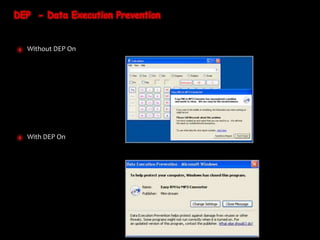
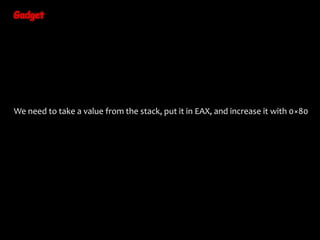
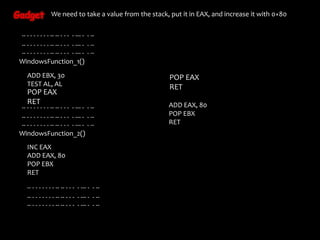
The document discusses return-oriented programming (ROP) exploits, including methods for bypassing exploit mitigation technologies such as Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR). It provides insights into constructing ROP chains using existing executable instructions and highlights strategies for discovering ROP gadgets. Additionally, it outlines necessary Windows API functions to manipulate memory protections to facilitate executing shellcode.