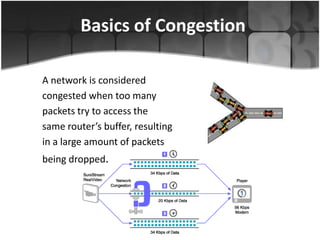
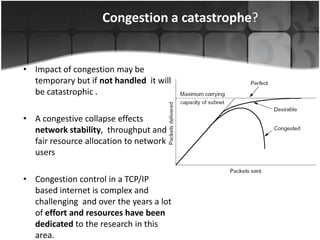
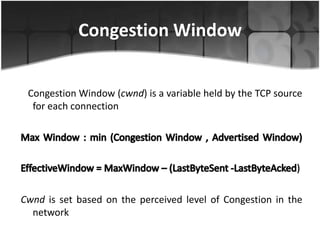
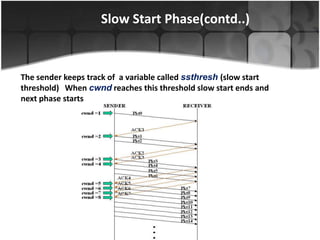
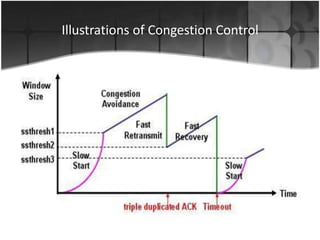
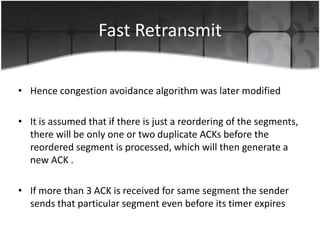
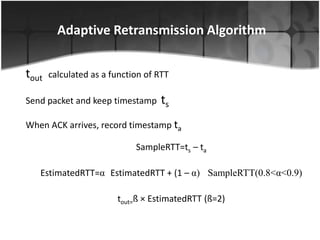
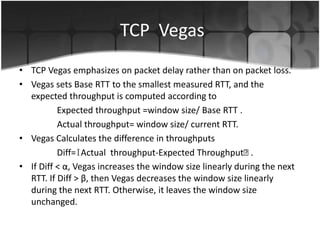
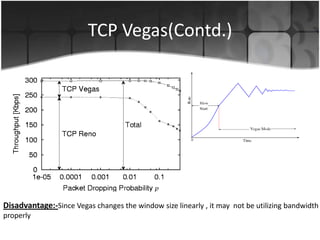
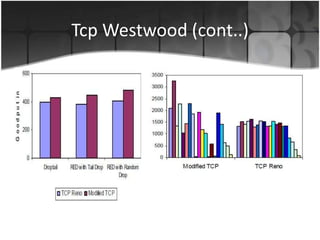
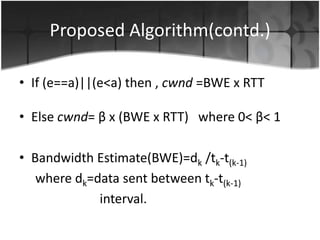
This document summarizes a presentation on congestion control in TCP/IP networks. It discusses basics of congestion and how it can be catastrophic if not handled. It then describes the basic strategies used by TCP to combat congestion, including slow start, congestion avoidance, detection, and illustration of algorithms like fast retransmit and recovery. Issues with wireless networks and variants of TCP like New Reno, Vegas, and Westwood are also summarized. The presentation proposes a new congestion control algorithm and discusses plans to simulate and test it.