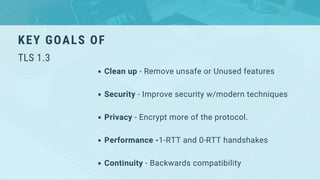
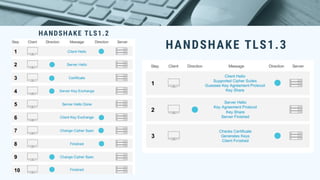
TLS 1.3 is an update to the Transport Layer Security protocol that improves security and privacy. It removes vulnerable optional parts of TLS 1.2 and only supports strong ciphers to implement perfect forward secrecy. The handshake process is also significantly shortened. TLS 1.3 provides security benefits by removing outdated ciphers and privacy benefits by enabling perfect forward secrecy by default, ensuring only endpoints can decrypt traffic even if server keys are compromised in the future.