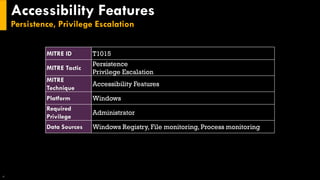
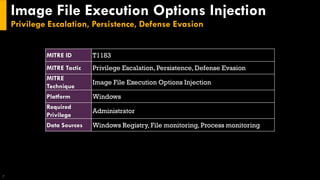
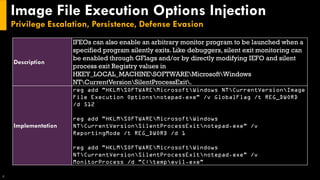
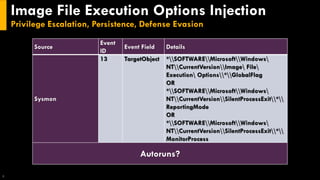
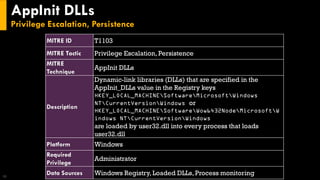
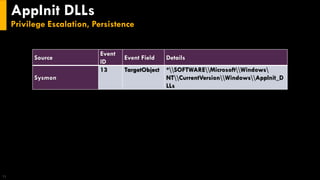
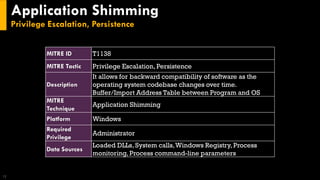
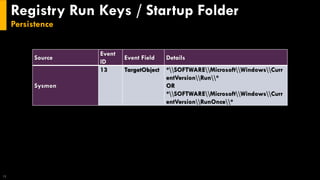
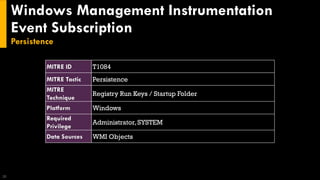
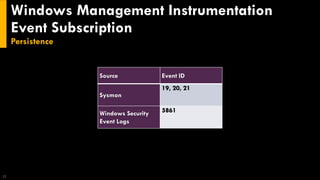
This document discusses several techniques for maintaining persistence on Windows systems, including modifying accessibility features, injecting into image file execution options, using AppInit DLLs, application shimming, BITS jobs, registry run keys, and Windows Management Instrumentation event subscriptions. It provides details on how each technique works, common implementations, required privileges, relevant data sources, and example event log entries.