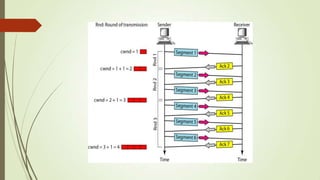
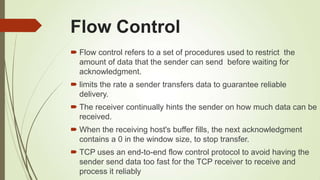
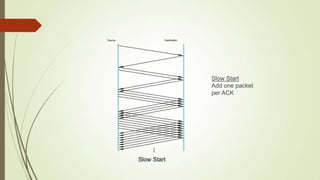
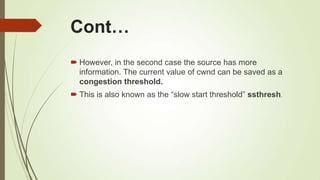
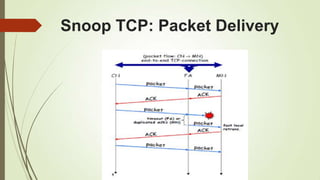
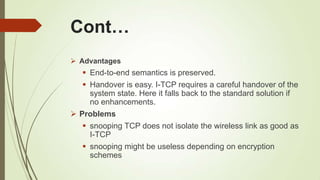
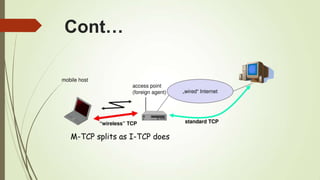
This document discusses various transport layer protocols for mobile networks. It begins by describing TCP and its mechanisms for congestion avoidance, flow control, slow start, and retransmission. It then covers several TCP variants including Tahoe, Reno, and Vegas. It also discusses indirect TCP, Snoop TCP, and Mobile TCP which aim to optimize TCP for wireless networks by handling retransmissions locally or splitting the connection. The document provides details on the algorithms and functioning of these different protocols.















![TCP Vegas
Developed by Brakmo, O'Malley & Peterson
[SIGCOMM,1994]
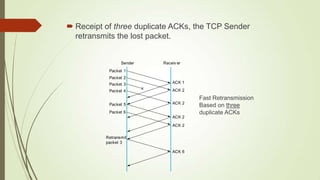
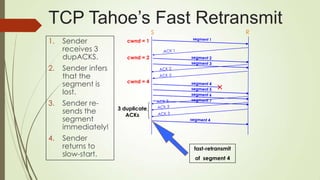
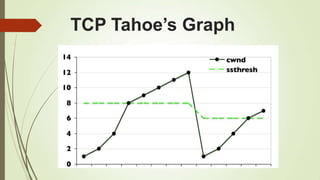
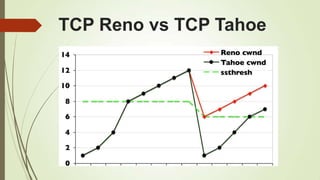
TCP Vegas emphasis on packet delay, not packet loss.
Sender-side protocol
Inter-operates with other TCP variants
Depends heavily on accurate calculation of the Base RTT
value.
If it is too small then throughput of the connection will be
less than the bandwidth available while if the value is too
large then it will overrun the connection.](https://image.slidesharecdn.com/group4-140512011411-phpapp02/85/Mobile-Transpot-Layer-24-320.jpg)


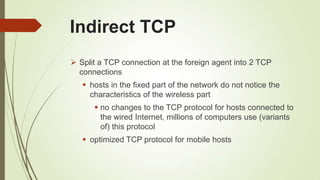
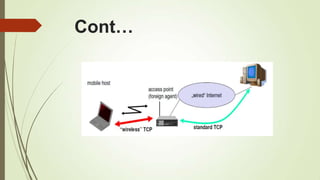

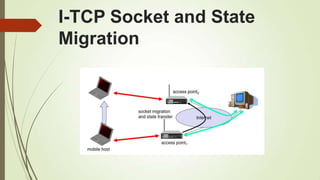




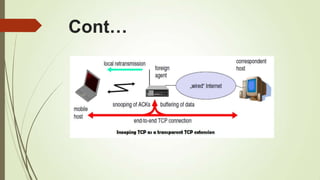











![References
[1]IEEE:TCP-FIT: An improved TCP congestion control algorithm and its
performance
[2]IEEE: Fast TCP flow control with differentiated services
[3]Afanasyev, A.; N. Tilley, P. Reiher, and L. Kleinrock (2010). "Host-to-host
congestion control for TCP―
[4] Jacobson, Van; Karels, MJ (1988). ―Congestion avoidance and control‖
[5]http://www.scribd.com/doc/63483753/Indirect-TCP-Snooping-TCP-Mobile-
TCP-Mobile-Transport-Layer#download
[6]Jian Ma, "A simple Fast TCP flow control in IP network or IP/ATM subnet – a
significant improvement over IP", November, 1997
[7]A Comparative Analysis of TCP Tahoe, Reno, New-Reno, SACK and Vegas
http://inst.eecs.berkeley.edu/~ee122/fa05/projects/Project2/SACKRENEVEGAS.p
df](https://image.slidesharecdn.com/group4-140512011411-phpapp02/85/Mobile-Transpot-Layer-51-320.jpg)
