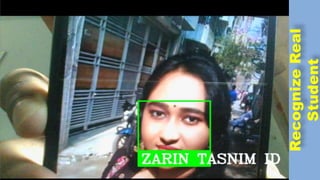
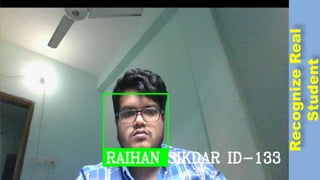
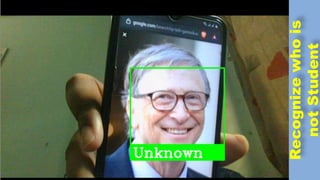
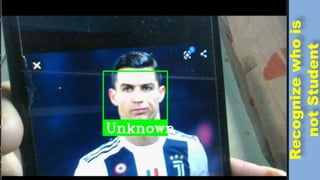
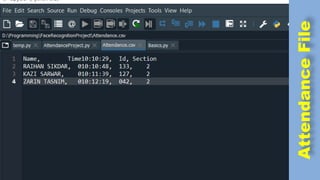
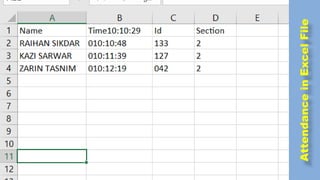
The document discusses face recognition technology for use in an automatic attendance system. It first defines biometrics and face recognition, explaining that face recognition identifies individuals using facial features. It then covers how face recognition systems work by detecting nodal points on faces to create unique face prints. The document proposes using such a system to take student attendance in online classes during the pandemic, noting advantages like ease of use, increased security, and cost effectiveness. It provides examples of how the system would capture images, analyze features, and recognize enrolled students to record attendance automatically.