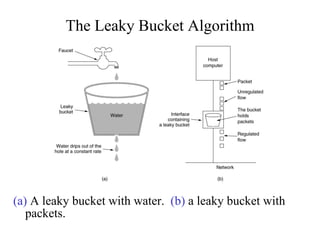
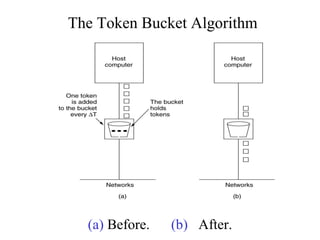
The document discusses several algorithms used for congestion control in TCP/IP networks, including slow start, congestion avoidance, fast retransmit, fast recovery, random early discard (RED), and traffic shaping using leaky bucket and token bucket algorithms. Slow start and congestion avoidance control the transmission rate by adjusting the congestion window size. Fast retransmit and fast recovery allow quicker retransmission of lost packets without waiting for timeouts. RED proactively discards packets before buffer overflow. Leaky bucket and token bucket algorithms shape traffic flow through use of buffers and tokens to smooth bursts and control transmission rates.