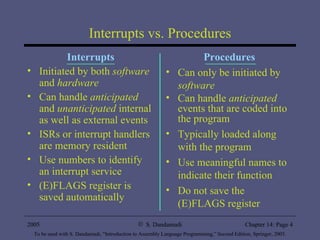
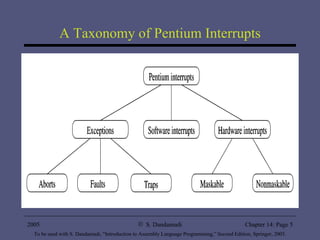
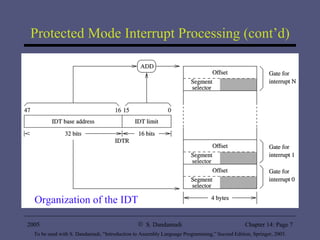
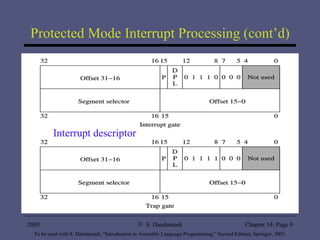
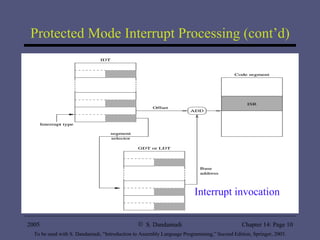
The document provides an overview of interrupt processing in protected mode, including a taxonomy of interrupts, how interrupts alter program flow, differences between interrupts and procedures, interrupt descriptor table organization, interrupt invocation process, dedicated interrupts, software interrupts, file I/O system calls, and hardware interrupts. It describes interrupt handling at a high level and key concepts like interrupt service routines, interrupt descriptor table, interrupt enable flag instructions, and interrupt triggering mechanisms.