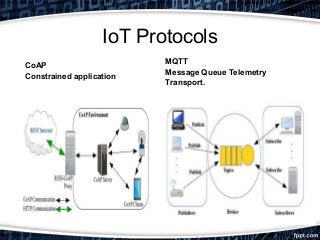
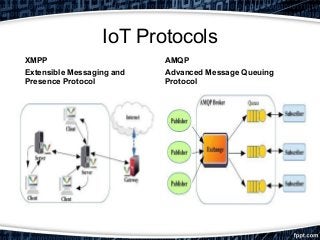
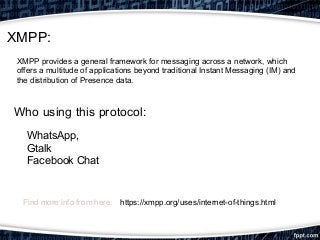
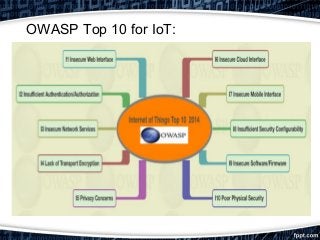
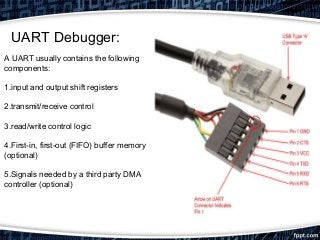
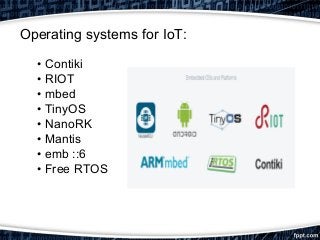
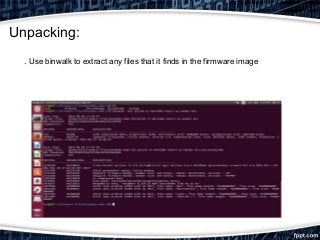
This document provides an overview of exploiting insecure IoT firmware. It begins with an introduction to IoT protocols like CoAP, MQTT, XMPP, and AMQP. It then discusses the OWASP top 10 security risks for IoT, focusing on insecure software/firmware. Common debugging interfaces for firmware like UART, JTAG, SPI, and I2C are explained. Operating systems and compilers used for IoT development are listed. Finally, the document outlines a methodology for exploiting insecure firmware, including getting the firmware, performing reconnaissance, unpacking, localizing points of interest, and then decompiling, compiling, tweaking, fuzzing, or pentesting the firmware. Tools mentioned include binwalk, firmwalk