The seminar presented by Mr. Anthony-Claret Onwutalobi at the University of Helsinki covered congestion control, highlighting the transition from old TCP to new TCP and the introduction of sliding window concepts. It emphasized the limitations of TCP, the slow start, congestion avoidance, fast retransmit, and fast recovery algorithms to improve data transmission reliability and efficiency. The document also outlined the roles of various techniques in managing network congestion and enhancing throughput.

![Introduction
Definition of Terms:
Congestion - is a condition of severe
delay caused by an overload of datagram
at one or more switching point (router).
[2]
Congestion Control: is a distributed
algorithm use by TCP to share network
resources among competing users. [3]](https://image.slidesharecdn.com/congestioncontrolavoidance-141210102755-conversion-gate02/85/Congestion-control-avoidance-2-320.jpg)



![Congestion Avoidance
congestion avoidance, is run any
time *except* when (re-)starting
and is responsible for estimating the
(dynamically varying) pipe size[4]
](https://image.slidesharecdn.com/congestioncontrolavoidance-141210102755-conversion-gate02/85/Congestion-control-avoidance-11-320.jpg)

![Slow Start and Congestion Avoidance
Algorithm
Slow Start and Congestion Avoidance Algorithm: [3]
Initialization for a given connection
Sets cwnd to one segment and ssthresh to 65535 bytes
The TCP output routine never sends more than minimum of cwnd and
the receiver’s advertised window
When congestion occurs (indicated by a timeout or the reception of
duplicate Ack),
One-half of the current window size (the minimum of cwnd and the
receiver's
advertised window, but at least two segments) is saved in ssthresh.
Additionally, if the congestion is indicated by a timeout, cwnd is set to
one segment
(slow start)
When new data is acknowledged by the other end, increase cwnd, but
the way it
increases depends on whether TCP is performing slow start or
congestion avoidance.](https://image.slidesharecdn.com/congestioncontrolavoidance-141210102755-conversion-gate02/85/Congestion-control-avoidance-13-320.jpg)

![Fast Recovery
After fast retransmit sends what
appears to be the missing segment,
congestion avoidance, but not slow
start is performed.
This is the fast recovery algorithm.
It is an improvement that allows
high throughput under moderate
congestion, especially for large
windows. [2]](https://image.slidesharecdn.com/congestioncontrolavoidance-141210102755-conversion-gate02/85/Congestion-control-avoidance-15-320.jpg)
![References
[1] The Great Idea Finder “Fascinating facts about the
invention of the Traffic Light William L. Potts
“http://www.ideafinder.com/history/inventions/trafficlight.ht
m Date Accessed: 10th February 2008
[2] D. E. Commer, “Internetworking with TCP/IP, Volume 1:
Principles, protocols, and Architecture, 2006
[3] W. R. Stevens, “TCP Slow Start, Congestion Avoidance,
Fast Retransmit, and Fast Recovery Algorithms, “RFC 2001,
Jan 1997
[4] D. E. Commer, “Internetworking with TCP/IP, Volume 1:
Principles, protocols, and Architecture, 2006
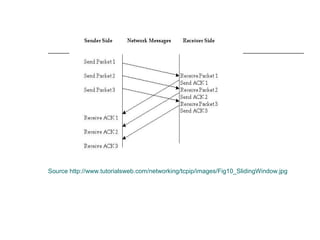
[5] http://www.tutorialsweb.com/networking/tcp-ip/
images/Fig10_SlidingWindow.jpg](https://image.slidesharecdn.com/congestioncontrolavoidance-141210102755-conversion-gate02/85/Congestion-control-avoidance-16-320.jpg)
![References - Continue
[6] V. Jacobson, “Modified TCP congestion
Avoidance Algorithm, “end2end –internet April
30, 1990 ftp://ftp.isi.edu/end2end/end2end-interest-
1990.mail
[7] D. X. Wei C. Jin, S. H. Low, S. Hedge, “FAST
TCP” Motivation, Architecture, Algorithm,
Performance IEEE Network, 2005
[8]http://www.isi.edu/nsnam/DIRECTED_RESEAR
CH/DR_WANIDA/DR/JavisInActionSlowStartFrame
.html Date Accessed 15/02/08
[9]http://www.cs.rice.edu/~amsaha/Papers/Cexa
m/notes/node109.html 15/02/08](https://image.slidesharecdn.com/congestioncontrolavoidance-141210102755-conversion-gate02/85/Congestion-control-avoidance-17-320.jpg)