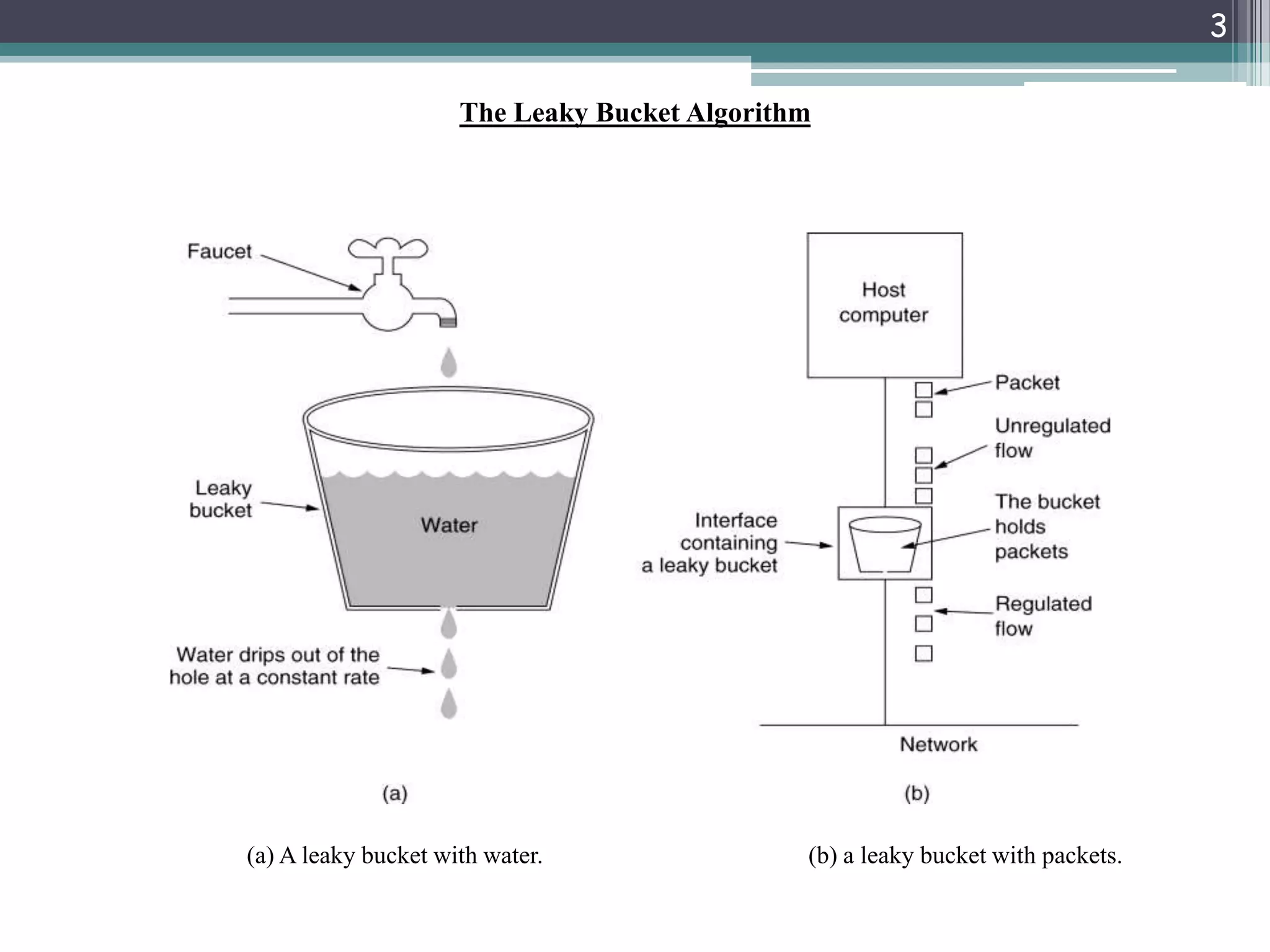
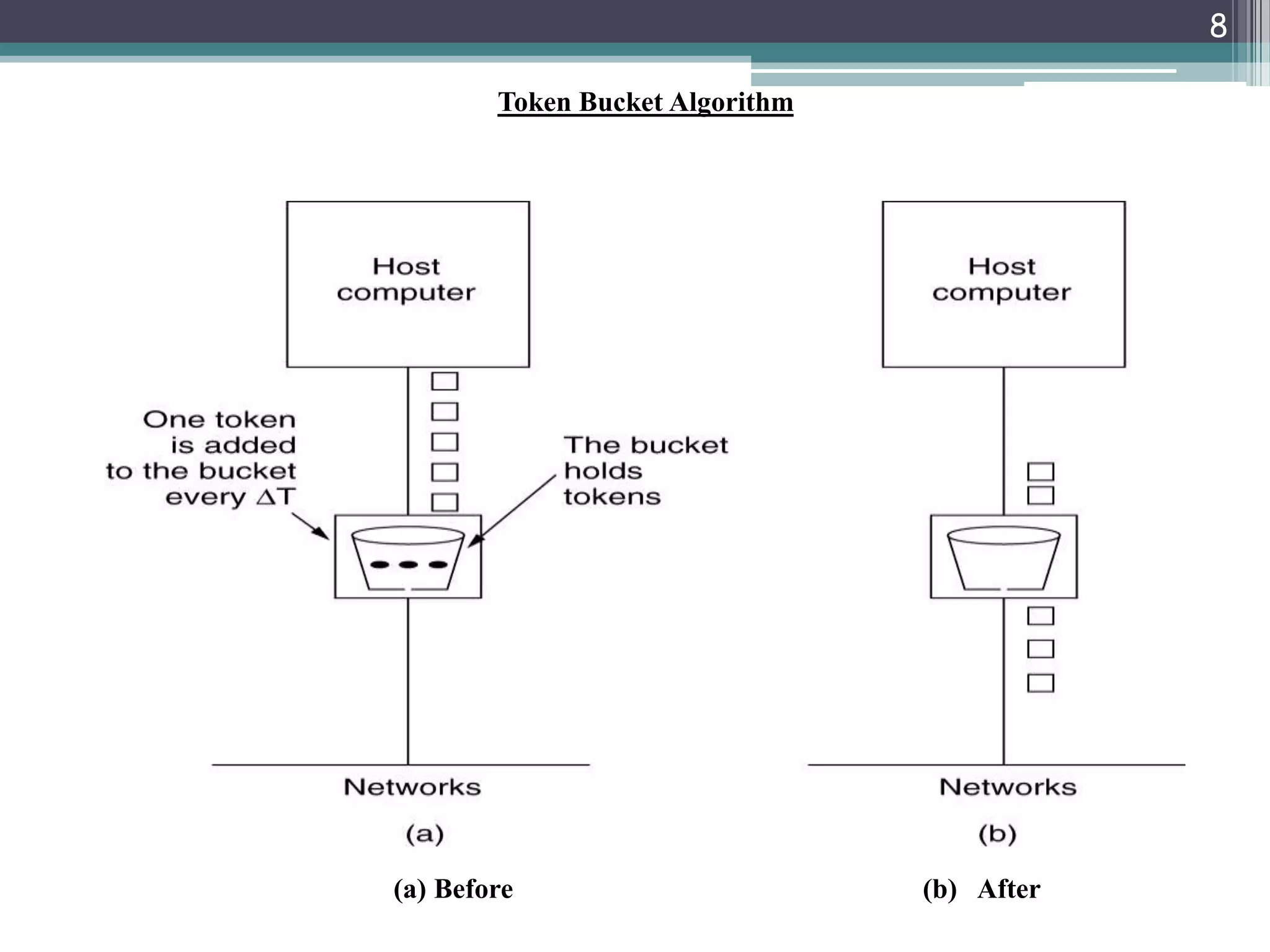
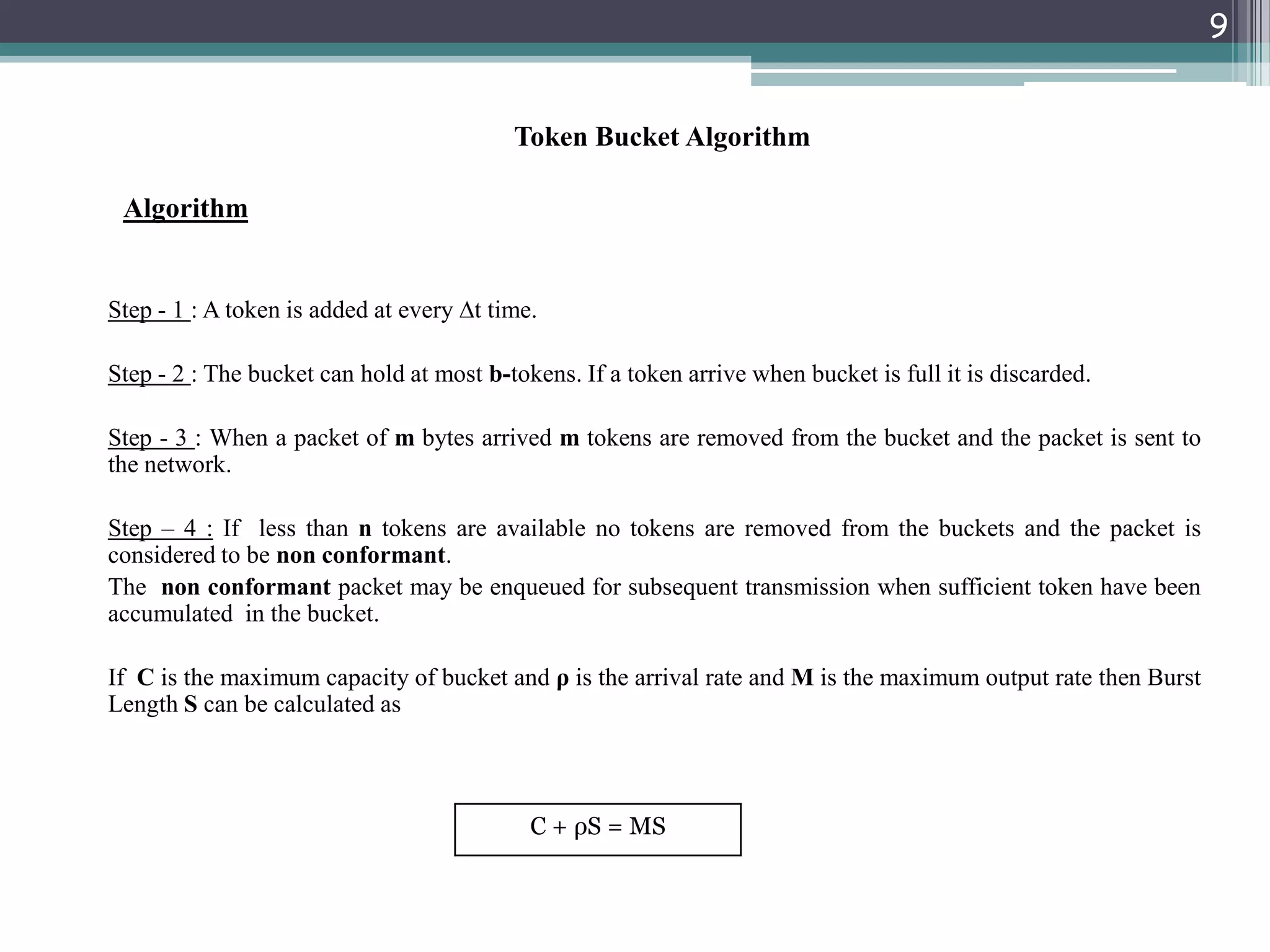
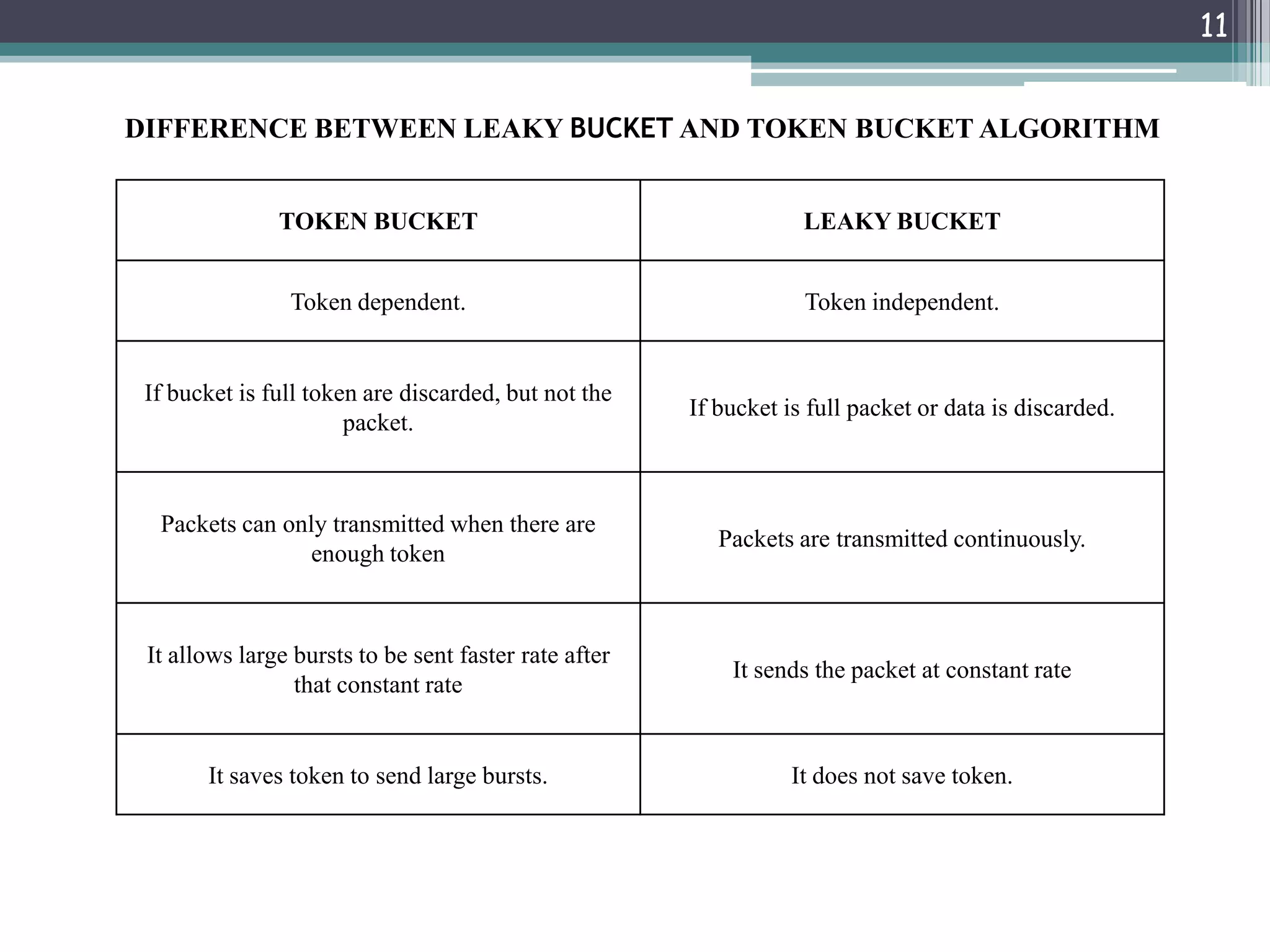
The document explains traffic shaping as a method to regulate data flow rates in networks, highlighting two algorithms: the leaky bucket and token bucket. The leaky bucket algorithm maintains a constant output rate while allowing variable input rates and discards excess packets if the buffer overflows, while the token bucket algorithm permits bursty traffic through token management. Key differences between the two algorithms include how they handle excess data and their capacity to allow bursts versus maintaining a constant data flow.